What is a Hardware Security Module? Comprehensive Guide

Imagine a world where your valuable secrets and sensitive information are guarded with an ironclad shield of protection. A realm where unauthorized access is nothing but a distant nightmare. Welcome to the realm of HSM, the mighty guardian that stands tall to safeguard your digital treasures.
HSM, short for Hardware Security Module, is a physical device that acts as a fortress for your data, ensuring its confidentiality, integrity, and availability. This article seeks to provide a comprehensive understanding of HSMs, exploring their functionalities and highlighting their significance in today’s ever-evolving digital landscape.
What is HSM?
HSMs are standalone and tamper-resistant hardware devices specifically engineered to fortify cryptographic processes. They serve the essential functions of generating, safeguarding, and managing encryption keys, which are crucial for data encryption and decryption, and creating digital signatures and code signing certificates. HSMs can take the form of plugin cards or be integrated into various hardware components, including smart cards, appliances, and external devices.
These devices undergo rigorous testing, validation, and certification processes, adhering to strict security standards like FIPS 140-2, Common Criteria EAL 4+, or equivalent benchmarks. These benchmarks assure users that the devices offer unparalleled levels of security and shield against potential threats, ensuring the utmost confidentiality and integrity of data.
Working of HSM
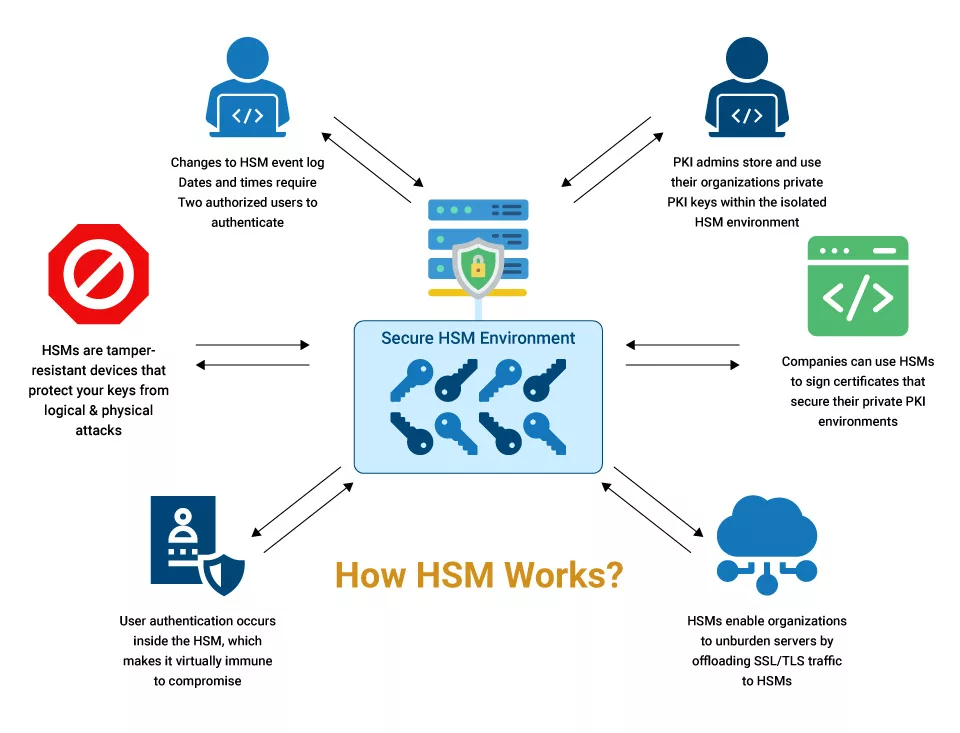
Here’s an outline of how HSMs work:
Key Generation and Storage:
HSMs use secure random number generators (RNGs) to generate strong cryptographic keys. The generated keys are securely stored within the HSM and safeguarded against unauthorized access or extraction, ensuring keys’ integrity and randomness, which are crucial for robust cryptographic operations.
