What is Code Signing Time Stamping?

A paramount concern for both developers and users is the authentication of software. Code signing is crucial to establishing trust and confidence in software entities such as files, documents, executables, and software.
By affixing a digital signature, code signing guarantees the genuineness of the software and safeguards against any unauthorized tampering during transit.
This article explores the significance of code signing in the modern era, highlighting its role in fostering trust among users, mitigating warning messages, and bolstering overall software security. Join us on a journey into the world of code signing, where authenticity and peace of mind converge.
How Time Stamping Preserves the Integrity of Code Signing Signatures?
The validity and trustworthiness of software is of utmost importance. Time stamping allows the software to recognize and validate digital signatures, even after a code signing certificate expires. It protects the integrity of the signature applied to the software.
The operating system verifies the digital signature when a user executes a signed software executable on their machine. However, by incorporating time stamping, the process takes on an added layer of reliability.
Instead of solely relying on the system’s current time during execution, the user’s computer verifies the signature based on the time it was digitally signed. This means the software’s signature remains valid and trustworthy even if the code signing certificate has expired.
How is Time Stamping Crucial Today?
The significance of time stamping lies in its ability to combat the challenges posed by certificate expiration. Certificates used for code signing have a finite lifespan, typically one to three years.
Once a certificate expires, operating systems and security measures may treat software as untrusted or potentially malicious. Developers can ensure their software retains integrity and authenticity, regardless of the certificate’s expiration.
Furthermore, time stamping is a valuable ally in scenarios where code signing certificates must be revoked or replaced. In such cases, having a time-stamped signature allows users to continue trusting the software, even if the certificate is no longer valid or has been compromised.
This instills confidence in the end-users and mitigates the potential disruption that can occur due to certificate-related issues.
Role Time Stamping Server in the Code Signing Process:
A time stamping server plays a crucial role in the code signing process. When you sign and time stamp your software package, the hash of the package is uploaded to the time stamp server. The timestamp server then performs the following actions:
- The timestamp server records the exact date and time when the signature was applied to the software package. This information is vital for establishing a verifiable timeline and aids in compliance, auditing, and legal requirements.
- The timestamp server verifies and certifies that the software certificate used for signing is valid at the time of signing. This step ensures the software package was signed using a valid and trusted certificate.
- After signing the information, the time stamp server returns a timestamp to be attached to the file. This timestamp includes the digitally signed information, verifying the time stamp’s validity.
- Using its private key, the time stamp server signs the gathered information, including the software package’s hash, the certificate’s validity, and the signature’s date and time. This cryptographic signing process ensures the integrity and authenticity of the time stamp information.
Measures to Fortify Trust and Security with Code Signing
When it comes to code sign time stamping, following best practices can significantly enhance the effectiveness and reliability of the process. Adopting these practices allows you to streamline your software development lifecycle and ensure a smooth experience for developers and end-users. Let’s explore the recommended practices for code sign time stamping:
Incorporate Time Stamping into Your Development Process:
Integrate time stamping as a standard practice in your software development lifecycle. Doing so can avoid any unforeseen issues caused by version mismatches or inconsistencies. Consider time stamping as an essential step to maintain the integrity and authenticity of your software throughout its lifecycle.
Enable Time Stamping:
Enabling the time stamping option in your chosen signing tool, such as Microsoft Signtool, is crucial. Additionally, when selecting a signing tool, verify that it supports the time stamping feature, as it may be optional by default. Enabling time stamping adds a layer of trust and ensures the long-term validity of code signatures.
Benefit from Revocation:
Time stamping plays a vital role in enabling the revocation of code signing certificates if necessary, such as in the event of private key compromise. With time stamping, clients can still verify the authenticity of the software, even if the code signing certificate is revoked.
This feature provides flexibility and reassurance for developers and users, allowing for necessary security measures without disrupting the software installation process.
Document the Time Stamping Process:
Document the complete process of applying time stamps using your signing tool. As different tools may have varying workflows for time stamping, having a comprehensive document will serve as a reference for all stakeholders involved in the code signing process.
Distribute this document to ensure that everyone follows the correct procedures consistently.
Adhering to these best approaches can optimize your code sign time stamping process and ensure the software’s seamless verification and revocation.
Enabling time stamping, integrating it into your development process, documenting the workflow, and leveraging revocation benefits enhance your code signing efforts’ overall security and reliability.
