What is Quantum-safe Cryptography? Quantum vs. Post-Quantum Cryptography

The number of Internet users globally peaked at 4.7 billion in early 2020, representing a startling 1,187% surge in only 20 years.
In addition, our growing reliance on Internet-based technology produces enormous volumes of data. This data must be encrypted since it includes many “sensitive” information. We utilize specialized encryption techniques to ensure that only authorized persons possessing encryption keys can view this data.
We’ve been using the same cryptographic algorithms, like RSA, to secure our data for decades. These encryption techniques were mainly effective, but the quantum threat will soon render them unsuccessful. Using encryption immune to quantum attacks is the only way to stop the total breakdown of our IT infrastructure.
However, what exactly is the cryptography? What is quantum-safe cryptography? And what is the difference between Quantum Encryption and Post-Quantum Cryptography?
Let’s look at the answers to these queries below!
What Exactly is Cryptography?
The study of secure communication methods, such that only the message’s sender and intended receiver can read its contents, is commonly called cryptography. Examples of encryption methods to hide information in images include microdots and merging.
The fields of math, computer science, electrical engineering, communication science, and physics are all combined in modern cryptography. E-commerce, chip-based payment cards, digital currencies, computer login credentials, and military communications depend significantly on cryptography.
Numerous legal difficulties have arisen because of the development of cryptographic technology in the Information Age. Many nations have classified cryptography as a weapon and banned or restricted its use because of the possibility of espionage and rebellion. In digital media, cryptography is also crucial.
In the article below, we will go through quantum cryptography in depth and point out its differences from post-quantum cryptography.
What is Quantum Cryptography?
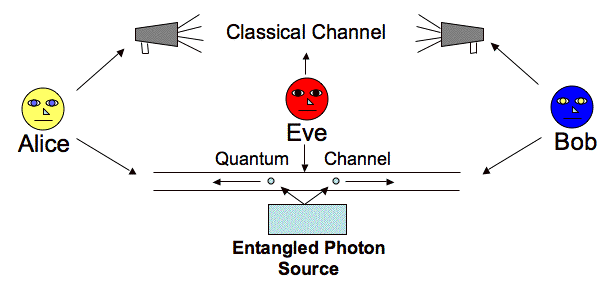
Quantum cryptography studies using quantum mechanics techniques to carry out cryptographic operations. Quantum key distribution, which provides an information-theoretically secure solution to the critical exchange challenge, is the most widely recognized application of quantum cryptography. These encryption techniques are supposedly “unbreakable” since they rely on physical principles rather than mathematical proofs.
Creating and distributing shared keys through quantum key distribution ensures that no third parties have observed. Several natural phenomena apply to quantum states and offer quantum information an additional layer of protection. When measured, quantum states collapse.
The quantum states would no longer be in a superposition if an attacker attempted to read out data through an entanglement-based protocol.
A quantum state cannot be duplicated, according to the no-cloning theorem for quantum physics. As a result, an attacker could not replicate the quantum information being communicated and manipulate their copy.
Quantum cryptography is a successful turning point in the information security business, at least in principle. However, no cryptographic technique will ever be 100 percent Secure. Because it relies on several crucial assumptions, quantum cryptography is only conditionally secure in practice.
Exactly How Does Quantum Cryptography Work?
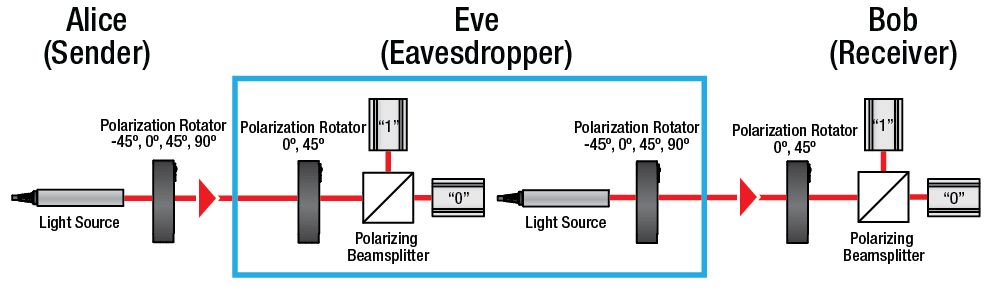
Using a filter (or polarizer), the transmitter emits photons with one of four random polarisations and bit designations: vertical, horizontal, 45° right, or 45° left.