Key Management:
HSMs provide a comprehensive suite of key management functionalities, which includes key generation, import, export, versioning, and facilitating key lifecycle operations like rotation and retirement.
Cryptographic Operations:
HSM excels in performing various cryptographic operations. They offer encryption and decryption capabilities and play a critical role in generating and verifying digital signatures, ensuring the authenticity and integrity of electronic documents and transactions. They also support secure hashing algorithms for data integrity verification and provide secure APIs and interfaces for the seamless integration of cryptographic functionalities into applications.
Secure APIs and Interfaces:
HSMs offer secure APIs and interfaces. APIs establish a secure communication channel between the application and the HSM, preventing unauthorized access and safeguarding cryptographic material from tampering.
Physical and Logical Security:
HSMs incorporate robust physical and logical security measures. Physical security features include tamper-evident casings, sensors to detect physical attacks and secure key storage mechanisms. Logical security encompasses robust authentication mechanisms, access controls, and cryptographic operations executed within a trusted environment.
Compliance and Auditing:
HSMs provide the necessary capabilities to comply with security regulations and industry standards. They offer auditing and logging mechanisms, enabling organizations to track and monitor cryptographic operations. Compliance features within HSMs assist in demonstrating adherence to security best practices and successfully passing regulatory audits.
Types of HSM
HSM devices come in various types, each tailored to specific use cases and industry requirements. However, there are two main types of HSMs:
General Purpose HSMs:
General purpose HSMs are versatile devices that support a wide range of encryption algorithms, such as CNG, CAPI, and more. They are designed to cater to various applications that require cryptographic services and secure key management.
General purpose HSMs are commonly used in environments where Public Key Infrastructures (PKIs) are implemented and in managing crypto-wallets and other sensitive data. These HSMs offer flexibility and compatibility with different systems and encryption standards.
Payment and Transaction HSMs:
These HSM devices are tailored to the financial industry’s requirements and are essential in maintaining compliance with Payment Card Industry Data Security Standards (PCI DSS).
Payment and transaction HSMs provide specialized cryptographic services and secure key management solutions that align with the specific needs of payment processing systems. They play a critical role in securing financial transactions and ensuring the confidentiality and integrity of payment card data.
It’s important to note that while general purpose HSMs offer broader applicability, payment and transaction HSMs focus specifically on securing payment card information and complying with industry-specific standards. The choice between these two types of HSMs depends on the specific security requirements and use cases of the organization or industry involved.
Common Use Cases for HSMs
HSMs find applications in various industries and scenarios. For example, financial institutions utilize HSMs to secure transaction processing, ATM networks, and payment systems.
Government agencies rely on HSMs for secure document signing and encryption of sensitive information. HSMs are also used in cloud environments to protect cryptographic keys and ensure the confidentiality of customer data.
Apart from these, here are some of the unique use cases of HSMs:
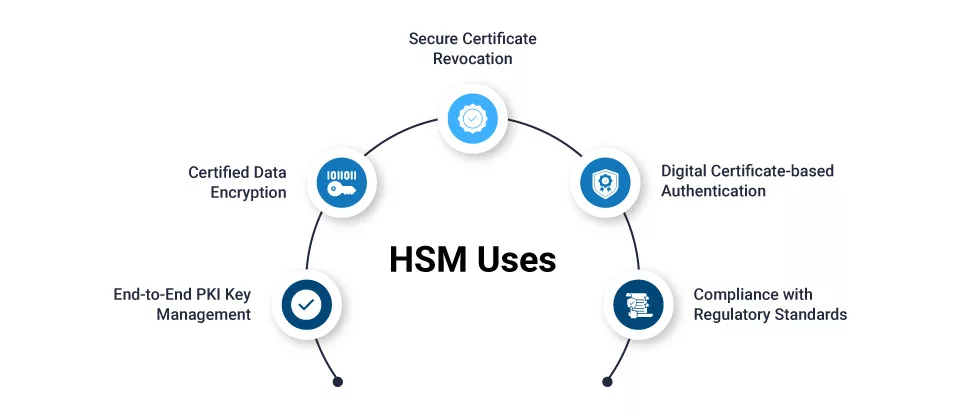
End-to-End PKI Key Management:
HSMs generate, protect, and manage private keys, including Root CA Key, ensuring the secure implementation of Public Key Infrastructure for robust encryption and digital certificate management.