Understanding the Technology Behind Code Signing Time Stamping
Let’s look closely at the technology employed in code signing time stamping to ensure reliable and verifiable time stamps.
Certified Time Stamp Authority (TSA):
A certified Time Stamp Authority (TSA) is employed to provide verifiable time stamps. The TSA operates using PKI principles and technologies. This authority utilizes encryption and decryption techniques to generate time stamps that various entities can validate and trust.
PKI (Public Key Infrastructure) Technology:
Public Key Infrastructure (PKI) technology forms the foundation of code signing time stamping. PKI involves cryptographic techniques that enable secure communication, authentication, and data integrity. PKI ensures only authorized entities can generate and validate time stamps by utilizing public and private key pairs.
Verification and Signing Process:
During code signing, time stamping is applied to verify the date and time the program was signed. The time stamping server facilitates this verification process, typically accessed via a URL.
Certification Authorities (CAs) like Sectigo and DigiCert maintain their servers, which customers can use to apply timestamps to their signed software.
The time stamping server receives the signed program and generates a verifiable time stamp. It includes information such as the precise date and time of the signing event.
By using encryption techniques, the server ensures the integrity and authenticity of the time stamp, making it tamper-proof and resistant to forgery.
Perks of Code Signing Time Stamping:
Code signing time stamping offers several benefits to software developers and users. Firstly, it enables the verification of the signing date and time, providing evidence of when the software was signed. This information is valuable in ensuring compliance, auditing, and legal purposes.
Furthermore, time stamping enhances the longevity and trustworthiness of code signatures. Even if a code signing certificate expires or is revoked, the time stamp validates the software’s integrity at the time of signing. This feature prevents warning messages and allows users to trust the software without a valid certificate.
The Process to Ensure Accuracy and Validity with PKI Technology
Time stamping is vital to maintain the accuracy and validity of software signatures. This process is facilitated by a Time Stamp Authority (TSA), which operates based on Public Key Infrastructure (PKI) principles and technology.
Let’s delve into the steps involved in time stamping software and how it contributes to establishing trust and reliability.
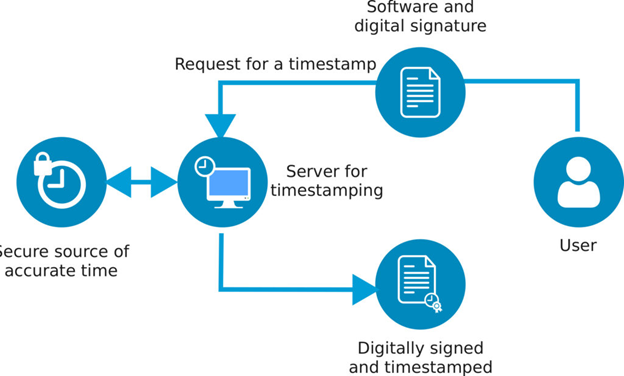
Creation of Hashed Value:
The time stamping process begins with the requester creating a hashed value for the software that requires a timestamp. This hashed value represents a unique digital fingerprint of the software, providing a concise and secure representation of its contents.
Sending the Hashed Value to TSA:
The requester transmits the hashed value to the Time Stamp Authority (TSA). This communication typically occurs over a secure channel to ensure the integrity and confidentiality of the data. The requester seeks to associate a trusted timestamp with the software by sending the hashed value to the TSA.
Generating a New Hash Value:
Upon receiving the hashed value, the TSA combines it with authoritative time information, such as the date and time of the digital signature. The TSA’s private key then signs this amalgamation and other relevant data to create a new hash value. This process ensures the authenticity and integrity of the timestamp generated by the TSA.
Bundling and Transmission:
The newly generated hash value and the original software’s hash value are bundled and sent back to the requester. This bundle contains the necessary information to verify and link the timestamp to the specific software.
Verification and Embedding:
The requester’s application receives the bundle from the TSA and proceeds with the verification process. By comparing the original software’s hash value with the bundled information, the requester can confirm the validity of the timestamp.
Once the verification is completed, the timestamp is deemed valid and becomes embedded within the code signature of the software.
Developers and users can benefit from increased confidence in software signatures by incorporating time stamping into the code signing process. The use of PKI principles and technology ensures the secure application of timestamps by the Time Stamp Authority.
With each step carefully executed, time stamping adds an extra layer of trust, allowing users to rely on the accuracy and reliability of code signatures, even after the original signing event.
Buy or Renew your Code Signing Certificate Starting at Just $199.99/Year
