What is ACME Protocol, and How does it Work?

Welcome! This article will discover a robust protocol and explore how it functions. ACME protocol, short for Automated Certificate Management Environment, is a seamless communication channel between Certificate Authorities (CAs) and various endpoints in a company’s digital ecosystem.
ACME automates the management of Public Key Infrastructure (PKI) certificates used in web servers, email systems, and user devices. This protocol has gained popularity due to its simplicity, cost-effectiveness, and ability to streamline certificate lifecycle management. Let us explore ACME protocol and its significance in modern enterprise security.
What is the ACME Protocol?
ACME Protocol, or Automated Certificate Management Environment Protocol, is a powerful tool for automating the management of certificates used in Public Key Infrastructure (PKI) systems. It facilitates seamless communication between Certificate Authorities (CAs) and endpoints. Unlike other protocols, ACME is free of licensing fees and can be easily configured. It is implemented by IT teams to enhance enterprise security.
In RFC 8555, the Internet Security Research Group (ISRG) published the ACME protocol as an Internet Standard. The current version of the protocol is ACME v2 API, released in March 2018, while the previous version (ACME v1) has been deprecated since April 2016.
What is the idea of the ACME Protocol?
The fundamental concept behind PKI certificate issuance is that Certificate Authorities, like Certera and Sectigo, are trusted entities responsible. They verify the legitimacy of certificate users and their associated domain names. Traditionally, exchanging information required for authentication and certificate issuance was manual. However, the ACME protocol streamlines this process by automating the communication between the CA and the user, eliminating manual intervention. It utilizes simple JSON-formatted messages transmitted over secure HTTPS connections. Furthermore, the ACME protocol extends its capabilities beyond certificate issuance, allowing for efficient revocation and renewal.
With ACME protocol, organizations can simplify and optimize their certificate management workflows, enhancing the security and reliability of their digital infrastructure.
Advantages of an Automated Protocol
Let us examine the benefits and uses of an automated protocol, explicitly highlighting the challenges and risks associated with manual certificate deployment and management. While PKI offers a robust authentication and encryption solution, manually handling certificates can take time and introduce unnecessary risks.
Regardless of the scale of certificate deployment, whether it’s a single SSL certificate for a web server or millions of certificates across various networked devices and user identities, the end-to-end process of issuance, configuration, and deployment can take several hours. Manually managing certificates also increases the likelihood of forgetting certificate expirations, ownership gaps, and vulnerabilities to attacks like Man-in-the-Middle (MITM).
To mitigate these challenges, enterprises require an automation standard like ACME. By implementing ACME, organizations can ensure that certificates are accurately configured and deployed without human intervention on an individual certificate basis. This automation not only reduces risk but also grants IT departments more significant control over operational costs.
What Sets ACME Apart from Other Options?
Various standards like Enrollment over Secure Transport (EST), Simple Certificate Enrollment Protocol (SCEP), and solutions tied to enterprise architectures such as Microsoft Active Directory are available in certificate automation. However, the ACME protocol has become an increasingly popular choice among enterprises. But why?
Enterprises heavily rely on PKI certificates to authenticate and encrypt many assets, including web servers, networked devices, mobile devices, user identities, email systems, IoT devices, network appliances, and DevOps environments. Adding to the complexity, enterprises often operate across multiple IT infrastructures rather than relying solely on a centralized architecture.
ACME has gained traction among IT teams as a solution to tackle the scale and complexity challenges they face. It offers several key advantages:
- Open Standard and User-Friendly: ACME is an open standard that provides a comprehensive set of commands and robust error-handling capabilities. Making ACME easily adoptable by enterprises and Certificate Authorities (CAs), simplifying the integration process.
- Robust Security Practices: ACME follows industry-leading Transport Layer Security (TLS) and other PKI security best practices. Ensuring IT teams confidently implement and manage valid PKI certificates while CAs maintain strict authentication procedures.
- Community Support: A thriving community supports and continuously enhances ACME. Unlike protocols controlled by a single vendor or organization, ACME benefits from the collaborative efforts of diverse contributors, ensuring ongoing improvements and innovation.
- Flexibility and Backup Support: ACME offers the flexibility to incorporate and support backup CAs, adding resilience to certificate management systems.
