eIDAS 2.0: Future of Digital Identity for Better Web Security

eIDAS 2.0 – What’s New?
The eIDAS 2.0 aims at amending the old eIDAS Regulation of 2014, providing solutions to the identified gaps and also pointing to new features such as trust services and the ID wallet.
The European Commission presented a draft on the revision of eIDAS Regulation in June 2021 and it is better known as eIDAS 2021 or eIDAS 2.0.
- Cooperation in making improvements to the current version of the regulation.
- Introducing more trust services such as electronically signed mails and digital certificates for authentication.
- Implementing the digital eID wallet, being the common digital proof of identity throughout the European Union.
The European Commission must assess the eIDAS regulation within its effectiveness and present it to the European Parliament and the Council no later than 1st July 2020. This evaluation aims at finding out if the regulation is effective, efficient, relevant, and consistent with other policies, and to what extent European integration is being implemented.
The concluding report, released in October 2020, appraises the effectiveness of the regulation so far, pinpointing the existing shortcomings and highlighting areas that need further enhancement. It is about the need for some radical modifications to properly suit the private sector identification needs.
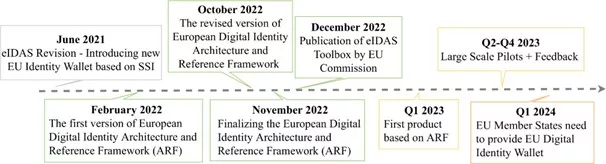
Although the development of the 2.0 version of eIDAS began in 2018, at present the proposal is at the deliberation stage of the Council of Ministers. Initially proposed for implementation in the second half of 2023, the law may be delayed until 2024 as a result of the legislative process’s complexity and the need for adequate stakeholder input.
What will eIDAS 2.0 Change?
The eIDAS Regulation has gone through substantial changes during its 2012 inception that included transformations in societal trust service frameworks. The growth of online services, supported by the quarantines caused by the pandemic, dynamism in behavior, and the internet, emphasized the demand for a new framework.
The next step eIDAS “2.0” intends to cover even newer electronic trust services and additionally stresses the need for more standardization, especially in the area of technical and operational requirements of trust service providers.
A key incentive for eIDAS 2.0 is based on the unsuccessful performance of the objectives of the original regulation.
It is quite interesting that only 60% of the citizens of the EU have a reliable identification system, with the acceptance rates being even lower. Therefore, national service and infrastructure cooperation and interoperability are still not enough.
Hence, it was necessary to bring the law into line with emerging identification methods to enhance the creation of inter-community trust service modules and to facilitate the implementation of innovation and scientific projects.
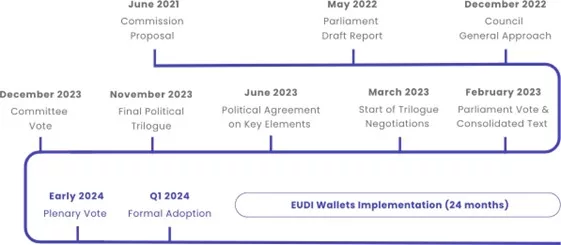
The generally accepted aim of eIDAS 2.0 is to harmonize and standardize implementation in EU Member States, reducing differences and preventing interpretational variations when compared to the first eIDAS adoption.
In addition to that it creates new infrastructure and includes new electronic trust service categories such as electronic proof-of-delivery, electronic seals, and qualified electronic archiving which was not predicted before.
Besides, eIDAS 2.0 has introduced the European Digital Identity Wallet (DIW), this platform makes identity management easier to handle. This DIW makes both online and offline identification in the EU possible, for public or private services and assists the end user in exercising control over information sharing securely.
Regulation-embedded requirements will be kept via the inclusion of robust security measures that will be verified and certified by designated public or private entities.
For example, the design of “zero-knowledge proofs” refers to the existing cryptographic techniques by letting parties show that they have a certain piece of information without divulging it and guaranteeing that their statements are true. The last W-eIDAS 2.0
A regulation draft version has been cleared for public access on June 3, 2021, which will be hosted on the official website from September 2023. Therefore, the citizens will get to have the Digital Identity (DID) Folder from that date on.
eIDAS 2.0 and Digital Identity
eIDAS 2.0 is a new version of digital identity within the European Union that focuses on enhancing the security and reliability of online identity while meeting the increasing demands for such.
