Root Certificate vs Intermediate Certificate – The Real Difference
You may undoubtedly come across the terms “root certificates” and “intermediate certificates” whenever you get an SSL certificate for your website. After all, it is normal to fail to differentiate the two terms.
So, let’s get started without further delay.
Since the ZIP archive package that you get in an email from the CA contains multiple SSL files, it’s typical for you to be confused for a short while along with the installation procedure if this is your first time installing an SSL/TLS certificate on your own.
Furthermore, the file received by the CA through email includes the server certificate, which is unique to your domain. Conversely, the intermediate certificate connects your server with the CA’s root certificate.
Also, if you’re feeling confused about server certificates, root certificates, intermediate certificates, and the chain of trust, read this article to learn more about them as well as other things like the distinction between root certificates and intermediate certificates and why they’re so crucial for the operation of SSL/TLS.
However, let’s first examine the chain of trust before moving on to the bigger picture.
What is the SSL Chain of Trust?
The SSL chain of trust refers to how it connects to a trusted Certificate Authority. It assists your browser in determining whether to trust the SSL/TLS Certificate that the website you’re currently visiting has installed. It must be possible to track it back to its trusted root, To verify the authenticity of an installed SSL/TLS certificate.
Additionally, the chain’s end-entity, intermediate, and root certificates must all be adequately trusted. The chain of trust is an umbrella term for these three components.
Here is an Illustration of How the Chain of Trust Functions:
It doesn’t matter if you call it the Chain of Trust or The Certificate Chain; they all carry the same concept. The website owners acquired the SSL and CA certificates in this chain.
The certificate’s recipient and sender are reassured of the document’s reliability and legitimacy.
The Features
- The certificate’s issuer information, or the CA that issued it, is included in the chain.
- In contrast to the subject of the subsequent certificate, the present certificate’s issuer is the same.
- A secret key related to the certificate’s position in the hierarchy is used to sign the certificates.
- The CA certificate is the final certificate (trust anchor) and is trusted when it comes from a reputable source.
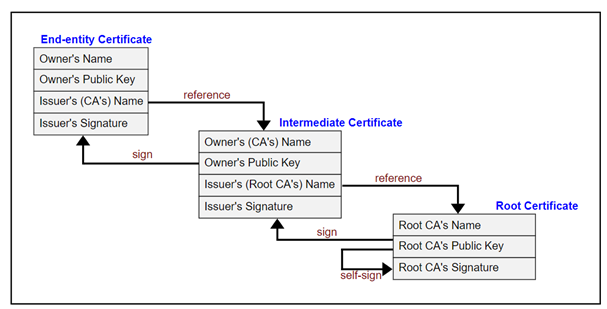
Each certificate chain begins with the root certificate issued by the CA, continues with one or more than one intermediate certificate, and finally comes to an end with the final certificate (also known as the SSL certificate).
What is a Root Certificate?
The root certificate, which is often referred to as a trusted root, is one of the certificates issued by a reliable Certificate Authority (CA), such as Sectigo.
A root certificate is an X.509 digital certificate at the top of the trust chain. It is regarded as the core of Public Key Infrastructure.
Each device has a root store with valid CA signatures. This store also contains their public keys and certificates already downloaded.
When browsers must verify the CA’s dependability, they compare the same from their root store. The browser will alert the user that they are attempting to access an insecure site if the CA name does not match the name listed in their root store.
The additional certificates granted are the followers, and the root certificate is the boss. Consequently, the Certificate Authority could be in danger if the root keys are ever compromised.
As a result, the compromised CA will be removed from the root store and all the certificates it signs will also be revoked. Such disasters can be prevented by keeping the root key in the Hardware Security Module, which is in a secure spot.
The digital key is protected by this physical computer equipment, which also incorporates crypto processing chips to thwart hacker intrusion. Compared to other certificates, root certificates have the longest possible validity duration.
Root certificates are incredible, and their trustworthiness tends to increase when their private key digitally signs them. Each certificate authority maintains different root certificates and characteristics. In the trust store, they are all open to view.
What is an Intermediate Certificate?
Certificate Authorities (CAs) use great vigilance while issuing SSL certificates. They stay away from directly providing server certificates through Roots since doing so is risky and could encourage fraud.
Since roots are significant, having many root CAs is not recommended. Intermediate CAs have been created to protect these roots and address this. By taking on all the responsibilities of root CAs, they acted as an extra security layer.