- Cost-Effective Solution: One of the significant advantages of ACME is its low cost. The protocol is free, eliminating licensing fees and reducing enterprise operational expenses.
How does ACME Protocol work Seamlessly?
The ACME protocol operates through two main components: the client and the server. The client, running on the user’s server or device, uses the protocol to request certificate management actions such as certificate issuance or revocation. The ACME server, hosted by a Certificate Authority (CA) like Sectigo, responds to these client requests and executes the requested actions once the client is authorized. The client and server communicate via JSON messages over a secure HTTPS connection.
Authentication plays a crucial role in the ACME protocol, specifically through an authentication step known as an ACME challenge. The CA can only issue a certificate or complete the request once the challenge is completed. Two types of ACME challenges are commonly used:
HTTP Challenges:
In this challenge, the CA sends a token to the ACME client, which then installs the token on the server. The client creates a file that combines the token with a thumbprint of the authorization key generated during setup. This file is placed on the server. Once the file is installed, the client notifies the CA, which retrieves and validates the file to complete the challenge.
DNS Challenges:
This challenge adds a verification factor by requiring the ACME agent to place a specific value in a TXT record within the domain’s DNS space. Like the HTTP challenge, the CA sends a token to the client, and the client appends the thumbprint of the authorization key to create and install the challenge file. After the agent informs the CA that the challenge has been met, the CA performs a DNS lookup and retrieves the TXT record to validate the challenge.
The challenge process is typically fast, usually completed within 15 seconds for both types. However, ensuring the server setup is complete before the ACME client sends any requests is essential. Delays in DNS propagation or firewall rules can cause ACME server queries to fail. It is recommended that clients should only respond to challenges once they believe the server’s queries will succeed, minimizing potential errors.
Time Taken in Troubleshooting the Challenges:
Satisfying ACME challenges is a relatively quick process that occurs behind the scenes. The ACME client handles most of the work, ensuring a seamless experience. The RFC provides some recommendations for efficient challenge completion:
- Clients should wait until they are confident that the server’s queries will succeed before responding to challenges.
- If initial attempts fail, the CA’s server allows the client to retry. It is advisable only to retry once every 5-10 seconds.
- The CA considers the challenge “in progress” if the client continues trying.
- There may be a slight delay between uploading the required file or DNS record and the CA being able to retrieve them.
In the digital context, where operations are measured in milliseconds, most challenges are typically satisfied in under 15 seconds.
What is the usual misconception of ACME?
Contrary to a common misconception, ACME is open to issuing domain validation (DV) SSL certificates. It can also be used to obtain higher-value business authentication certificates. However, for such certificates, it is necessary to have an existing business relationship with the chosen CA, such as an account with a balance or a payment agreement.
The ACME protocol itself remains the same regardless of the certificate type. Alongside setting up the ACME client and configuring it to communicate with the chosen CA, the organization undergoes either organization or extended validation based on their preference.
Once the validation process is complete and valid for 24 months, the ACME client can contact the CA, fulfill the domain challenge, and obtain the required certificate whenever a domain needs it.
Step-by-step Renew and Revocate your Certificate:
ACME protocol supports certificate lifecycle management, including issuing, renewing, and revoking PKI certificates. The process for issuing or renewing a certificate using ACME is straightforward and aligns with standard certificate management practices.
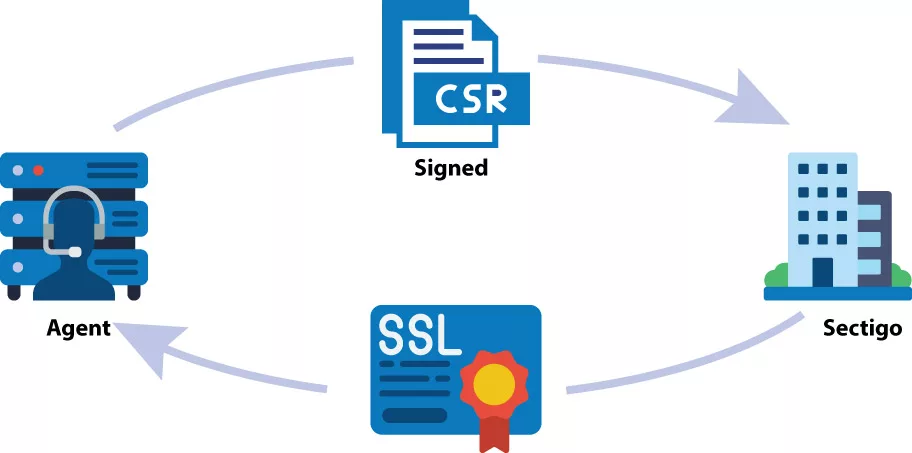
To request the issuance or renewal of a certificate:
- The client generates a Certificate Signing Request (CSR) that specifies the desired domain and includes the associated public key.
