What is Port 443? Detailed Guide on HTTPS Port 443

Owners of websites worldwide are switching from HTTP to the secure HTTPS protocol. Today, using port 443, ninety-five of the search engine’s internet traffic is encrypted. But what does HTTPS port 443 mean? And why is using the HTTPS standard port of such significance for website owners and, particularly, e-commerce organizations?
Over five million records were compromised in 83 significant data breaches found by IT Governance in February 2022. This is only the beginning, under IBM’s forecasts for 2022.
There is the highest risk around each nook and cranny, whether in eavesdroppers, man-in-the-middle attacks, or phishing attacks. Since there are so many potential dangers, businesses and other organizations striving to avoid cybercrimes prioritize user protection online.
Providing a secure browsing experience has become an essential challenge for website owners, companies, and Google in response to the rising number of cyberattacks.
The tech giant marks websites without an SSL/TLS certificate loaded as “Not Secure” and nearly all other major browsers agree. However, what can you do to get rid of this security alert or stop it from ever showing up on your website in the first place? Use a tool to connect through port 443 while utilizing a secure protocol.
This insecure connection warning message can be removed by getting an SSL certificate on the web server that hosts the website you’re attempting to access.
An SSL/TLS certificate establishes a private, secure, and encrypted communication channel between the client browser and the server. When you return to the website later, the connection will be created using port 443 and HTTPS.
What Exactly Are Ports and Port Numbers?
A port is a software-defined number in networking that is connected to a network protocol and accepts or transmits communications for a specific service to operate. Ports on a network make sure connections go where they’re supposed to and that traffic doesn’t block.
A 16-bit unsigned integer called a port number uniquely identifies every transport protocol and address combination. Standardized ports with an assigned number are installed on all network-connected devices.
In the 1970s, the early ARPANET developers initially proposed the idea of port numbers. The original word, socket number, had a 40-bit size.
There are 65,535 port numbers, separated into three ranges: commonly used, registered, and dynamic or private. These port numbers are allotted to various protocols.
Big companies and popular applications like Apple QuickTime and Structured Query Language (SQL) typically reserve renowned (well-known) ports with numbers 0 through 1023.
A range of 1024 to 49,151 port numbers are available for registration. Anyone can use dynamic or private ports ranging from 49,152 to 65,535. Additionally, a temporary port number might be assigned for the request period.
What does HTTPS Port 443 Refer to?
HTTPS Port 443 is a vital component of secure website communication. It is the default port for HTTPS, the secure variant of the HTTP protocol. Using Port 443, HTTPS encrypts the data transmitted between a user’s browser and a website, protecting critical information from malicious attackers.
Implementing HTTPS with Port 443 not only ensures the confidentiality of information but also develops user confidence by showing the padlock icon and “Secure” label in the browser’s address bar. Ensure your server has been configured to use Port 443 and the HTTPS protocol to secure communication on your website and user data.
A user’s browser will automatically try to connect to a website utilizing secure port 443 when they input a URL that begins with “HTTPS://.” This port is used in combination with the SSL/TLS protocols to provide a reliable, encrypted connection. Doing this ensures that all data transmitted between the two parties is confidential and concealed from third-party eavesdropping.
When port 443 is unavailable, the connection automatically switches to port 80. However, that only occurs if the website allows for unsecured connections, in which case a warning notice will be sent to the end user.
How Does HTTPS Work?
So, how does HTTPS work, and what goes on behind the curtain? Let’s explore!
Your account information (if you’re trying to log in to the website) remains encrypted whenever your client browser submits a request to a website across a secure communication channel. This shows that it cannot be read by a network attacker. This scenario takes place when the server gets a ciphertext that was produced by encrypting the original data.
Even if the transmission is intercepted, the attacker only has unreadable data and needs an appropriate decryption key to be transformed into readable form. Here is an illustration showing how this technique works:
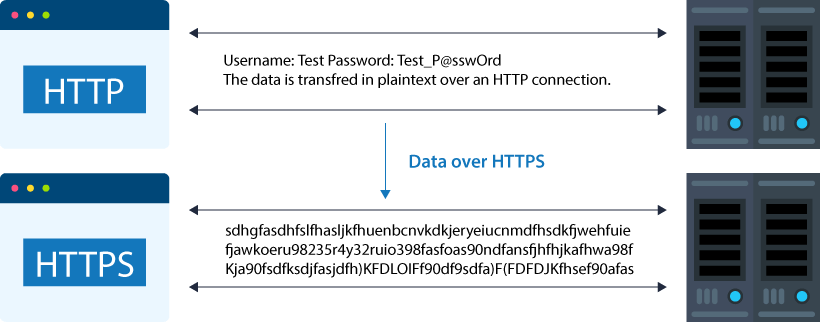
HTTPS connection securely encrypts traffic through port 443.
A shared symmetric key is distributed over HTTP through an SSL/TLS connection using public key encryption (where there are two keys: public and private), and this key is then used for bulk transmission.
HTTPS port 443 is used for TLS connections. The client can also switch from an unencrypted connection to an encrypted one by sending a request.
The browser and the server must compromise on the connection parameters used during communication before enabling a connection. They execute an SSL/TLS handshake to reach an agreement:
The process starts with a hello message transfer across the client browser and the web server.
When protocol negotiation initiates, the encryption standards that each party supports are sent, and the server shares its certificate.
The server’s public key is now in the client’s possession due to this certificate. It validates the server certificate’s legitimacy before generating a pre-master secret key using the public key. The pre-master secret is then encrypted using the public key and given to the server.
In accordance with the value of the pre-master secret key, both parties individually calculate the symmetric key.