The photons are directed towards a receiver, which employs two beam splitters (horizontal/vertical and diagonal) to “read” the polarisation of each photon. The receiver must guess which beam splitter is used for each photon because it still determines which to use.
The receiver notifies the sender of the beam splitter utilized for each photon in the stream of photons after it has been transmitted, and the sender compares this information to the polarizer sequence used to transmit the key. The bit sequence that results from eliminating the photons read with the wrong beam splitter serves as the key.
What is Quantum-safe Cryptography?
Quantum cryptography truly bases its security on quantum mechanical concepts. These encryption techniques are supposedly “strong” because they rely on physical principles rather than mathematical proofs. Of course, side-channel attacks are an exception.
In the era of quantum computing, quantum-safe encryption protects confidential information, communications, and access. On a computer, cryptography is used almost constantly. Because of this, most of the time, criminals cannot read your emails, access your medical information, post on social media, remotely turn off your vehicle’s engine, or interfere with the electrical system of your city.
Modern cryptography is so practical that when protected data or systems are compromised, it virtually never happens because the encryption was broken. Most breaches are caused by human errors, such as when someone unintentionally shares a password or leaves a backdoor open to a secure system.
Modern encryption standards, such as 2048-bit public keys, are comparable to the most robust vaults: they are virtually hard to break into unless someone leaves a key lying about outside. However, things will change in the age of quantum computing. Any 2048-bit vault might be opened by a malicious party with a powerful enough quantum computer, allowing them access to the data it is designed to secure.
Although we do not yet know the precise date when quantum computers will be strong enough to break 2048-bit cryptography, several scientists have created timelines based on the information we already have. The first security breaches might occur as early as 2030, according to the National Institute of Standards and Technology Report on Post-Quantum Cryptography.
The goal of quantum-safe cryptography is to rebuild the cryptographic vault to make it secure against quantum and classical attacks.
How Significant is Quantum-Safe TLS?
A powerful quantum computer will soon be able to execute the “SHOR” algorithm, which can quickly break existing TLS communication methods (RSA/ECC) as quantum computing expands and advances. While there are now no massive quantum computers accessible, when they are, any TLS data-in-transit that has been monitored and stored could be compromised. Data has a lengthy shelf life.
Hence, Key Protect must enable quantum-safe cryptographic techniques to safeguard TLS communications.
Key Protect has provided the capability to employ a quantum-safe enabled TLS connection to make sure that your data is secure during the key exchange procedure to maintain the resilience of your in-transit data.
Recommended: Google Chrome 116 Introduced Hybrid Post-Quantum Cryptographic Algorithm for HTTPS
Algorithms for Quantum-Safe Cryptography
Most key-derivation algorithms (like bcrypt, Scrypt, and Argon2), MAC techniques (like HMAC and CMAK), and cryptographic hashes (like SHA2, SHA3, and BLAKE2) are quantum-safe (just marginally impacted by quantum computing).
- To be quantum-safe, use 384 bits or more (256 bits should be sufficient for a considerable duration).
Quantum-safe symmetric ciphers include AES-256 and Twofish-256.
- Employ keys of 256 bits or more instead of 128-bit AES
Hashes are Quantum Safe.
Quantum-safe cryptographic hashes include such like SHA2, SHA3, and BLAKE2:
- Finding a collision for a 256-bit hash on a conventional computer requires 2256 steps (using the birthday attack), yet SHA256 has 2128 crypto-strength.
- Hash collisions in 2256 operations could be identified with quantum computers. However, this needs to be clarified.
- Theoretically, finding a collision between SHA256 and SHA3-256 may require 285 quantum operations, but it might be far more expensive in practice.
Important Note:
- SHA256 and SHA3-256 could be quantum-safe algorithms.
- SHA384, SHA512, and SHA3-384, SHA3-512 are Quantum-safe.
- Most 256-bit symmetric ciphers are quantum-safe.
- AES-256, ChaCha20-256, Twofish-256, and Camellia-256 are the quantum-safe ciphers.
What is Post-quantum Cryptography?
“post-quantum cryptography” commonly refers to public-key encryption techniques developed to protect against attacks using quantum computers.
