Session Hijacking: A Detailed Guide for Safeguarding Your Online Interactions

You must be aware that session hijacking is a particularly insidious hacking technique among the various threats that users and organizations face.
Bad actors can access any ongoing user session online. With the session management mechanism, these assailants can assume the rule of a fair user’s session, potentially gaining access to sensitive information, privileges, and transactions.
This blog covers the intricacies of session hijacking, shedding light on its various aspects, types, examples, and preventive measures.
What is the Session Hijacking?
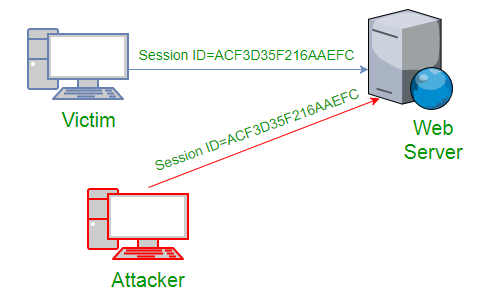
Session hijacking, session takeover, or session stealing is a hacking technique where unauthorized individuals access a legitimate user’s session on a computer system or online account. By exploiting vulnerabilities in the session management mechanism, attackers can take control of the ongoing session, effectively assuming the identity and privileges of the legitimate user.
The process involves seizing control of an ongoing TCP/IP communication session through the execution of illicit actions within a safeguarded network environment.
Conventionally, web sessions are administered via session tokens, virtual keys granting access. The individual executing the session hijack gains full entitlements identical to the genuine user’s.
For instance, online shopping or utility bill payments are susceptible to exploitation by session hijackers, who target web browsers or web application sessions for their attacks.
Types of Session Hijacking
Session hijacking, a perilous hacking technique, manifests in various forms, each with distinct characteristics and methods. Understanding these types is paramount to safeguarding online interactions. Let’s delve into the three primary types of session hijacking and the methods attackers use to compromise digital security.
Active Session Hijacking:
Active Session Hijacking transpires when an attacker assumes control of an ongoing session. In this scenario, the genuine user’s access is suspended as the attacker takes on the authorized user’s role.
Moreover, the attacker can manipulate the communication between the client and the server. By inundating a valid session with excessive traffic, the attacker orchestrates a denial-of-service (DoS) assault, disrupting the communication flow and gaining unwarranted control.
Passive Session Hijacking:
Passive Session Hijacking differentiates itself by its stealthy approach. Instead of assuming control, the attacker clandestinely monitors the interaction between a user and a server. The hacker aims to eavesdrop on data transmissions, recording them for future exploitation. This stolen data is subsequently utilized for unauthorized activities.
This technique resembles a man-in-the-middle attack, where the attacker lurks between the client and server, intercepting sensitive information.
Hybrid Hijacking:
A fusion of Active and Passive Session Hijacking gives rise to Hybrid Hijacking. Here, attackers monitor the network traffic, identifying vulnerabilities that allow them to wrest control of the web session when opportune moments arise.
This dynamic blend of techniques empowers them to exploit weak points in communication channels, seamlessly transitioning between passive monitoring and active manipulation.
Examples of Session Hijacking
Let’s consider a few illustrative examples to learn the severity of session hijacking better.
Imagine an attacker exploiting a vulnerable login page to steal a user’s session token, subsequently gaining unauthorized access to the user’s account.
Another scenario involves intercepting unencrypted communication between a user and a server to steal session cookies, thereby assuming the user’s identity and privileges.
A list few Examples of Session Hijacking:
Session Fixation:
In this scenario, an attacker tricks a user into using a specific session ID. Once the user logs in with that session ID, the attacker can take over the session, as they know the session ID and can predict its value.
Man-in-the-Middle (MITM) Attack:
An attacker intercepts the user and server communication, stealing the session cookie or token. This allows the attacker to impersonate the user’s session.
Cross-Site Scripting (XSS):
Attackers inject malicious scripts into web pages that other users view. These scripts can steal session cookies or tokens from users’ browsers, giving the attackers unauthorized access to their sessions.
Session Sidejacking:
Attackers use packet sniffing tools to capture unencrypted session tokens transmitted over a network. This allows them to gain access to the target user’s session.
Session Replay:
Attackers capture and replay legitimate session data to gain unauthorized access to a system. This technique is effective when the session data isn’t adequately validated or protected against replay attacks.
Session Prediction:
Attackers use various methods to predict or guess session IDs, allowing them to hijack sessions that haven’t been properly secured.
Session Denial-of-Service (DoS):
Attackers flood the target system with multiple requests to exhaust resources, causing legitimate users to be forcefully logged out. The attacker can then take over the vacant sessions.
Browser Extension Exploitation:
Malicious browser extensions can compromise sessions by accessing cookies or injecting scripts to manipulate sessions.
A Case Study in Session Hijacking: The CRIME Attack
Demonstrating the genuine threat posed by session hijacking, the CRIME attack is a concrete example of how vulnerabilities in security protocols can be exploited. This incident, which occurred in September 2012, sheds light on the tangible repercussions of such breaches.