The ensuing update of the eIDAS Regulation is developed based on its original concept of 2014 with several strategic improvements and new features that will make the EU digital identity foundations stronger.
The European Digital Identity Wallet (DIW) is one of the matters the eIDAS 2.0 is built around. DIW is the centralized repository where individuals can store and perform management of their digital identity credentials including their electronic signatures, authentication certificates, and other trust services.
By integrating the different credentials onto a secure and single platform, the DIW will offer users a simplified and efficient way of verifying their identity online.
What is more, the DIW will be interoperable across the EU member states thereby ensuring smooth authentication and access to the digital services across the member states. This interoperability is vital for allowing EU citizens to use their digital identities in different countries, enabling the citizens to move more freely and provide access to online services.
Also, apart from DIW, eIDAS 2.0 has provisions that are targeted to increase the overall level of security as well as reliability of digital identity solutions. The regulation shall introduce tougher demands for the issuance and verification of digital identity credentials aiming at the preservation of their integrity and authenticity. These work against identity fraud and misuse such as strong authentication and verification identification processes.
The European Identity Card, an important key component of eIDAS 2.0, is a tool that promotes and adopts electronic identification and trust services in the European Union. Besides, the Union is shifting its approach to more data sovereignty, too. Lastly, this also reflects the objectives of personal data protection by returning power to users with regards to the management and sharing of their personal information.
In 2030, it is expected that over 80% of Europeans will use digital wallet identifiers. From now on, there is no longer a physical boundary between digital identity and the reality of our daily lives, but digital identity has begun to be involved in all aspects of our daily life. Thus, the digital state will carry on its evolution, introducing the systems that combine public infrastructures.
The future for businesses and trust service providers, however, is bright, since the market is projected to show a steady growth rate of 19% out of the current year until 2028 according to a Marketsandmarkets study.
In addition, the digital wallet will be common in our everyday life and it will change the way we do payments and soon it can change our habits in all areas of our life. Faster border crossing, notarized signatures, and financial transactions in three clicks will be the future we will have if we strengthen a powerful digital identity.
For these tendencies, the quality of user experience and the security of personal data will remain the basis of the usage of such solutions.
On the one hand, the future seems to lead to the unification of the identification services but on the other hand, the path to it is still full of traps. However, the European players have a tendency to provide their services harmonized under eIDAS 2.0, while the task of interoperability and standardization is still an uphill battle.
In addition, the focus on building up trust and confidence in digital transactions cannot be underestimated by eIDAS 2.0. The regulations aim at the development of the adoption of standardized protocols and best practices for digital identity management, hence creating a more secure and transparent digital ecosystem.
What is the Difference Between eIDAS 1 and eIDAS 2?
| Aspect | eIDAS 1 | eIDAS 2 |
| Introduction | eIDAS 1, which is the name of the first version of the eIDAS Regulation, was officially adopted by the EU in 2014. The main idea was to create a legal environment for electronic identification, authentication, and trust services, on which the cross-border digital transactions within the EU were to be based. | eIDAS 2 is a proposed revised eIDAS Regulation which was developed by the European Commission in June 2021. This update is aimed at overcoming the existing limitations and weaknesses of the current framework while bringing in new rules to build digital identity management capacity and facilitating interoperability. |
| Trust Services | The main goal of eIDAS 1 was to lay the foundation for trust services, like electronic signatures, seals, timestamps, and electronic documents, which provide electronic transactions with legal validity across the EU member states. | Besides, eIDAS 2 brings more focus on building upon the trust services that are already present in eIDAS 1 and also facilitate the introduction of additional trust services that will respond to emerging needs and technological advancements. These can also be domain name system (DNS) security extensions, e-docs, e-signatures, and other digital trust services. |
| Digital Identity | eIDAS 1 only provided starter templates for digital identity management, such as the electronic signatures and authentication mechanisms, it did not offer a complete guide for that. | eIDAS 2 presents the notion of European Digital Identity Wallet (DIW), which is a centralized system designed to store and handle digital identity credentials.. The DIW serves as an efficient and safe way of verifying one’s identity on the web and promotes seamless interconnectivity and cross-border verification. |
