Kaspersky Experts Discovered a years-old Microsoft Office Vulnerabilities
Security Breach Alert: The Resurfacing of Long-Forgotten Microsoft Office Flaws Triggers an Avalanche of Targeted Onslaught of Attacks on Users and Corporations, Prompts Urgent Response Measures.
Kaspersky’s security experts have raised a red flag as they witnessed an unprecedented 500% surge in the exploitation of a critical vulnerability known as CVE-2017-11882 since the beginning of this year. This alarming trend has significantly harmed thousands of users, making it an urgent concern for individuals and businesses. Another older vulnerability, CVE-2018-0802, has emerged as the favored “attack weapon” among cybercriminals, affecting 130,000 users.
Let’s Unveil Some Problematic Statistics:
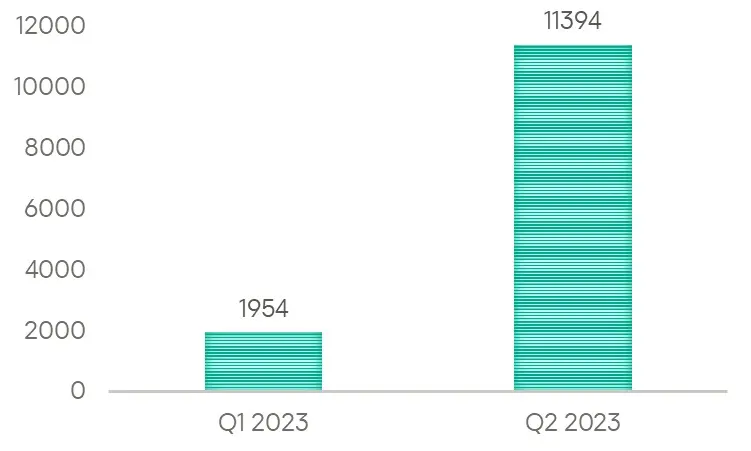
In a recent revelation, Kaspersky researchers discovered a shocking figure of over 11,000 users who fell victim to malicious attacks exploiting the dated security vulnerability in Microsoft Office, namely CVE-2017-11882, during the second quarter of 2023.
This vulnerability allows attackers to exploit the equation editor tool in Microsoft Office documents, providing a gateway to execute harmful code on targeted devices.
Why is it a Constant and Looming Threat?
The persisting threat of cyberattacks on Microsoft software stems from the prevalence of older versions still in use today. Due to their susceptibilities, these older versions have proven desirable targets for attackers. It underscores the importance of proactively implementing reliable security solutions and diligently updating software to safeguard against potential breaches.
Top Vulnerabilities Under Attack:
Several vulnerabilities have emerged as prime targets for exploitation, leaving thousands of users affected:
- CVE-2018-0802: Impacting 130,126 users.
- CVE-2010-2568: Affecting 31,091 users.
- CVE-2017-0199: Compromising 13,537 users.
- CVE-2017-11882: Endangering 11,394 users.
- CVE-2011-0105: Afflicting 10,646 users.
Which is an Effective Attack Vector?
Exploiting the identified vulnerability proves disturbingly simple for attackers – they merely need to distribute a malevolent file to potential victims or create a deceptive website, using social engineering tactics to lure users into opening it.
Despite this vulnerability having been discovered and patched long ago, the second quarter of this year witnessed an alarming 483% surge in its exploitation compared to the previous quarter.
This unsettling trend is a stark reminder that old vulnerabilities can still serve as potent weapons, jeopardizing individual users and corporate infrastructures.’
What is the Need for Vigilance?
As cyber threats evolve, users and businesses must remain vigilant in fortifying their digital defenses. Timely updates, reinforced by reliable security solutions, are vital safeguards against potential security breaches.
Staying informed about emerging vulnerabilities and adopting proactive measures can significantly mitigate risks and protect the digital landscape from harmful exploitation.
List of Proactive Security Recommendations:
Kaspersky’s security experts offer vital recommendations to fortify defenses against threats arising from the exploitation of various vulnerabilities:
Swiftly Install Patches:
To prevent cybercriminals from exploiting newly discovered vulnerabilities, it is crucial to install the necessary patches on all systems and software promptly.
Exercise Caution with Links:
Verify them for authenticity before clicking on any links. Check URL addresses for anomalies, spelling errors, or discrepancies that may indicate potential phishing attempts or fake websites.
Deploy Endpoint Protection and Email Server Security:
Enhance your protection against phishing attacks and email-based threats by implementing robust endpoint protection and email server security solutions.
Employ Comprehensive Detection and Response Solutions:
Adopting comprehensive detection and response solutions is vital for businesses. These solutions gather data from multiple sources, including endpoints, networks, and cloud platforms, to enhance threat detection and response capabilities.
Leverage Specialized Services:
Utilize trusted security services such as Website Vulnerability Scanning, Vulnerability Testing, Vulnerability Assessment, Penetration Testing, App Security and more. These services can identify and halt attacks early, preventing cybercriminals from achieving their malicious objectives.