The CRIME attack method hinged on exploiting data leaks within the compression ratio of TLS (Transport Layer Security) requests. This intricate technique allowed the attackers to exploit weaknesses in the encryption protocol. By capitalizing on this vulnerability, the attackers could access users’ login cookies, a digital key granting entry to their active sessions.
The attackers could hijack users ‘ sessions once in possession of these login cookies. The impact of this breach was profound, as it granted unauthorized access to sensitive data and privileged information. The attackers circumvented the established security measures and presented themselves as authenticated users.
The CRIME attack was characterized by its method of decrypting HTTPS cookies set by the targeted website. This decryption was achieved through brute force tactics, where the attackers systematically attempted various combinations to decrypt the cookies. The success of their efforts led to the siphoning of a significant volume of data.
What is Hijacking?
Hijacking, a malicious technique deployed by hackers, engenders complete control over a designated computer system or network connection.
Once seized, the attacker gains unfettered access to the victim’s computer, affording the ability to peruse and manipulate transmitted data and messages. Central to hijacking is the hacker’s covert aspiration: commandeering a computer or network with the intent of pilfering information incognito.
This surreptitious endeavor allows the hacker to remain undetected while systematically extracting valuable data. An illustrative scenario includes a hacker wresting control of a target computer, clandestinely activating its camera to gather sensitive information for espionage purposes surreptitiously.
What are the Types of Hijacking?
Hijacking is a term that encompasses various unauthorized takeover methods across different domains. Here, we highlight several distinct types of hijacking:
Session Hijacking:
This hijacking involves unauthorized access and control over an ongoing user session, often to steal sensitive information or manipulate the session’s content.
Domain Hijacking:
In domain hijacking, cybercriminals illicitly gain control over a domain name by changing its registration information. This can lead to unauthorized access or disruption of online services associated with that domain.
Clipboard Hijacking:
Clipboard hijacking refers to the unauthorized interception of copied data from a user’s clipboard, which attackers can exploit for their gain.
Domain Name System (DNS) Hijacking:
DNS hijacking occurs when attackers manipulate the domain name resolution process, redirecting users to malicious websites or intercepting communications.
Each hijacking type poses unique risks and requires specific security measures to prevent and mitigate their effects.
How Does Session Hijacking Work?
Session hijacking operates by exploiting vulnerabilities in the session management protocols of web applications. Attackers identify weak points in the communication channel between users and servers, intercept session tokens or cookies, and manipulate the session state. Hackers can seamlessly infiltrate ongoing sessions through session fixation, MITM attacks, and XSS.
Hackers deploy various methods to execute the Active, Passive, and Hybrid Session Hijacking variations.
They can choose to employ a single approach or multiple techniques concurrently to maximize their impact. Some standard methods include:
Brute-forcing the Session ID:
Attackers employ exhaustive trial-and-error attempts to guess session IDs to gain unauthorized access
Named for its intuitive approach, this attack involves the attacker guessing and testing Session IDs based on their length. This method thrived due to weak security practices and short session IDs. The introduction of longer, robust session keys has slowed the effectiveness of this method considerably.
Cross-Site Scripting (XSS) or Misdirected Trust:
Hackers compromise user browsers and exploit their trust relationships with servers
In Cross-Site Scripting, hackers exploit vulnerabilities in web servers by injecting malicious code into web pages. This surreptitious code insertion helps attackers locate Session IDs. By leveraging security weaknesses, they infiltrate systems, gaining unauthorized access.
Man-in-the-Browser:
Compromises the user’s browser to manipulate or intercept their web interactions
Utilizing Trojan Horse programs, attackers execute the Man-in-the-Browser attack. They position themselves between the server and the client by inserting malicious code. This manipulation facilitates activities like financial fraud, highlighting the severe consequences of this intrusion.
Malware Infections:
Attackers employ malware to infiltrate systems, giving them access to session data and control over user activities
Attackers resort to deception, luring users to click on links embedded with malware or Trojan programs. These surreptitious programs install malicious software without user consent. This breed of malware discreetly pilfers browser cookies, compromising sensitive data.
Session Fixation:
Coercing users into adopting a predetermined session ID, attackers can exploit the session they’ve set up
In Session Fixation attacks, hackers create an alternate session or deceive users into authenticating vulnerable servers. Employing tactics like misleading emails, attackers prompt users to inadvertently engage with their malicious session, leading to unauthorized access.
Session Side-jacking:
Through packet sniffing techniques, attackers intercept unencrypted session tokens transmitted across networks
Attackers exploit weak points in network security, mainly when users employ insecure Wi-Fi connections. Using packet sniffing techniques, they intercept network traffic, allowing them to seize session cookies stealthily. Packet sniffing involves observing network data flow.
Which is the Most Used Session Hijacking Attack?
Session hijacking, a prevalent cybersecurity concern, can manifest through various techniques. Among these, a prevalent method is IP spoofing, where attackers manipulate source-routed IP packets to inject commands into an ongoing communication between network nodes.
This allows them to assume the identity of an authenticated user and discreetly infiltrate the session.