Both parties send a modified cipher spec message to confirm that they have computed the symmetric key and that symmetric encryption will be used for the bulk data transfer.
What does HTTPS Port 443 Secure?
Secured communication is delivered using HTTPS over port 443 in order to establish an encrypted connection between the browser and the server it wants to connect to.
Your login credentials, credit card information, and bank account number are securely transmitted over this channel when you initiate a web-based purchase of products or services. For this reason, financial institutions and internet organizations that want to secure their customers’ sensitive data and prevent data breaches frequently employ an HTTPS connection through port 443.
Because of HTTPS’s encryption, your Internet Service Provider (ISP) cannot read or listen in on your data transactions between client and server. As a result, confidentiality is ensured, and tampering can be prevented. The padlock that can be seen in the website’s address bar is one of the trust symbols.
Why do We Require Port 443?
HTTPS port 443 is required because it enables secure HTTPS connections and encrypted data transfer. Data transferred across a standard port, such as port 80, is viewable as plain text. This is worrisome because cybercriminals and malicious individuals might view and steal traffic data.
- The SSL certificate and an encrypted connection help to keep payments secure. You must have an SSL certificate and encrypt your data if you own an online business and want customers to be allowed to pay with debit and credit cards.
- It gives your consumers peace of mind that their data is secure, increasing the probability that they will do business with you again.
- Axway Global Consumer Survey data shows that customers are more inclined to purchase from websites where they feel that the security of their data is vital. 75% of those surveyed stated they would cease business with organizations with data breaches.
- It prevents man-in-the-middle attacks and keeps data secure while in transit. Because the data is encrypted and authenticated as it is transferred via HTTPS, various malicious attacks are minimized.
- This prevents traffic eavesdropping and data decryption. Customers should be aware that a website’s validity cannot be completely guaranteed by the HTTPS protocol or the secure padlock in the browser address bar.
- Fostering client trust could help in raising conversion rates. Consider the following websites if you had to purchase an expensive smartphone online:
- Webpage one, where all transactions take place in Port 80 and utilize the insecure HTTP protocol
- Webpage two’s URL begins with HTTPS, a secure protocol, and all communication takes place in Port 443.
Baymard’s most recent Ecommerce Checkout Usability survey, which found that 18% of customers quit purchasing when they lack confidence in a website. Why Does It Matter? Because security and trust could significantly influence decision-making processes and purchasing while shopping online.
So, data protection has increased in significance with the development of e-commerce. Any website owner who wants their customers to use their services securely and confidently will employ an encrypted connection for data transmission between their customers’ browsers and the web servers hosting their websites.
In this concern, HTTPS port 443 becomes essential. Let’s look at how you can make it available on your PC.
How can Port 443 be Opened in Windows?
You must add Port 443 to the Firewall to enable it on Windows. To enable port 443 in Windows Firewall, follow these steps:
- To enter the Firewall Control Panel, go to “Start” > “Run” and type Firewall.cpl
- Then click “Inbound Rules” in the top-left corner of the left pane after choosing “Advanced Settings” from the left pane.
- Next, select “New Rule” in the “Action” column of the right-side panel.
- It will start a new window. You need to enter “443” next to “Specific local ports” under “TCP” selection.
- Click “Allow the connection” and press “Next” in the “Action” window.
- Then click “Next” after selecting “Domain” and “Private” in the “Profile” window.
- Enter “WCF-WF 4.0 Samples” as the name in the “Name” field and press “Finish.”
Please note that you must repeat steps two through eight to set up the outbound rules.
What HTTPS Port 443 Does Not Do?
More than basic safety measures are required when working with sensitive data online. Therefore, it’s important to remember what HTTPS cannot protect:
- Users are not protected from fingerprinting attacks by it.
- The bad guys can still read (and abuse) some less sensitive information.
- Which websites you are watching,
- Your IP address and location,
- How frequently you browse websites, Message size.
- It cannot assure you if a criminal established the website.
- Finally, private browsing won’t be possible with HTTPS Port 443.
Conclusion
Who you are—a site owner or a user—does not matter. On an unencrypted connection, all browsing is done by one side, and all communication is in plain text.
Since reading and compromising/misusing the data is very simple, it poses a risk to your company. Despite having many drawbacks and restrictions, SSL encryption security via port 443 HTTPS does make the internet more secure.
Several Certificate Authorities and SSL resellers sell SSL certificates at affordable prices. They are concerned about your needs and provide the finest SSL certificate needed for your website, depending on the domains and subdomains you need to secure.
FAQ’s
Is HTTP 443 the same as HTTPS?
HTTPS (Hypertext Transfer Protocol Secure) is a protected and secured variant of HTTP in which all communication is routed over port 443. A secure connection is built between the browser and the web pages using the TCP protocol, which is also linked to this port.
How do I Fix Port 443 Enabled?
For Windows
- Open the server.properties file at [app-path].
- By switching the relevant settings from N to Y, enable port 80 (and 443).
- Alter the server port in all providers installed on your network.
- Modify the User Client config file’s server port.
- Finally, restart the Application Server.
How do I know if Port 443 is Open?
Here’s how to use the “netstat” command to accomplish it:
- Access the terminal on your Linux computer.
- Press Enter after entering sudo netstat -tulpn | grep:443.
- If the command gives any output, your system’s port 443 is open.
How do I know which Process is using Port 443?
sudo netstat -tulpn | grep :443The output of the column indicates which PID is listening on that port.
What are the Purposes of Ports 80 and 443?
Unlike Port 80, which allows for plain text data transfer, Port 443 allows for data transmission through an encrypted network.
