Hashing vs Encryption – Know the Difference
Comparing Hashing and Encryption: Two Robust Methods for Safeguarding Data
Hashing vs. Encryption has been a long-standing debate in the technology world. Both security measures have pros and cons, uses, and capabilities, driving a long wall of separation between them. Consider them as one-way and two-way roads. On a one-way street, you can only move in one direction, unlike a two-way road, where you can move in opposite directions but on your own. Taking the car in the opposite direction on one-way road leads can lead to accidents.
Similarly, the significant difference between encryption and hashing is the direction. In encryption, we can encrypt and decrypt the message, but in hashing, the message cannot be decrypted once encrypted. With this understanding, let’s move on to a detailed comparison to determine the difference between encryption and hashing.
What is Encryption?
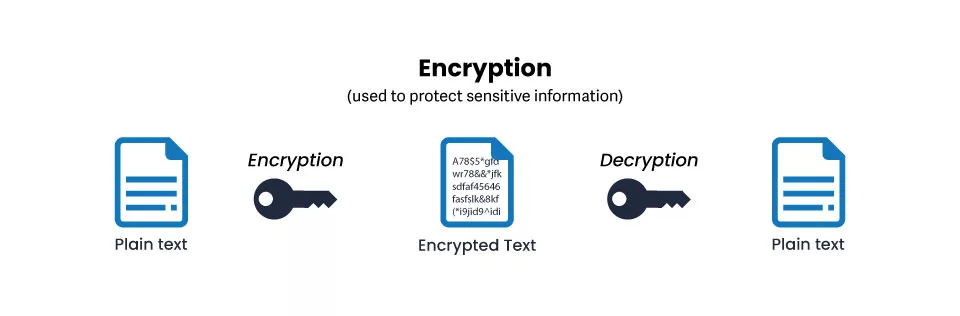
Encryption means hiding text in plain sight by mixing up its orientation with the help of a cipher text. It is like using complex coding (not programming code) techniques to create a mixed-up text that no human or computer can understand.
To be a bit rude, we can call the ciphered text garbage text because that is precisely what it looks and reads like. However, the good thing is that we can also decrypt the cipher text to find out what was the real message.
So, in encryption, we are converting plain text into cipher text with a set mechanism. And using the same mechanism, we can also convert the cipher text into plain text. Encryption is used to protect data and ensure it remains confidential. Encryption is used while storing or transferring data on a system to another device or network. With advancements in encryption technology, additional security measures are also applied to encryption, like authentication and non-repudiation.
What is Hashing?
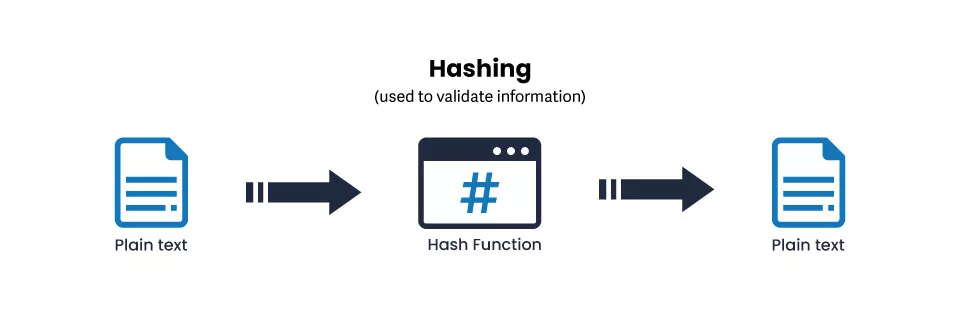
Hashing differs from encryption in that it does not convert the plain text but turns the text into a key using hash functions. The output generated with hashing cannot be reversed to find the original text. However, this process is used to authenticate the sanctity of the information shared. In other words, when we apply a hash to a text, it generates an output. No matter how often we apply a hash function to the text, it will always generate the same output.
So, this system is used to check whether the hashed text has been altered or edited in any way. Even the slightest change in the text will generate a different hashed output, informing that the text has been changed. Due to this, hashing functions are mostly used to protect passwords.
What is the Difference between Encryption and Hashing?
Let’s get into the details of hashing vs encryption and understand their utility and benefits when compared to each other.
Purpose of Using Hashing and Encryption
As we have understood from the definition, encryption mainly converts plain text into cipher text. This is done to keep the information shared via a digital medium secure and confidential.
With encryption, no unauthorized person, someone who doesn’t have the decryption key, cannot access the data. Even the ones who have access to the decryption key and can access the encrypted data have limited functionality regarding how they can interact with the data.
