New S/Mime Baseline Requirements – September 2023

In July 2020, the CA/Browser Forum initiated a significant development in the world of digital security by establishing the S/MIME Certificate Working Group (SMCWG).
The primary objective of this working group was to formulate and define stringent requirements for Certification Authorities (CAs) that issue S/MIME Digital Certificates. These certificates are pivotal in securing email communications, encompassing functionalities such as signing, verifying, encrypting, and decrypting emails.
Fast forward to the present day, and the CA/B Forum’s forward-thinking initiative is about to reach fruition. The eagerly awaited Baseline Requirements, encompassing a new set of standards, are poised to take effect on September 1, 2023.
This marks a watershed moment for electronic communication security and privacy. S/MIME Certificates, serving as the guardians of email integrity and the protectors of sensitive information, will soon adhere to a uniform level of security and compatibility.
This harmonization of standards ensures that S/MIME Certificates, the digital sentinels of email security, offer a consistently robust level of protection. The implementation of these new Baseline Requirements not only fortifies the security of internet communication but also enhances user privacy.
What is Secure/Multipurpose Internet Mail Extension?
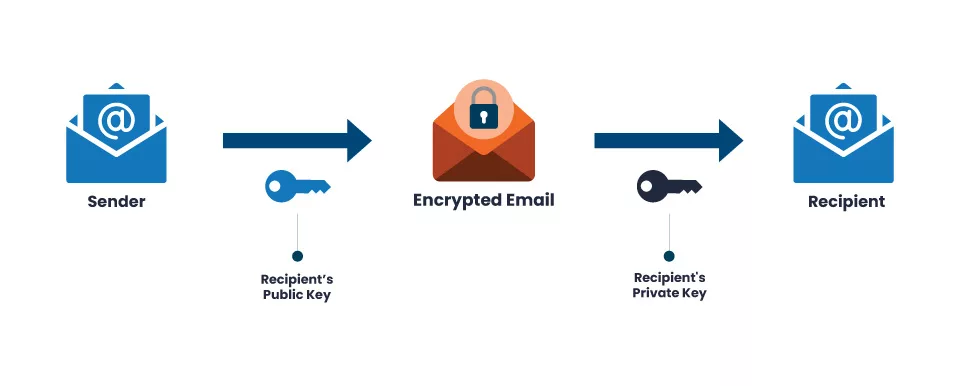
S/MIME, or Secure/Multipurpose Internet Mail Extension, is a widely embraced protocol for transmitting signed and encrypted email messages. Employing S/MIME signatures bolsters the verification of message authenticity and guards against tampering.
On the other hand, S/MIME encryption provides a secure veil for the content of messages, shielding them from prying eyes.
These forthcoming standards will apply to all trusted Digital Certificates bearing the Extended Key Usage (EKU) extension, expressly set as id-kp-emailProtection (OID: 1.3.6.1.5.5.7.3.4).
When did the CA/B Forum introduce these Guidelines?
In January 2023, the CA/B Forum introduced a set of fresh guidelines that will revolutionize the issuance of S/MIME (Secure Multi-Purpose Internet Mail Extension) certificate standards. These guidelines are scheduled to take full effect on September 1, 2023, ushering in a new era of email security.
S/MIME Certificates are digital credentials installed on devices to provide robust identity verification. These certificates enhance email security by enabling users to sign their outgoing messages digitally. When the sender and receiver possess Email Signing certificates, they can confidently exchange encrypted messages, knowing their communications remain secure and tamper-proof.
Recommended: What is a S/MIME Certificate and How Does It Work?
Introducing these updated guidelines represents a significant step forward in bolstering the security and privacy of electronic communications. As we look ahead to September 1, 2023, the email landscape is set to become even more secure, thanks to the implementation of these enhanced S/MIME certificate standards.
Role of Public Key Infrastructure (PKI):
The issuance of certificates has seen notable changes recently, including the introduction of amendments to the S/MIME Baseline Requirements.
It’s essential to note that these changes primarily pertain to public critical infrastructure (PKI) and organizations relying on well-known third-party certificates. Internal private CAs, which issue certificates for internal purposes, are not subject to these new baselines.
Recommended: How Public Key Infrastructure (PKI) Works to Keep Your Data Secure?
So, what’s the driving strength behind these modifications, and why were they deemed necessary? The core rationale behind these changes is establishing a standardized and consistent certificate issuance process across all Certification Authorities (CAs) and registration authorities.
Historically, different CAs and registration authorities followed varying issuance procedures, potentially introducing security vulnerabilities. Ensuring uniformity in issuing publicly trusted digital certificates has become imperative to enhance security and minimize risks.
What are the Various Aspects covered in S/MIME Baseline Requirement?
The scope of the S/MIME Baseline Requirements is comprehensive, covering various aspects of certificate issuance and management. Here are some key areas that fall under its purview:
Accurate Use of Certificates:
One of the fundamental aspects addressed by the Baseline Requirements is ensuring the correct usage of certificates. This involves validating that certificates are appropriately utilized according to their intended purpose, preventing misuse or misconfiguration that could compromise security.
Legitimacy of the Subject’s Identity:
The Baseline Requirements also emphasize validating the subject’s identity by CAs and registration authorities. This process ensures that the identity information provided by certificate applicants is accurate and reliable, further bolstering the integrity of the digital certificate ecosystem.
Auditing and Compliance:
Regular auditing and compliance checks are essential to verify that CAs and registration authorities adhere to the established standards. This aspect helps maintain accountability and ensures that the practices and procedures outlined in the Baseline Requirements are consistently followed.
