What Is a Certificate Revocation List? [CRL Explained]

The foundation of Public Key Infrastructure (PKI), which secures billions of online transactions, is the X.509 digital certificate standard.
But what will happen if these certificates or the keys that go with them have an issue? They need to be revoked since it is clear that they can no longer be trusted. A certificate must be added to a certificate revocation list (CRL) so as for users to be informed that it has been revoked.
We have already seen massive certificate revocations take place in PKI history. For instance, in 2019 Apple, Google, and GoDaddy canceled millions of certificates because their serial numbers were 63 bits rather than 64 bits.
Due to an issue in their code, Let’s Encrypt also carried out a significant amount of certificate revocations in March 2020.
What Is a Certificate Revocation List (CRL)?
A Certificate Revocation List, or CRL, is a list of digital certificates that have been revoked or considered invalid before their expiration date.
A digital certificate—a digital identifying document that protects internet communication—is issued by a trustworthy third-party certificate authority (CA). Applications verify the validity of an SSL/TLS certificate using a CRL, an essential component of public key infrastructure (PKI).
In other words, CRL is a technique for preventing the validation of unwanted certificates. The identities of certificates that are considered untrustworthy have been included in the CRL.
Why is Certificate Revocation List Required?
When a CA provides a digital certificate, they expect that the certificate will be used over its complete lifecycle. (Certificates now have a two-year validity; however, for certificates issued on or after 1st September 2020, the duration will be decreased to one year)
But not all certifications remain valid for that long. They occasionally get their licenses canceled too soon; at that point, they join CRLs. This is different from the processes for expired certificates, which CAs revoke, and browsers and operating systems immediately refuse. (Therefore, they aren’t included in the listings of certificates that have been revoked.)
As you can imagine, if customers are unaware that a certain certificate has been revoked, it can cause a lot of issues. A good illustration of one of those issues is The alert notification you saw before that read “Your connection is not private”. Therefore, CAs and CRL providers encompass certificate revocations to their CRLs to make them easier to observe and track.
Why will a CA Include Certificates in a CRL?
There isn’t a universal response to this query. Your website’s certificate may be revoked by a CA for several reasons, including:
- The private key for your certificate is compromised by someone.
- The CA has been compromised from within.
- The certificate holder is no longer trustworthy: The CA may revoke the certificate and add it to the CRL if they conclude that the certificate holder is no longer reliable.
- The CA may revoke a certificate, for instance, if the certificate holder has breached the terms of the certificate agreement or taken part in unauthorized activity.
- The CA must issue a new certificate if any of your organization’s information specified on the certificate is updated or modified.
- A certificate was illegally or fraudulently signed using a stolen key.
- When the CA issues a certificate improperly, it replaces it with a new one.
What Is Included in a Certificate Revocation List?
Although CRLs could vary, the following are a few elements that are frequently included:
- Name of CRL issuer
- The extension (s) of the certificate
- the common name, or CN
- Date of the next CRL issued.
- Algorithm for the certificate’s signature
- Certificate serial number
How does a Certificate Revocation List (CRL) Work?
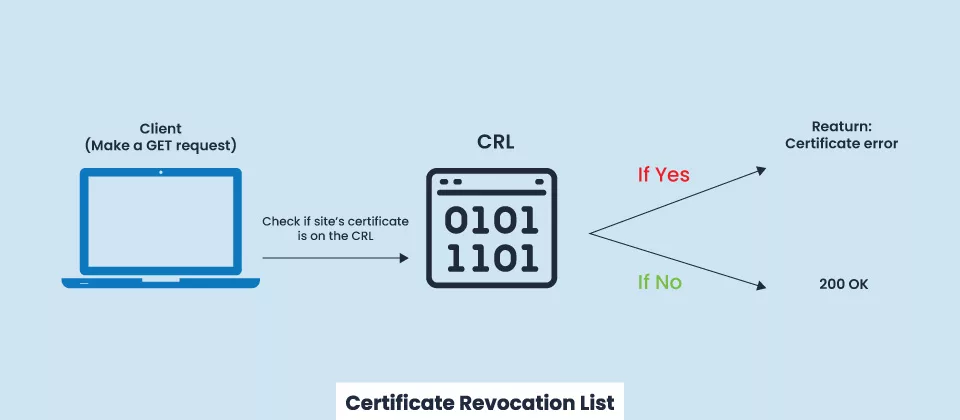
The certificate revocation list is simply a broad compilation of certificates that have been blocked and maintained up to date by a certain certificate authority.