Due to the inaccessibility of the root CA’s keys, intermediate certificates link the root CA and the last certificate that is issued.
CAs generate intermediate roots and are more trustworthy when signed (with a private key). Following that, CAs sign endpoint SSL certificates using the same private key. After the document has been signed, the owner of the relevant website is finally issued an SSL certificate.
Multiple iterations of the same process are carried out when several intermediate certificates are involved. In this instance, one intermediate root certifies the subsequent intermediate root, and the CA can utilize all of them to sign the final SSL certificate.
Browsers make use of these intermediary certificates to identify root CAs. Additionally, the server certificates are accepted using these certificates as well.
Perhaps it is now clear why the SSL folder also contains an intermediate and primary certificate. These certificates have a longer validity duration than SSL certificates regarding reliability.
Comparing the Difference between Intermediate and Root Certificates
The Public Key Infrastructure (PKI) uses both root certificates and intermediate certificates to generate and validate digital certificates. However, there are certain obvious differences between both.
| Difference | Root Certificate | Intermediate Certificate |
| Outline | A root certificate known as a self-signed digital certificate resides at the top of the PKI’s trust hierarchy. Verifying that a digital certificate was issued by a reliable source, is used to create trust in it. | An intermediate certificate is a digital certificate that can be issued by a root certificate. It serves as an intermediary between the root certificate, and the certificate used by the end user. |
| Certificate granting | Prevent the CA from issuing SSL certificates directly. To prevent breaches, they use intermediate certificates to sign the endpoint (SSL) certificates. | The intermediate certificate acts as a mediator by signing the intermediate certificates, securing the root certificate, and issuing SSL certificates. |
| Expiration | Root certificates are used for a long time and hardly expire. | Compared to root certificates, intermediate certificates often have a shorter length of validity. |
| Maintenance | Trusted Certificate Authorities (CA) provide and maintain root certificates. | The Certificate Authority oversees managing intermediate certificates, which can be changed or renewed as required. |
| Revoke | Root certificates do not need to be revoked if a certificate is revoked for any emergency. | To avoid harm in an emergency, intermediate certifications will be revoked. |
| Significance in the trust chain | In the trust chain, the root certificate is more valuable than an intermediate certificate since it is more valuable. | In the trust chain, the intermediate certificate is of lesser significance. It serves as a middleman. |
| Signature | The root certificate uses its private key to sign the intermediate certificate. | The end-point certificate and any other intermediate certificates, if any, are also signed by the intermediate certificate using the same key. |
| Access | The root certificate is accessed by the Root Store. | The intermediate certificate is accessed through the Private Key. |
Wrap up!
Understanding these critical differences and managing these security certifications is a challenging task. You may be aware now that although both certifications have characteristics and purposes in common, they differ considerably. Root Certificates are maintained offline and never made available to end users to preserve security. In contrast, the intermediate certificate is kept online for signatures, and other intermediate and endpoint certificates are issued.
In simple terms, both certificates are essential to the PKI chain of trust. Its link and trust will be broken in the absence of any. Therefore, be sure to utilize both certificates to secure your systems and digital infrastructure.
We hope you now have a better understanding of what the SSL chain of trust is, how crucial it is for an SSL/TLS certificate to function properly, what the root certificate and intermediate certificate are, and how they differ.
FAQ’s
What distinguishes a root certificate from an intermediate certificate?
While root certificates are self-signed, intermediate certificates are cross-signed. The root CAs are the basis for the certificate chain of trust model. In contrast, the primary goal of the intermediate CAs is to offer an extra layer of protection in the case of any erroneous issuance or online attacks.
Can I Trust the Root Certificate?
A trustworthy certificate authority (CA) is the source of a Root SSL certificate. Anyone can generate a signing key and a new certificate within the SSL environment. However, that certificate is only considered legitimate if a reputable CA has directly or indirectly signed it.
What is the Benefit of an Intermediate Certificate?
The intermediate certificate is a layer of encryption between the end user’s certificate and the certificate issued by the Certificate Authority. It acts as a verification tool that informs a browser that a certificate was issued on the root certificate of the CA, a reliable, trustworthy source.
Do Root Certificates expire?
They are usually valid for 20 years or more. These root certificates are then used to create intermediate certificates at the second level, usually valid for three to six years.
Are Root CA certificates self-signed?
An X. 509-based public key infrastructure (PKI) is built on the foundation of root certificates, which are self-signed (and can have several trust pathways, for example, if the certificate was issued by a root that was cross-signed).