So, encryption is used popularly to share files, images, text, videos, and other sorts of information over the web.
Hashing is implemented with a different purpose. It is used to compare the same set of data as and when required to ensure that it has not been tampered with. When we have large volumes of data, comparing the hash functions is easier than comparing every bit of data.
Along with storing and securing passwords, hashing functions are also used for digital signatures. Then we have the geometric hashing system used in identifying and matching similar graphics on a computer or matching recognizable objects even if they have undergone some modifications.
In a nutshell, we can say that encryption aims to secure data confidentiality. But the purpose of hashing is to secure data integrity.
Direction | One-Way and Two-Way
Hashing has no reverse process. This means that once a text has been hashed, we cannot unhash it to find the original message. However, there is no need to unhash or reverse the process in hashing because the system is used for different purposes. We cannot reverse the hash function but only use it to map out the secured information. The hashed information is secure if the hash code is authentic.
Encryption, on the other hand, is a two-way street. Once the encryption is applied to obscure information, it can be reversed to decrypt the same information.
Algorithms Used in Hashing and Encryption
Another segment difference between encryption and hashing stems from the usage of algorithms. Listed below are a few algorithms for your reference.
Encryption Algorithms
- Symmetric Encryption
- Asymmetric Encryption
Symmetric Encryption
One of the techniques used in encryption is symmetric. It implies that one single key is used for encrypting and decrypting the information. So if one person used a string of characters to encrypt data, another would use the same string of characters to decrypt. Hence, the secret key must be present with the client and server.
Asymmetric Encryption
Asymmetric encryption uses a public key accessible to the website/server and the user. Another is the private key used by the administrator. In this, the public key is used for encryption, and the private key is used for decryption.
Hashing Algorithms
- MD5
- SHA256
- Tiger
MD5
Message Digest 5 algorithm provides a 128-bit output. It is a successor to the MD4 algorithm and brings several improvements. However, despite advancements, the MD5 algorithm has vulnerability and collision issues.
SHA256
The National Security Agency introduces the Secure Hashing Algorithm. Used popularly by several organizations, this hashing algorithm also brings quick updates making it more secure with time. SHA provides 256-bit protection, considered the most secure form of hashing-based security.
Tiger
Tiger is an upgraded version of the MD5 algorithm, as it provides 192-bit output. Modern-day computers and software use the Tiger algorithm. Today we also have the Tiger2 algorithm, which is an advanced form of encrypting solution.
There are many encryption algorithms apart from encryption and hashing, such as Advanced Encryption Standard (AES), RSA, Blowfish, Triple DES, and ChaCha20.
Which is more Secure? Hashing or Encryption?
There is no easy way to answer this question, as both types of security standards have distinct uses and purposes. However, for the sake of our discussion, we can compare them in terms of their security strength.
Let’s compare the time required to break the encryption and hashing protection.
| Hashing Standard | Time | Encryption Standard | Time |
| SHA 256 | 5.4 million years | RSA 2058 – Type of Asymmetric Encryption | 300 trillion years |
| MD5 | 12 minutes 22 seconds | AES 128 and 256 – Type of Symmetric Encryption | More than one billion years |
From the above table, we can be sure of one thing, that encryption is harder to break than hashing. We are talking about billions and trillions of years of continuous work required to crack the code.
But to make hashing more challenging and difficult to crack, we can use salting. It’s an additional precaution of sorts that adds a random string of characters to the hash value. With salting, the hashed value becomes even more obscure.
So, we will need higher computational power to crack the code with salting. It primarily protects the passwords from the hash table attack and reverses engineering the hashed value to find the password.
Length of the Output
We will get an output based on the input in hashing and encryption. This output is either the encrypted text or the hashed value. However, in one type of security system, the output is fixed; in another, the output depends on the input. Let’s find out how.
In hashing, no matter the length of the input, the output has limited characters. In other words, we can create a hash value of an entire 200-page book or hash a ten-character string of passwords; the hash value for both can be the same.
This is because the hash value generated does not convert plain text into another form. It only creates a hash value of the current information. Changes in the hashed text can lead to a change in the value.
But in encryption, the output depends on the ciphered text. The longer text means longer lengths of the cipher text.
Conclusion
Hashing and Encryption might be two different systems of enhancing security, but they are insanely important in today’s world. A world where anything we do on the web is susceptible to being cracked or accessed by a third party. Hence, setting in either or both systems is important to secure data.
We can use both techniques in the same environment and not risk overlapping as they have different purposes and areas of control. This sums up our discussion on hashing vs encryption and how they effectively provide a security net for our online transactions and data.