Subject Identity Verification:
Another crucial component is subject identity verification, which includes confirming the subject’s original domain control. This step ensures that individuals or entities requesting certificates have legitimate control over the domains they claim to represent, safeguarding against unauthorized or fraudulent certificate issuance.
CA Operational Practices and Security Controls:
Ensuring the security and reliability of CAs is paramount. The Baseline Requirements encompass CA operational practices and security controls, setting standards for how CAs operate and protect their infrastructure to maintain the trustworthiness of their issued certificates.
Types of S/MIME Certificates:
Since S/MIME offers various validation options tailored to different user needs. Under the umbrella of S/MIME Baseline Requirements, S/MIME Certificates are categorized into four distinct validation types based on the information contained within the certificate’s subject field:
Mailbox-Validated:
This type includes optional subject attributes such as email address and/or subject serial number.
Mailbox validation certificates are characterized by the inclusion of specific attributes like an email address (e.g., [email protected]) or a serial number (e.g., 03:73:F0:57:FA:90:CD:E8:3B:J0:4E:C7:C6:EE:FG:5H) in the subject field. These certificates are well-suited for scenarios where the focus is on verifying the mailbox or device associated with the certificate.
Organization-Validated:
It encompasses solely Organizational (Legal Entity) attributes within the subject.
As the name suggests, this certificate type is intended for organizations and businesses. The subject field exclusively features the legal entity’s organization name without mentioning an individual’s name. It’s a practical choice for enterprises seeking to secure email communications while emphasizing the organization’s legitimacy.
Sponsor-Validated:
Subject details consist of Individual (Natural Person) attributes combined with the subject’s organizationName.
Sponsor-validated certificates are unique in combining both the individual’s name and the organization’s name in the subject field. These certificates are typically issued by enterprise Registered Authorities and serve a specific purpose.
Organizations issue sponsor-validated certificates to their employees, reflecting the employee’s and company’s names on the certificate. This dual-validation approach ensures a robust level of security for business-related communications.
Individual-Validated:
Subject information is exclusively related to the individual user.
This type of certificate is designed for individuals who require secure email communication. You’ll find the individual’s name in the subject field, such as “Joseph Joy” Unlike other certificate types, there is no mention of a company or organization name here. It’s ideal for personal use or situations where the sender’s identity is crucial.
Additional Categories of Baseline Requirements:
In each case, user control over the mailbox undergoes rigorous validation following the established baseline requirements. Generations, including Legacy, Multipurpose, and Strict, further delineate these categories.
Legacy:
This category accommodates most prevailing practices, making them eligible for CA/B guideline audits with minor adjustments. It introduces a unique organization identifier in certificates featuring organizational attributes and sets a maximum certificate validity of 1185 days. Legacy profiles ease the transition to Multipurpose and Strict categories compared to current practices.
Multipurpose:
Designed to cater to various use cases such as client authentication, document signing, and secure email. This category features a reduced maximum certificate validity of 825 days and emphasizes stricter adherence to subject DN attributes.
- Strict: Geared toward the long-term vision, this generation focuses exclusively on secure email applications and prohibits integration with other extensions. Its goal is to enforce rigorous compliance with Subject DN attributes and a maximum certificate validity of 825 days.
Moreover, S/MIME Baseline Requirements have established precise validation methods to authenticate user identities and control email addresses. These methods include:
Mailbox Challenge:
This involves proving control over the mailbox through an email challenge or response from the user.
- Domain Control: Leveraging the best practices outlined in the TLS Baseline Requirements, this method validates authority over the mailbox via the domain.
- Mail Server Operator Confirmation: This entails confirming control over the SMTP Fully Qualified Domain Name (FQDN) to which a delivered message is directed.
In complement to these detailed requirements, S/MIME Baseline Requirements define specific timeframes for the validity of various validations. Organizations and individuals may utilize identity validation for up to 825 days before the most recent validation. Similarly, mail server and domain control validation should not precede the certificate issuance by more than 398 days.
Wrapping up
In summary, introducing S/MIME Baseline Requirements is the key to email security and privacy evolution. These standards promise a more secure, consistent, and reliable environment for exchanging information, ultimately contributing to improving internet security and safeguarding user privacy.
Frequently Asked Questions (FAQs):
Q. What are S/mime’s Fundamental Requirements?
A: S/MIME baseline requirements are guidelines and criteria for the appropriate certificate-issuing process. It guarantees that all security requirements are satisfied.
Q. How long is the SMIME Certificate valid?
A: We reported that Apple changed the S/MIME certificate validity term to 825 days in November 2021.
Q. What are the Four Functionalities that SMIME Supports?
A: S/MIME provides authentication, non-repudiation of origin, message integrity, and message privacy as its core security functions.
Q. What is the OpenSSL Smime size Restriction?
A: The maximum file size restriction for OpenSSL SMIME is 1.49GB. It is possible to raise this cap, though.
Q. What is the Smime key length?
A: The hash function used by the Federal Network Agency must be SHA-256 or SHA-512 compliant, and the RSA key length must be at least 2048 bits.
Q. How much does a S MIME Certificate Cost?
A: The best pricing for a Comodo S/MIME certificate is $12.99 annually at Certera.com
Q. How can my S MIME Email Certificates be Renewed?
A: The procedure for renewing your certificate varies depending on the CA that granted it, but in general, it entails applying for a new certificate, proving your identity, and installing the new certificate on your email client and device. Your email settings or the website of the CA both allow you to verify the expiration date of your certificate.
Buy Trusted Email or S/MIME Certificates Starts at Just $9.49/Year