Session hijacking is broadly categorized into two main types:
- Application Layer Hijacking
- Transport Layer Hijacking
Each type encompasses numerous attack subtypes, affording hackers various tactics to hijack a user’s session.
In the broader context of cyber threats, several common types of attacks routinely compromise systems and data:
Malware:
Malicious software infiltrates systems to disrupt operations, steal data, or gain unauthorized access.
Denial-of-Service (DoS) Attacks:
Attackers overwhelm a system’s resources to render it unavailable, disrupting its normal functioning.
Phishing:
Hackers employ deceptive emails or messages to trick users into divulging sensitive information.
Spoofing:
Attackers falsify their identity or data to gain unauthorized access to systems or manipulate users.
Identity-Based Attacks:
These attacks target vulnerabilities in identity management systems to gain unauthorized access.
Code Injection Attacks:
Attackers inject malicious code into applications to exploit vulnerabilities and gain control over systems.
Supply Chain Attacks:
Hackers infiltrate third-party providers or components to compromise systems higher up the chain.
Insider Threats:
Malicious actions from within an organization, whether by employees or contractors, pose significant risks.
So, how can you get rid of these attacks? Let us find out in the following section!
How to Prevent Session Hijacking?
Defending against session hijacking demands a comprehensive approach that reinforces the security mechanisms within web applications.
By focusing on effective communication and session management, you can significantly mitigate the risk of falling victim to this insidious cyber threat.
Here’s a range of strategies to bolster your defenses:
HTTPS (Hypertext Transfer Protocol Secure):
Embrace the power of HTTPS to establish a secure online environment. Through SSL/TLS encryption, HTTPS safeguards your session traffic. This encryption thwarts attackers from intercepting plaintext session IDs, even if they’re monitoring your activities.
Consider implementing HSTS (HTTP Strict Transport Security) to ensure a consistent and robust encryption layer.
Session Management:
Rely on established web frameworks for session management, avoiding the pitfalls of creating custom systems. These frameworks come fortified with security measures, offering a solid defense against hijacking attempts.
System Updates:
Maintain a strong security posture by installing reputable antivirus software. Such software can detect viruses and shield you from the malware attackers often employ for session hijacking. Ensure that your devices are consistently updated through automatic updates.
HTTPOnly:
Implement the HTTPOnly attribute to thwart client-side script access to stored cookies. By doing so, you impede attackers from executing cross-site scripting (XSS) attacks that rely on injecting malicious scripts into browsers.
Session Key Regeneration:
Strengthen your defense by regenerating session keys post-initial authentication. This renders attackers’ extracted session IDs obsolete, as the ID is transformed immediately after authentication.
VPN (Virtual Private Network):
Leverage the protective shield of a VPN to ward off session hijackers. A VPN obscures your IP address and enhances your session security by creating an encrypted “private tunnel” for your online activities.
Identity Verification:
Amplify security by subjecting users to additional identity verification beyond the session key. This includes scrutinizing customary IP addresses and application usage patterns.
Phishing Scam Vigilance:
Guard against phishing attacks by meticulously verifying the authenticity of emails before clicking on any embedded links. Only engage with links that emanate from verified and legitimate senders.
Public Hotspot Caution:
Exercise prudence when connecting to public WiFi networks. Opt for secure wireless networks to ensure the sanctity of your sessions, shielding your interactions from potential attackers.
By conscientiously implementing these strategies, you heighten your security and contribute to the broader mission of establishing a safer digital landscape for all users.
The Role of Encryption in Securing Against Session Hijacking
Preserving the integrity of user sessions against the looming threat of hijacking is a paramount concern for organizations. One practical approach to fortify defenses involves the integration of robust encryption techniques. These encryption methods, presented as certificates, are vital in safeguarding users’ interactions and data.
SSL (Secure Sockets Layer):
SSL, which stands for Secure Sockets Layer, is the bedrock technology for upholding secure internet connections. It establishes a shield around the communication channel between two systems, effectively shielding sensitive data from interception and tampering.
Organizations use SSL to prevent malicious actors from surreptitiously accessing and altering transmitted information, including potentially sensitive personal data.
TLS (Transport Layer Security):
TLS, an evolution from SSL, represents a more advanced and secure iteration. Also known as Transport Layer Security, TLS offers enhanced safeguards against threats.
Like its predecessor, TLS ensures the confidentiality and integrity of data exchanged between systems, providing a comprehensive defense against session hijacking attempts.
Wrapping up
Comprehending the multifaceted nature of session hijacking and the tactics attackers employ empowers users and organizations to bolster their defenses. Implementing robust security benchmarks, such as encryption, regular session expirations, and vigilant software updates, is essential in the ongoing battle against this pervasive threat.
As technology advances, so do the techniques of malicious actors. Session hijacking poses a significant threat to the security and privacy of online users.
By understanding its types, methods, and preventive measures, individuals and organizations can fortify their defenses against this pervasive hacking technique, ensuring safer and more secure online experiences.
Protect your Organization and assets against cyber threats, malwares and attacks with End-to-End Cyber Security Services.
Browse Cyber Security Solutions and Services