| Interoperability | Interoperability was the most important purpose of eIDAS 1, intended to ensure the cross-border authentication and access to digital services without | eIDAS 2 places greater emphasis on interoperability seeking to overcome the limitations and the inconsistencies which hindered the cross-border digital |
| barriers. The implementation problems and the inadequate interoperability between national systems were identified. | transactions under eIDAS 1. The regulation is intended to support harmonized procedures and processes for continuous information exchange among the EU member states. | |
| Legal Framework | By the legal first framework, eIDAS 1 ensured the online identification and trust services within the EU. The principles were established which formed the basis of confidence in the digital environment; however, some limitations and challenges worth considering were outlined, which led to a revision. | eIDAS 2 is designed to extend eIDAS 1 legal framework and to tackle its some vulnerabilities, introducing new terms to improve the digital identity management and promote trust and security of the electronic transaction. |
| Scope | eIDAS 1 marked the beginning of efforts to establish a unified digital identity framework within the EU, setting the stage for cross-border electronic transactions. However, its scope was limited, and certain aspects required further development and refinement. | eIDAS 2, as its name suggests, is a comprehensive overhaul of the conventional framework, introducing a broader scope of provisions and the ever-changing nature of digital identity management. The main purpose is to create a more flexible and comprehensive regulatory infrastructure capable of sustaining the ever increasing volumes of digital trade in the region. |
| Implementation | Since its adoption in 2014, the eIDAS 1 was slowly implemented by the EU member states with each country having to transition their national laws to incorporate its provisions. This proceeding covered a wide range of legal, technical, and administrative problems. | eIDAS 1 dates back to 2014, while an increase in the number of amendments and updates have been made to respond to emerging issues and challenges. Although the revision of the system was required at the beginning, it occurred in the course of time, which later resulted in the proposal of eIDAS 2 in 2021. |
| Timeline | The first eIDAS Regulation was passed in 2014, and later on it has been amended to address | The public consultation on the eIDAS 2 proposal was launched in June 2021 with its future entry |
| additional issues and challenges. Nevertheless it was felt that the need for a comprehensive review arose over a period of time and the proposal for eIDAS 2 was made in 2021. | into force expected in 2024. By means of this timeline, the EU Member States have enough time to prepare for implementing the new regulations and experience a smooth transition from eIDAS 1 to eIDAS 2. | |
| Key Focus | The 1st version of the eIDAS was based on building a legal framework for eID and trust services security and interoperability in order to organize cross-border digital transactions in the European Union. | eIDAS 2 seeks to take the findings of eIDAS 1 further while correcting most of its critiques. eIDAS 2 also adds provisions to improve identity management, increase interoperability, and strengthen confidence and security in electronic transactions. |
| Specific Provisions | eIDAS 1 was drafted for the first time, which is meant to establish the base for electronic signatures, seals, timestamp and other trust services, with aim to enable secure and legally binding electronic transactions. | Among the types of trust services innovation established in eIDAS 1, eIDAS 2 additionally provides some new trust services, including electronic proof-of-delivery services, electronic seals, and qualified electronic archiving, needed in emerging situations as well as technological breakthroughs. |
| Objectives | The main scope of e IDAS 1 was to build a legal framework for eID and trust services within the EU for secure and cross border digital transactions in order to occur without difficulties. | eIDAS 2 will improve on the strengths of eIDAS 1, fix its shortcomings and provide new rules to further the use of digital identities, interoperability, and trust and security in online transactions. |
| Regulatory Impact | eIDAS 1 was a very important step in the process of the formation of digital identity frameworks in the EU. It helped to provide a platform for secure and interoperable online transactions. Nevertheless, some restrictions and problems were found and, therefore, a full review has to be organized. | eIDAS 2 is a modified version of the solution to renew and reinforce the EU digital identity infrastructure that will address the unmet needs of eIDAS 1 and, among the new provisions, promote interoperability, trust, and security in all electronic transactions. |
Purpose and Benefits of eIDAS 2.0
The initial eIDAS regulation dealt mainly with electronic ID and trust services for electronic transactions. The law also ensured that secure electronic interaction between citizens, organizations, and public authorities was to be recognized across the European Union.
This purpose was, and still is, to promote efficient online public and private services with an emphasis on the protection of electronic services realized by electronic signatures, seals, and timestamps.
One of the major changes that eIDAS 2.0 introduced is that of the expansion of the regulation boundary to cover more types of electronic trust services. eIDAS 2.0 is wider-ranged as it also includes electronic registered delivery services, electronic certificates for authentication, and electronic seals for electronic documents.
