What is a .Pem File? How does it Differ? How to Create and Open it?

Regular website owners recently recognized the significance of an SSL/TLS certificate because of years of push from the browser and security community.
Consequently, most website owners get an SSL certificate when their website is developed. However, many need to become more familiar with this topic and could become frustrated by some intricacies of the cybersecurity industry.
The PEM certificate file could be one of these issues. Therefore, we’ll discuss the PEM certificate file in this blog.
PEM is a container file format frequently used for storing cryptographic keys. It specifies the File’s structure and encoding type; However, it can be used for various applications.
This blog majorly outlines what a PEM file is, what is .pem, the purpose of PEM files, and what is PEM format is.
What Exactly Is a PEM File?
Let us tell you something first before we answer this query. Your certificate authority must provide you with the security certificate you purchased (usually an SSL certificate), which is just a collection of files containing the private Key, the intermediate certificate, and the CA server certificate.
These files are typically delivered by email, encoded in a single file or “container” as some refer to it. One such file type is a PEM (Privacy-Enhanced Mail) container.
A PEM file is abbreviated as a Privacy Enhanced Mail Certificate file that is used to send emails confidentially. The person receiving this email can ensure that it hadn’t been modified in transit, was not viewed by anyone else, and was sent by the person specified as the sender.
The difficulty of delivering binary data over email gave rise to PEM files. Using base64 encoding, the PEM format converts binary into an ASCII string.
The PEM container is still used today to store certificate authority files, public and private keys, root certificates, etc., even though newer, more secure technologies have substituted the PEM format.
What is the PEM file format?
PEM is a container format used primarily by Apache and other web server systems to store digital certificates and keys. In simple terms, it’s the file extension of a file that contains several certificate files.
For X.509 certificates, a text file called a PEM file is frequently used. It has a plain-text header and footer that indicate the certificate’s beginning and ends (For example, —BEGIN CERTIFICATE and —– END CERTIFICATE), as well as the certificate’s text encoded in Base64.
Note: Instead, specific PEM files could come with a different file extension, such as KEY for public or private keys or CER or CRT for certificates.
How to Create a PEM Certificate File?
Some servers can be demanding for PEM files. You have no choice but to comply with your server’s request for a PEM file if it is to be one of them. You shouldn’t worry because making a PEM certificate file is easy as a pie. To accomplish it, take the following steps:
Download the private Key, root, main, and intermediate certificate files your certificate authority provided you first.
Now, open a text editor ( Notepad) and paste the entire contents of every certificate and its private Key in the following order:
- The Private/Secret Key
- The Primary Certificate
- The Intermediate Certificate
- The Root Certificate
- Add the beginning and ending tags.
- The File should then be saved with a .pem extension, e.g., your_domainname.pem.
- Congrats! A PEM certificate file was just successfully generated by you. It was as easy as pie.
What is the Purpose of PEM File?
PEM files hold certificates and cryptographic keys. These files are used on apps, websites, and servers to share data and authenticate users securely. Private keys, digital certificates from certifying authorities, and SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates are all frequently found in PEM files.
PEM files are frequently used to create secure connections and encrypt data in various web-based applications, VPN connections, email clients, and web servers.
Digital signatures can additionally be created using PEM files. A document is signed using the private Key, and the associated public Key is kept in a PEM file. The signature can subsequently be verified, and the document’s authenticity can be confirmed by anybody using the public Key.
PEM files are helpful in many scenarios. For instance, they may be used to protect client-server communication. For example, a web server could use a PEM file to verify its identity to a client browser. Using the public Key present in the PEM file, the browser could subsequently encrypt data transferred to the server.
How to Open PEM Files?
Depending on the application that uses it and the operating system you’re running, there are many ways to access a PEM file. To make your PEM file compatible with some of these applications, you might need to convert it to a CER or CRT format.
Windows
Launch Microsoft Management Console from the Run dialogue box (type mmc using the Windows Key + R keyboard shortcut).
This will allow you to import a CER or CRT File into Windows. Select Certificates from the left column under File> Add/Remove Snap-in…, then click the Add > button in the window’s center.