Post-quantum cryptography, also known as quantum-proof, quantum-safe, or quantum-resistant cryptography, refers to cryptographic methods (often public-key algorithms) immune to a quantum computer’s intrusion. By updating current mathematical-based methods and standards, post-quantum cryptography prepares us for the future of quantum computing.
The advancement of cryptography techniques can be implemented using conventional computers of the present, but they will be secure against attacks from quantum ones shortly.
Why is Post-quantum Cryptography Required?
There is a mathematical relationship between public and private keys. Modern public-key encryption methods rely on calculations that are challenging for ordinary computers, including determining the prime factors of huge numbers.
The way quantum computers handle information enables them to perform certain computations inaccessible to traditional computers.
The following reasons explain why post-quantum cryptography is necessary.
- When User A wishes to transmit a message to User B, online contact between User A and B frequently uses public-key cryptography. Alice makes a public and private key pair to do this in private. User A encrypts a message that can only be decrypted by User B’s private key using the public key.
- Because only Alice has the private key, but everyone else has access to her public key, traditional computers find it challenging to recognize a private key. The mathematical issues related to the connection between private and public keys currently need to be solvable by traditional computers.
- Because of the distinctive way that quantum computers analyze information in comparison to traditional computers and the ability to do different computations, they can estimate a private key incredibly rapidly. It has an algorithm that can quickly determine a private key only based on the public key.
- Without new benchmarks for public-key cryptography, quantum hackers can listen in on many online conversations and tamper with a system that depends on confidence. This could undermine trust and privacy online.
The Significant Difference between Quantum Cryptography and Post-Quantum Cryptography
The key differences between quantum cryptography and post-quantum cryptography are shown in the following table.
| Quantum Cryptography | Post-Quantum Cryptography | |
| 1 | “Quantum cryptography,” sometimes known as “quantum encryption” or “quantum security,” is the term used to describe the use of quantum physics in the science of cryptography. | A group of techniques known as post-quantum cryptography are usually public-key algorithms and have been developed to resist an attack from a quantum computer. |
| 2 | Specialized hardware will be required for implementation. | Most solutions won’t require specialized hardware but rely only on software. |
| 3 | Quantum physics says a quantum channel cannot be successfully intercepted without detection. | Algorithms can be examined to determine how reliable they are, but there is no guarantee that someone won’t eventually find a way to defeat them. |
| 4 | It only uses optical communication through an optical fiber in open space. | It works with any digital communications media, including optical communications and RF wireless networks. |
| 5 | Higher expenses because new communications infrastructure and technology are required. | Solutions for software-based synthesis will be reasonably priced. |
| 6 | Although it’s unlikely, it’s feasible that it could be used for digital signatures. | Many versions of the standards are currently being developed for the usage of digital signatures. |
| 7 | There are only a few choices. Use should only be made of line-of-sight nodes. | Appropriate for communicating via any mobile device. |
FAQ’s
Which Kind of Encryption is Quantum-safe?
Quantum-safe symmetric ciphers include AES-256 and Twofish-256. Most well-known public-key cryptosystems, including RSA, DSA, ECDSA, EdDSA, DHKE, ECDH, and ElGamal, are quantum-broken! Most digital signature algorithms, including RSA, ECDSA, and EdDSA, are quantum-broken.
Is AES Encryption Quantum-safe?
Although AES is secure against conventional computers, quantum attacks can still exploit it. It’s crucial to comprehend how AES functions and why it is susceptible to quantum attacks.
What is Quantum-safe Security?
Sensitive data, communications, and access are secured in the age of quantum computing because of quantum-safe cryptography. Cryptography is used in almost all of your computer-related activities.
What Distinguishes Quantum-safe from Quantum-secure?
To combat the risk posed by quantum computers, both quantum-secure and quantum-safe solutions will be required. However, quantum-secure solutions are now available to secure long-term data against attacks that can be harvested and decrypted in the future. In contrast, quantum-safe solutions are still being developed for current threats.
Which Encryption is the most Difficult to Break?
The most muscular and reliable encryption method currently used in commerce is AES 256-bit encryption. AES 128-bit encryption has never been broken, even though AES 256-bit encryption is theoretically more challenging to penetrate than AES 128-bit encryption.