The “Qualified Trust Service Providers” (QTSPs) concept formation is one of the other focal points of the eIDAS 2.0 regulation. QTSPs will play a significant role in the updated regulation, as they will be in charge of overseeing that the electronic identities accredited correspond with the updated regulation.
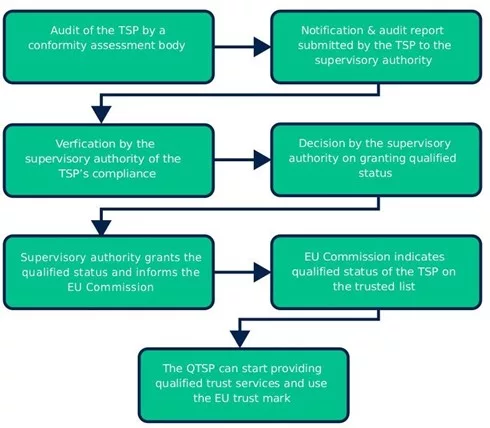
Through the eIDAS 2.0 regulation, qualified trust service (QTS) and Qualified Trust Service Provider (QTSP) are being defined to ensure legal and regulatory compliance with eIDAS high-level security standards and obligations.
QTSPs are required to comply with several security steps as e-transaction security providers which include generating electronic signatures, digital certificates, or timestamping services. These prerequisites are strong cryptographic algorithms, authentication methods, individual transfers, audit trails, and secure system architecture.
QTSP indicates a Trust Service Provider, which has gained qualified status and is overseen by the national supervisory body (SB).
eIDAS 2.0 looks to expand the concept of identity by including various services that can be accessed offline and online from anywhere in the world.
Through issuing a basic set of digital identity credentials (ID cards, passports, professional certificates, and driving licenses) it will become easily recognizable across the EU – European Digital Identity (EUDI) Wallets. These ‘wallets’ are like mobile apps or cloud services that collect and store digital credentials, making them usable for private and secure in various government and non-government cases.
This transformation, therefore, demands that a reliable, trusted, and secure identification process is created that would provide customers with a convenient process of purchasing, enrolling, or using these services.
Digital Identity Verification
Digital identity verification is the act of determining whether an individual or organization is who or what they say they are by electronic means. As the world turns digital and electronic transactions become the norm, verifying user identities has become critical for safety, trust, and compliance.
Remote identity verification is the most common use of digital identity verification technologies that don’t require physical documents and in-person verification as most of identity verification methods involve various technologies and methods to verify the identities of users.
There are Several Methods used for Digital Identity Verification including:
Document Verification:
The method we consider here is to confirm the realness of national identity documents using OCR technology for scanning and analyzing texts and algorithms for document verification.
Biometric Authentication:
Biometric authentication is based on physical attributes like fingerprints facial features, or iris patterns, which are unique to each person and used to prove an identity. Biometric data is captured using different kinds of sensors or cameras and is compared with the stored template for authentication.
Knowledge-Based Authentication (KBA):
KBA consists of verification of the user’s identity with the help of security questions that are strange and correlate with only the answer known by the user or the system requests personal information like the mother’s maiden name or the name of the first pet.
Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA):
2FA and MFA boost the security of the identification/verification process by requiring the users to provide two or more means/form(s) of identification or authentication like a password & one-time code sent via mobile device.
Digital identity verification is considered one of the most crucial problems that is greatly investigated in many sectors such as online banking, e-commerce, health care, and government services. Authentication via digital identity and the user’s true identity makes illegal access to data and resources, or identity theft and fraud, impossible.
In addition, the recent technological progress in the field of artificial intelligence (AI) and machine learning forms a basis for novel and incredibly accurate means of digital identity verification, with an emphasis on both security and user experience.
These technologies can go far in giving way to the ability to pulse through large data sets, pattern recognition, and spot abnormalities in the identification and verification processes, thus enhancing efficiency and reliability.
How to Prepare Your Business for eIDAS 2.0?
Preparing your business for eIDAS 2.0 is a complex process that integrates regulatory changes, the updating of policies and procedures, investing in technology solutions, training employees, and establishing partnerships.
Understand Regulatory Changes:
Begin by getting acquainted with the key updates introduced by eIDAS 2.0. Therefore, upgrades to the electronic signature standards, improved electronic identification methods, and the introduction of new trust services are among the measures that might be taken. Find out how these changes affect your business functioning and regulatory obligations.