- The CSR is signed by the private key corresponding to the public key mentioned in the CSR.
- The client signs the entire CSR with the authorized key pair for the domain, demonstrating that it has the authority to request the certificate.
- The CA verifies both signatures: the signature within the CSR and the signature from the authorized key pair.
- If the signatures are valid, the CA issues a certificate for the authorized domain, utilizing the public key provided in the CSR.
- The CA then sends the issued certificate to the client.
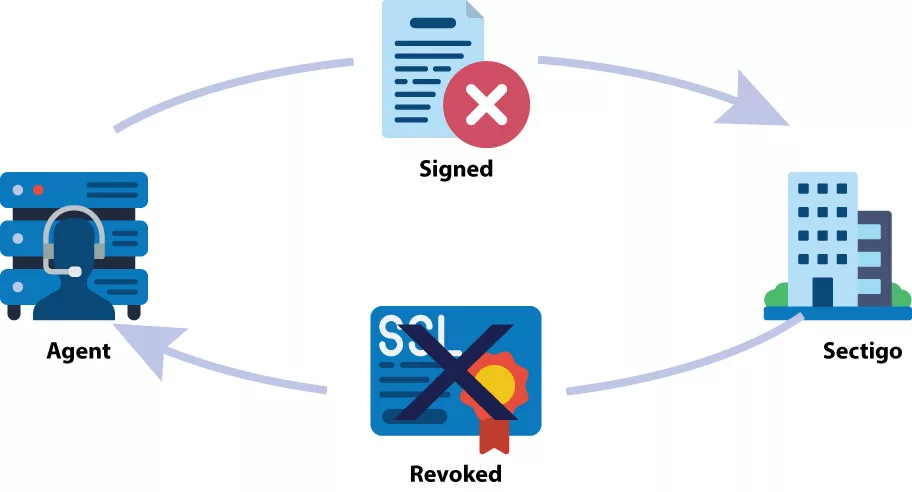
Revoking a certificate using ACME follows a similar communication process. The client signs a revocation request using an authorized key pair for the domain. The CA verifies the revocation request’s authorization and publishes the revocation information through standard revocation channels. Web browsers and other entities should no longer accept the revoked certificate.
Overall, ACME simplifies the management of certificate lifecycle events by providing a standardized and secure protocol for issuing, renewing, and revoking PKI certificates.
Process of Setting up an ACME Client:
The user must select the appropriate client and install it on the domain or server where the ACME protocol will be used. The ACME client offers flexibility and compatibility with various programming languages and environments commonly found in enterprises.
The available options for ACME clients are diverse and cover a wide range of programming languages and platforms. It includes Bash, C/C++, Clojure, Docker, Go, HAProxy, Java, Microsoft Azure, nginx, Node.js, OpenShift, Perl, PHP, Python, Ruby, Rust, and Windows/IIS.
QUICK NOTE: There are no proprietary clients for specific Certificate Authorities (CAs), as ACME is an open standard. It allows organizations to choose their preferred CA if it supports the ACME protocol.
Popular ACME v2 clients, hosted on GitHub, include Certbot by the Electronic Frontier Foundation (EFF) and sponsored by Sectigo, ACMESharp, acme-client, GetSSL, Posh-ACME, Caddy, Sewer, nginx ACME, and node-acme-lambda.
