Code Signing Certificate vs SSL Certificate: Difference
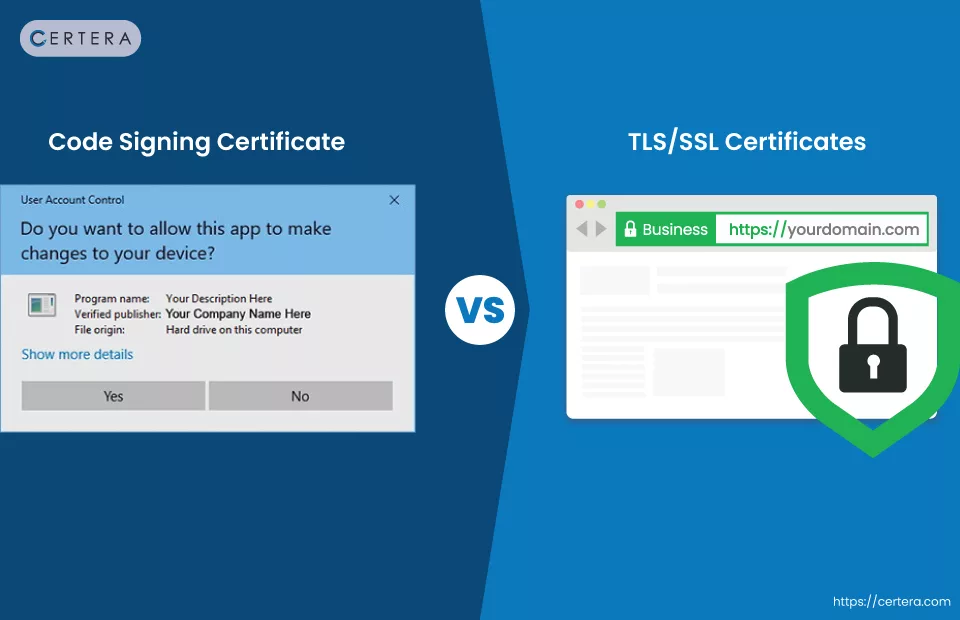
When protecting their web presence, most individuals need clarification on the difference between SSL and code signing certificates and wonder if they can be used interchangeably. The answer is NO.
Although both code signing and SSL/TLS certificates use public-key encryption, there are notable differences between the two. The critical difference between the two is that although SSL certificates ensure website security, code-signing certificates are committed to protecting software code integrity.
Let’s discuss code signing certificates with TLS/SSL certificates in more detail.
What is a Code Signing Certificate?
Code Signing Certificates are created when you need to sign executable files, drivers, software, scripts, and drivers. The verified publisher’s name is displayed when a user downloads software, and the code has stayed the same since it was signed.
If the code is not signed, the user will see a warning notice while downloading the software. if the code is not properly signed, the system/software will send a warning similar to the one shown in the following image:
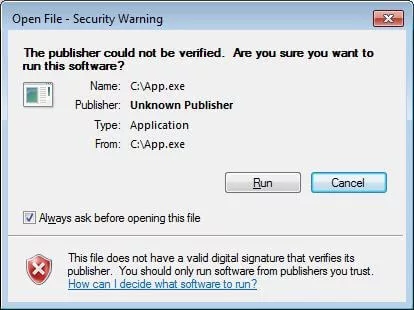
Users are becoming more concerned about internet security since malicious or unauthorized software can compromise systems. As a result, people are increasingly searching for secure downloads from trustworthy publishers.
Code signing certificate fulfills two significant objectives:
Validation: It shows evidence that a confirmed trustworthy publisher created the code.
Code Integrity: A code signing certificate prevents any third party from changing or tampering with the code that powers software or an application.
How Code Signing Certificate Works?
- You must first apply for the code signing certificate with a trustworthy CA, such as Certera, one of the Best SSL Certificate Providers.
- CA confirms your identification. The verification procedure varies depending on the company or individual. The CA generates the software’s public and private keys. The private key signs the code or data, whereas the public key validates signatures. The CA then issues the certificate after the verification procedure.
- It is at this point that you create a one-way hash using your private key and encryption methods, add a digital signature to your code, and then finish:
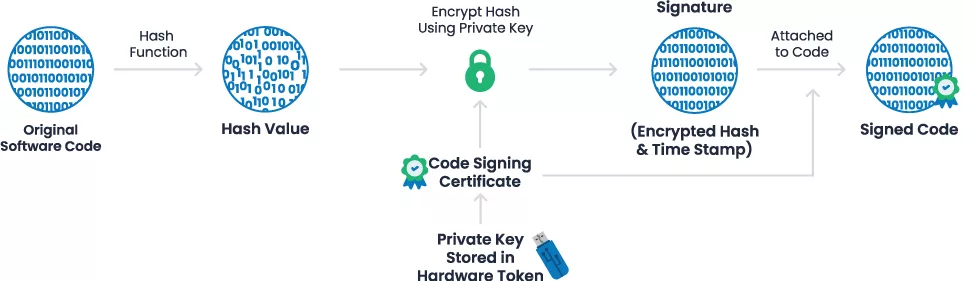
It is recommended to include a timestamp in your signature since it notifies the system that decodes your signature that the code was signed during the period when the code signing certificate was valid.