Assess Current Compliance Status:
Perform a thorough review of the eIDAS 1.0 and other existing regulations to understand the current compliance position of your organization. Specify the gaps or weaknesses in the current processes, technologies, and policies concerning digital identity authentication and electronic transactions.
Update Policies and Procedures:
Review and evaluate your organization’s policies, processes, and internal controls to ensure that they match the requirements of eIDAS 2.0. Your rules must cover issues like electronic signature validity, methods of identity verification, data protection, and cross-border electronic transactions.
Invest in Technology Solutions:
Evaluate your existing technology setup and consider investing in technology solutions that help in achieving compliance with eIDAS 2.0. Find out the smart identity verifications, digital signatures, encryption technologies, and secure communication channels. Go for a solution that has security features and meets the technical standards of eIDAS 2.0.
Train Employees:
Provide thorough training for different department employees to make them grasp the implications of eIDAS 2.0 and their responsibilities in compliance. Create training sessions on issues like the digital verification process, electronic signature workflows, security of data, and relevant regulations. Encourage employees to deal with and solve compliance issues accordingly.
Establish Partnerships:
Identify strategic partners, vendors, and service providers who can work with you in meeting your organization’s compliance goals. Collaborate with legal advisors, tech experts, and industry peers to gain insights, share knowledge, and together address common pitfalls. Develop partnerships with credible, third-party providers that provide solutions that include identity verification, digital signatures as well as secure transactions.
Conduct Testing and Validation:
Perform extensive testing and validation of your systems, processes, and controls to make sure they are in line with eIDAS 2.0. Carry out scenario simulations to confirm digital identity assurance processes, signatory procedures, and international transactions. Identify any problems and weaknesses, and act to correct them before piloting.
Monitor Regulatory Updates:
Be updated on emerging changes in regulatory frameworks of digital identity and electronic commerce. Track information on regulatory agencies and industry organizations to remain current on updates in standards, guidelines, and best practices. Keep on assessing and adapting your compliance strategies to always remain in synchrony with the changing regulatory demands.
Implement Continuous Improvement:
Creating a framework for continuous improvement will help in maintaining compliance with eIDAS 2.0 and other relevant legislation. Periodically assess and enhance the policies, operations, and systems to align with the new regulations and control emerging threats. Conduct periodic audits and assessments to observe compliance effectiveness and define the places for improvement.
Conclusion
The adoption of eIDAS 2.0 marks a giant step toward the development of digital identity and electronic transactions in EU member states. The emphasis on widening the sphere of trust service, digital identity verification and redressing the omissions of the current regulation, eIDAS 2.0 is poised to birth a new era of secure and convenient digital transactions.
The changes caused by eIDAS 2.0 compel businesses to rethink their processes, technologies, and compliance measures to remain in line with the new regulatory framework. Organizations that appreciate the effects of eIDAS 2.0 and adopt appropriate policies and procedures, invest in technology solutions, and train their employees in this direction, can thrive in the world of digital economy while remaining in line with regulatory requirements.
With eIDAS 2.0 getting near implementation, they should keep it in mind, track regulatory changes, and reevaluate and redevelop their compliance efforts regularly.
Following eIDAS 2.0 which facilitates digital identity solutions and being proactive towards compliance systems, businesses can bring security, seamlessness, and value to customers and associates through the application of digital identity solutions.
Frequently Asked Questions (FAQs)
1. What is the eIDAS 2.0 regulation?
The eIDAS 2.0 regulation is the latest version of the eIDAS Regulation released to counter the identified weaknesses, introduce additional trust services and further develop digital identity verification. It tries to set up a stronger platform for the execution of electronic transactions and digital identity service on the European Union level.
2. What is the eIDAS 2.0 Regulation Proposal?
The eIDAS 2.0 regulation proposal is an amended version of the existing eIDAS Regulation aiming to address disadvantages, add the newly introduced trust services, and improve digital identity verification within the European Union. It aims to set up a more powerful framework of electronic trade and digital identity management.
3. What is the eIDAS regulation 910 2014?
eIDAS Regulation 910/2014 is a regulation that was designed to create a single market for secure e-signatures, e-seals, e-timestamps, e-delivery services, and website authentication, by establishing common rules for electronic signatures, electronic seals, electronic time stamps, electronic delivery services, and website authentication.