Certified Data Encryption:
HSMs support certified implementations of leading data encryption algorithms such as RSA, ECC, and AES, ensuring high-level encryption standards for secure data protection.
Secure Certificate Revocation:
HSMs provide functions to securely generate the Certificate Revocation List (CRL), enabling the efficient and secure revocation of digital certificates when needed.
Digital Certificate-based Authentication:
HSMs authenticate users and devices by generating digital certificates, ensuring secure and trusted authentication for secure access control.
Key Lifecycle Management:
HSMs generate, manage, and securely delete cryptographic keys required for various encryption processes, maintaining the integrity and security of key management throughout their lifecycle.
Compliance with Regulatory Standards:
HSMs help organizations meet existing and emerging regulatory compliances such as UIDAI, eIDAS, etc., ensuring adherence to data protection and privacy regulations.
Features of HSM
HSMs offer a range of features to provide maximum security for cryptographic key management and operations. Here are some key features:
Tamper Resistance:
HSMs are built with tamper-evident casings and physical protections. They incorporate sensors and mechanisms that detect and respond to physical tampering attempts, such as opening the casing or tampering with internal components. These features ensure the integrity of the HSM and protect against unauthorized access to cryptographic keys.
Zeroization of Keys:
HSMs can securely erase cryptographic keys, ensuring their complete removal from the system and preventing unauthorized access or recovery.
Access Controls:
HSMs enforce strict access controls to prevent unauthorized users from accessing sensitive cryptographic material. Role-based access control (RBAC) mechanisms ensure that only authorized individuals or applications can interact with the HSM and perform cryptographic operations.
Robust Authentication:
HSMs employ strong authentication mechanisms to verify the identities of users or applications attempting to access the HSM. These devices mostly employ two-factor authentication, requiring a combination of something the user knows – a password and something the user has – a smart card or something the user is – biometric data to establish trust and grant access.
APIs and Interfaces:
HSMs provide secure APIs and interfaces that allow applications and systems to integrate with the HSM. Standard cryptographic protocol, are often supported, enabling seamless integration with existing systems.
Secure Design:
HSMs are designed with security in mind. They undergo rigorous testing and evaluation to meet recognized security standards, such as FIPS 140-2. The design principles encompass both physical and logical security measures to create a trusted environment for cryptographic operations.
Recommended: New Code Signing Changes: Delivery Modes, HSM
Isolated Environment:
HSMs operate within an isolated environment, separate from the host system or network. This isolation ensures that sensitive cryptographic keys and operations remain secure even if the host environment is compromised. By creating a distinct boundary, HSMs provide an added layer of protection against unauthorized access and potential attacks.
Cloud-Based HSM
The cost of acquiring a hardware security module (HSM) device often poses a significant financial barrier for businesses.
A report published by Security Today in 2018 highlighted that the deployment cost for a single HSM device could range from $30,000 to $40,000. Moreover, this expense does not cover additional aspects like support and maintenance.
To enjoy the advantages of utilizing an HSM device, businesses have two options. They can either bear the mentioned cost or consider the adoption of cloud-based HSMs.
Prominent vendors like AWS now offer several avenues to explore cloud-based HSM products and services. One option is to rent a dedicated physical HSM appliance that can be stored in an off-site data center.
Alternatively, businesses can choose to pay for access to the features of an HSM vendor’s device or appliance. There is also the possibility of paying for access to a virtual environment within a vendor’s shared HSM.
Recommended: CSR Generation and Import Certificate in Azure HSM
Integrating HSMs with cloud-based services establishes a trusted environment for generating, storing, and protecting encryption and decryption keys while enabling organizations to retain key control with third-party cloud providers, thus adding an extra layer of protection.