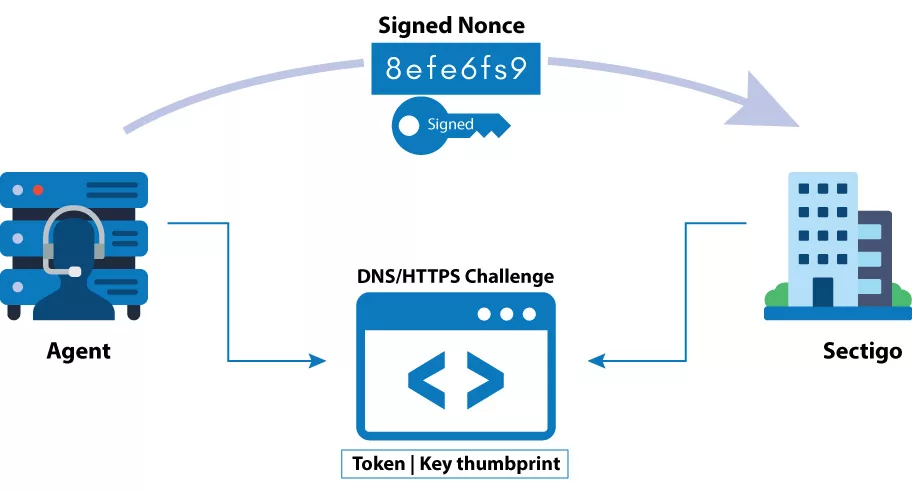
Once the ACME client is selected, the next step involves configuring the client and installing it on the server where PKI certificates will be deployed. The configuration process typically consists of six simple steps that can be completed in a few minutes:
- First, the client prompts the user to enter the domain(s) that must be managed.
- Then the user selects the desired CA from the client’s ACME-supporting CAs.
- Next, the client contacts the chosen CA and generates a private key pair.
- Here, the CA issues an ACME challenge (HTTP or DNS). It is done to authenticate the user’s identity.
- Lastly, the CA also sends a randomly generated nonce along with the challenges. The client signs the nonce with the generated private key to demonstrate ownership of the key pair.
- In the final step, the user defines the frequency at which the client will contact the CA to renew the certificate.
Which PKI and TLS/SSL certificate types does the ACME Protocol support?
The ACME protocol supports various TLS/SSL certificates and other PKI certificates. These certificates can be used for web servers, email systems, user devices, and any other application where PKI is utilized. However, it is essential to note that the CA (Certificate Authority) must support ACME for the specific type of PKI certificate needed.
In the case of SSL certificates, ACME supports different authentication modes, such as domain validation (DV), organization validation (OV), and extended validation (EV) certificates. Additional authentication steps may be required for certain types of certificates beyond what ACME provides.
Sectigo, as an example of a Certificate Authority, offers SSL/TLS certificates and Code Signing, S/MIME, and other X.509 certificates that support ACME. For enterprises that require automated management of these certificates at scale, the Sectigo Certificate Manager provides comprehensive support for the ACME protocol, enabling end-to-end lifecycle management automation. It guarantees efficient and secure certificate management processes for organizations.
Some General Errors Encountered in ACME:
When working with the ACME protocol, it is common to encounter errors. ACME uses a standardized format called a problem document (defined in RFC 7807) to report these errors. The problem document includes a “type” field containing tokens providing information about the problem.
The format of the string representing the problem document looks like this:
urn:ietf:params:acme:error:In the ACME RFC, “token” refers to the inputs between each colon in the string.
Analyzing the problem document enables API clients to understand both the high-level error class indicated by the status code and the specific details of the problem.
The focus here is on the “error” token in the string. Below is a brief list of possible errors and their meanings. The ACME client can resolve specific errors, while others may require human intervention.
What are the Latest Perks of ACME?
One of the key benefits of using the ACME protocol is the ease of switching between Certificate Authorities (CAs). As more commercial CAs begin to support ACME, this advantage becomes more significant.
To switch CAs using ACME, the process is straightforward:
- Create an account with the new CA.
- Update the URL or IP address of the ACME agent (client) contacts to communicate with the new CA.
- After obtaining the necessary authorization, the ACME agent handles the rest of the process.
- The agent replaces the old certificates issued by the previous CA with new certificates obtained from the new CA.
TIME FOR UPDATES:
Sectigo has plans to fully roll out its ACME protocol support in the upcoming summer, while DigiCert has already announced its support earlier this year. This widespread adoption of ACME by CAs further facilitates the seamless transition between CAs for certificate management.