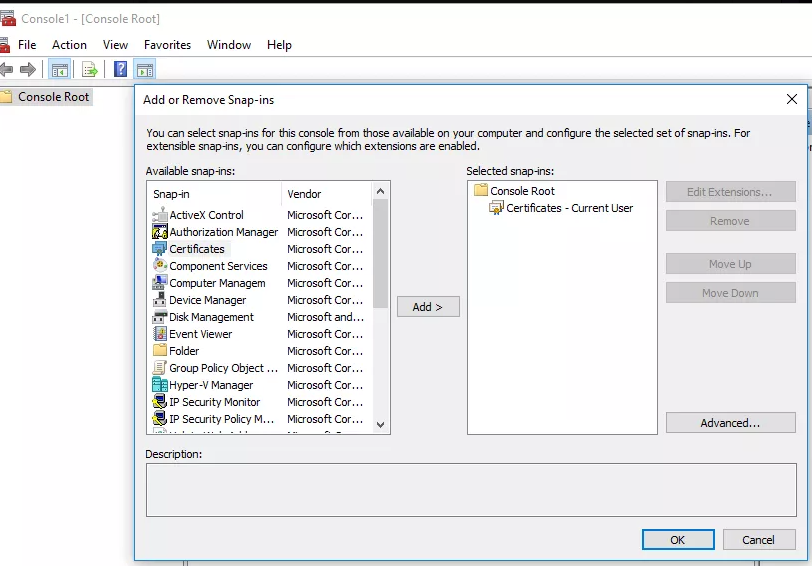
When prompted, select Local computer in the wizard after selecting Computer account on the following screen.
Expand the Trusted Root Certification Authorities folder once “Certificates” has loaded under “Console Root,” then select All Tasks > Import from the context menu.
macOS
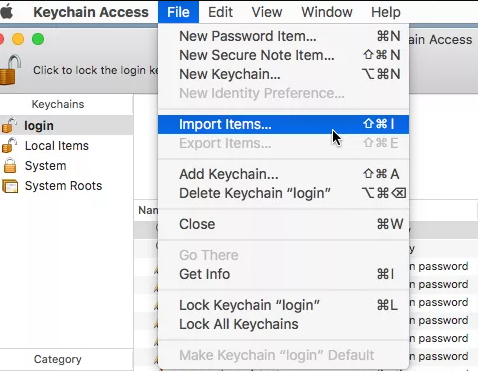
Use Safari to get the PEM file imported into Keychain Access. This method works for both your Mac and Windows email clients.
Additionally, you can import SSL certificates using Keychain Access‘ File > Import Items menu. From the drop-down option, select System, and then follow the on-screen instructions.
Try the following command (changing “yourfile. pem” to reflect the name and location of your PEM file) if none of the methods have been successful in importing the PEM file into macOS:
Security import your File. pem -k
~/Library/Keychains/login.keychainAdditional Information about PEM
- The data confidentiality and integrity feature of the Privacy Enhanced Mail Certificate format checks a message’s before- and after-sending message digests using RSA-MD2 and RSA-MD5 to ensure that it hasn’t been tampered with in transit.
- A PEM file starts with a header that reads —–BEGIN [label]—– and ends with a footer that is similar but reads: —–END [label]—-. It may say PRIVATE KEY, CERTIFICATE, or CERTIFICATE REQUEST in the “[label]” part, which describes the message.
- It’s simple to create and utilize PEM files. They could be created with several tools, such as Microsoft’s IIS Manager and OpenSSL. PEM files can be converted to other forms, including the binary Windows format PFX.
- For storing and exchanging security certificates and keys, PEM files are a prevalent file format. They have the first letter of the three people who developed the format—Phil Karn, Eric Young, and Tim Hudson—who gave it its name.
- Since the format was initially intended for encrypted email communication, PEM stands for Privacy Enhanced Mail.
Wrap up!
In conclusion, PEM files are essential security certificates and critical formats. They offer a quick and simple method for securing private information and ensuring online security. PEM files are often used and supported by most web servers, email servers, and other security software.
FAQ’s
What is the PEM Format Key?
Public Key Infrastructure (PKI) files, known as Privacy Enhanced Mail (PEM) files, are used for keys and certificates. Initially created to protect email, PEM is now a standard for Internet security.
How to Check the PEM Format?
You can use the instructions below to see if your files are already in the necessary format.
Verify that your Key is in PEM format by checking:
openssl rsa -inform PEM -in /tmp/ssl. KeyUse the command to determine if your certificate is in PEM format:
openssl x509 -inform PEM -in /tmp/certificate.crtWhat is a PEM File Example?
The public certificate alone or the entire certificate chain (Private Key, Public Key, root certificates) may be included in a.pem file: Personal Key. Certificate for the server (crt, Public Key)
Exactly How can I Create a PEM File?
You must download the certificates your certificate authority issued before creating a PEM file. This will comprise private vital files, a root certificate, a primary certificate, and an intermediate certificate.
The body of each certificate should then be pasted into a brand-new text file after using a text editor like WordPad or Notepad. The following should come first: Root Certificate, Primary Certificate, Intermediate Certificate, and Private Key. Add the beginning and ending tags. They’ll display as follows:
—–Start the certificate —– and End of Certificate —–
Why is a PEM File used?
PEM, or Privacy Enhanced Mail, is a DER certificate that has been Base64 encoded. Because PEM certificates can be quickly converted into readable data using a basic text editor, so they are often employed for web servers.
A PEM-encoded file often has self-explanatory headers and footers in a text editor.