Additionally, cloud-based HSMs help organizations meet regulatory compliance for key management and data protection. They enhance defense against breaches, insider threats, and unauthorized access. By incorporating HSMs into their cloud infrastructure, organizations demonstrate their commitment to safeguarding sensitive information.
Note: While cloud-based HSMs offer convenience and cost benefits, there are other considerations to keep in mind. Cloud service providers often demand that clients utilize Hardware Security Modules (HSMs) hosted within their own data centers.
This practice can limit the control organizations have over their key management processes. Alternatively, if a provider allows the use of on-premises devices, issues with connectivity may arise, leading to unwanted delays and compromising the overall system efficiency.
To overcome these challenges, fortunately, Key Management as a Service (KMaaS) emerged as a solution. KMaaS provides a centralized platform with HSM-level security tools, eliminating the need for physical hardware. By leveraging this cloud service, organizations can ensure the integrity and confidentiality of their data, even in complex cloud deployments.
Why Integrate HSM with PKI?
Integrating HSM with PKI brings several benefits to organizations, such as:
Safe Key Administration:
Integrating HSM with PKI enables organizations to establish a solid key management process. Private keys are generated within the HSM’s secure environment and never leave its boundary, significantly reducing the risk of exposure. HSMs offer features like key backup and secure key deletion, minimizing the chances of key leakage.
Enhanced Certificate Security:
HSM integration strengthens the security of digital certificates. HSMs can securely issue and store certificate signing keys, protecting them from unauthorized use. By storing certificate private keys within an HSM, organizations can prevent key theft and unauthorized certificate issuance, safeguarding their PKI ecosystem against potential attacks.
Streamlining Compliance Requirements:
Integrating HSM with PKI assists organizations in meeting compliance requirements. Many regulations and standards, such as HIPAA, mandate the use of HSMs for protecting cryptographic keys. By implementing an HSM-PKI integration, organizations can ensure adherence to these regulations and streamline their compliance processes.
Factors to Consider While Purchasing an HSM
Here are the factors that you should consider while buying an HSM:
Security Features:
Evaluate the security measures implemented by the HSM. Look for tamper-evident hardware, secure firmware, strong authentication mechanisms, and adherence to industry standards like FIPS 140-2 or Common Criteria.
Performance and Scalability:
Assess the HSM’s cryptographic performance to ensure it can handle your organization’s workload. Consider factors like transaction speed, key generation time, and cryptographic algorithm support.
Integration Capabilities:
Determine how well the HSM integrates with your existing systems, applications, and cryptographic protocols. Compatibility with industry standards and protocols like PKCS#11 or Microsoft CryptoAPI is crucial for seamless integration.
Key Management:
Evaluate the HSM’s key management capabilities. Look for key import/export, backup, rotation, and revocation features. Consider whether the HSM provides secure key storage and supports various key types (asymmetric, symmetric, etc.).
Compliance Requirements:
Determine if the HSM meets your organization’s compliance requirements. Consider regulations specific to your industry, such as PCI-DSS for payment card data. Ensure the HSM helps you achieve regulatory compliance.
Vendor Support and Reputation:
Research the vendor’s reputation, experience, and track record. Consider factors such as customer reviews, customer support quality, and the vendor’s commitment to ongoing product updates and security patches.
Physical Considerations:
Consider physical factors like the HSM’s size, form factor, and power requirements. Ensure it can be securely installed and maintained adequately within your organization’s infrastructure.
Budget and Total Cost of Ownership:
Evaluate the total cost of ownership, including initial purchase costs, ongoing maintenance fees, and any additional licensing fees. Consider the value the HSM solution provides in relation to your organization’s budget.
Third-Party Certifications:
Look for HSMs that have undergone independent security certifications, such as FIPS 140-2, Common Criteria, or ISO 27001. These certifications validate the security and reliability of the HSM.
Conclusion
In conclusion, HSMs fortify cryptographic processes and safeguard valuable information. Their functionalities, security features, and wide range of applications make them indispensable tools for organizations seeking to protect their digital treasures in today’s ever-evolving digital landscape.