Your signed software or code is ready to be sent to potential consumers. Your code signature will be seen when a customer downloads the application.
What is an SSL Certificate?
The SSL certificate encrypts all communication between the user’s browser and the server. The data between the two systems remains secure since a third party cannot intercept it.
The certificate verifies a company’s identification in some SSL certificate kinds, such as EV SSL and Organization Validation certificates. The phone number, physical address of the company, and information regarding government registration are all part of the identification verification.
Types of SSL Certificates
You may have three options when choosing an SSL certificate to purchase:
- Domain Validation SSL Certificate: It refers to the domain name’s authorization and does not include owner information in the certificate.
- Organization Validation SSL Certificate: Since a client can see an organization’s information in the certificate, the organization validates both domain ownership and the organization’s identity.
- Extended Validation SSL Certificate: This certificate contains the most significant level of validation and features a green address bar that can reassure clients and visitors about the security of their online credentials. Before issuing a certificate, business-related documents and third-party phone directory verification are required.
How Does SSL Certificate Work?
- The web browser and server use the SSL/TLS handshake mechanism to ensure an encrypted secure connection whenever a visitor accesses a website.
- The legitimate server replies with a TLS/SSL certificate and public key to the browser after receiving a request from the browser.
- The browser examines the certificate and determines it comes from a trustworthy certificate authority, such as Certera. The symmetric session key is then sent to the server.
- To begin the communication, the server encrypts the key with its private key and provides an acknowledgment in the encrypted format.
- The encrypted communication between the browser and server, which guarantees message integrity, privacy, and server security, can now be initiated.
Difference between SSL Certificate and Code Signing Certificate:
| S.No | SSL/TLS certificate | Code Signing Certificate |
| 1 | SSL/TLS certificate is for websites | The code signing certificate covers downloadable scripts, programs, and executables. |
| 2 | Certera, Sectigo, Thawte, DigiCert are renowned certificate authorities. | Certera, Sectigo, and DigiCert are well-known certificate authorities. |
| 3 | Domain Validation (DV), Organisation Validation (OV), and Extended Validation (EV) are considered validation types. | Standard Validation and Extended Validation are two different methods of validation. |
| 4 | Communication between two devices (a browser and a server) is encrypted. | It does not encrypt the code but rather hashes the scripts and publisher signature. |
| 5 | The website will lose encryption if the certificate expires. Until the certificate is renewed, a warning notice will be displayed on the web browser. | The system will display a security warning while downloading software if the certificate expires and will do so until it is renewed. |
| 6 | Starts at $3.99/Year | Starts at $199.99/Year |
- While an SSL certificate secures a website where users enter their login or payment information, a code signing certificate is utilized to sign software code.
- Nowadays, compared to code signing certificates, an SSL certificate is significantly cheaper. Certificates for domain validation are simply and affordably accessible on the market.
- Continuous data exchanged between a server and an SSL certificate encrypts a user’s browser to prevent data eavesdropping by third parties. Despite not encrypting the data, a code signing certificate with hash signs software, drivers, and executables. A software program is sealed off with a hash.
- The timestamping feature of SSL certificates is another difference between SSL and code signing; when an SSL certificate expires, the browser displays a warning until it is renewed. Even the certificate expires, despite the timestamping that a developer applies to Code Signing to keep the digital signature active.
- Owners of websites use SSL certificates, whereas developers use code signing certificates to sign their code.
- Regarding warranties, most certificate providers issue them SSL certificates, but only a few reputed organizations do so for code-signing certificates.
- While an SSL certificate maintains the security of online transactions between a server and a user’s browser, a code-signing certificate reassures users of the integrity of the code.
- Platforms, including Adobe AIR, Microsoft Authenticode, Mac, Microsoft Office and VBA, Sun Java, Silverlight, Windows 8/10, and Mozilla, are served through code signing certificates, whereas SSL certificates protect domain names.
Wrap up!
Users nowadays are aware that visiting unsecured websites or downloading unauthorized software might lead to system infiltration. Therefore, it is essential to use secure communication and secure downloading from reliable sources.
The comparisons provided above that highlight the distinctions between code-signing certificates and SSL certificates highlight the importance of each certificate in its unique way.