Following the steps listed below, a browser sends a request to a page that has an SSL/TLS certificate.
- An HTTPS-enabled page receives a GET request.
- Upon receiving that request, the certificate authority provides a list of all revoked certificates.
- The CRL is then analyzed by the browser to make sure that it does not include the certificate for the requesting site.
It might be challenging to maintain a certificate revocation list. It needs frequent updates and modifications and is consequently prone to mistakes.
Furthermore, depending on when the CRL was recently updated, it’s conceivable that a browser request to a site that ought to have a revoked certificate receives a green light since the list wasn’t updated in time.
How do Browsers Check for Certificate Revocation?
Browsers verify the legitimacy of the server they are connecting to before establishing a safe, encrypted connection. They verify the SSL/TLS certificate to achieve that.
A browser can accomplish this in one of two ways:
- For the questioned certificate, manually check the CRL. The client contacts the CA and downloads a copy of its list of certificate revocations. After that, it has to look through the full list in search of the particular certificate. This procedure is slow and tedious. The client downloads updated CRLs daily to improve performance.
- To check the status of the revocation of a given certificate, send an OCSP request to a specific OCSP responder over the CA’s revocation server. After receiving one of the three certificate statuses answers from the OCSP responder – whether “good”, “revoked”, or “unknown”—the user can respond suitably.
A brief note on OCSP: OCSP refers to Online Certificate Standard Protocol. To obtain information about the status of a digital certificate’s revocation, one can utilize OCSP which is specified in RFC 6960.
Recommended: Differences between CRL vs OCSP
OCSP is easier and quicker than CRLs because, the certificate verification is handled by the CA rather than your PKI, transferring the duty to them. It is also considerably carrying lesser data and simpler for the CA to comprehend.
The Shortcomings of Client-based Certificate Revocation Status Checks
The client (browser) is responsible for the two techniques previously discussed for determining the status of the certificate revocation. To connect to a certificate, the browser must first determine if it has been revoked.
There are additional challenges besides making browsers check the validity of the certificates, including:
- Due to its vulnerability to replay attacks and lack of encryption requirements, OCSP put up issues with security and privacy.
- CRLs and OCSPs are reliant on the infrastructure of a CA. The dependability of both practices is compromised by relying on a CA that has concerns with availability.
- CRL lists expand, and CAs publish new lists every day. The browser might not have the most recent CRL since CRL-based verification methods demand certificate revocation status checks for each connection.
- Both techniques (which are mentioned above) demand a lot of the client’s resources. They increase latency and use a lot of resources.
- False negatives- The client-based certificate revocation verification might ignore certain revoked certificates, which can give the impression that a false sense of security.
- High computational needs – Checking the status of certificates for revocation on the client side can be pricey in terms of processing, especially if several certificates are being checked. The authentication procedure may be severely slowed down as an outcome.
Online Certificate Standard Protocol (OCSP) Stapling
Due to the drawbacks, the market has created an additional option called OCSP stapling, a web server-based certificate revocation status check. OCSP stapling shifts the burden of processing OCSP requests from the user’s client to the web server.
This method uses fewer resources and gives the end user a more effortless experience. Additionally, it’s able to deal with the data leaking challenges that the client-based OCSP status check approach has.
The main advantages of OCSP stapling over CRLs are that it uses less bandwidth and enables real-time status checks.
Conclusion
Finally, Certificate Revocation Lists are essential for establishing trust in Internet interactions and transactions. However, they do come with several challenges, some of which were covered in this article. The best method to address these issues is to maintain an effective certificate management program.
FAQ’s
What are CRLs Certificate Revocation Lists?
The term “certificate revocation list” (CRL) refers to a list of digital certificates that have had their issuing certificate authority (CA) revoke them before the actual or designated expiration date of the certificates.
What is Meant by Certificate Revocation?
The act of invalidating a TLS/SSL certificate before its specified expiration date is known as certificate revocation. When a certificate’s private key appears to have been compromised, it should be immediately revoked. When the domain for which it was given is no longer active, it should also be revoked.
What Format is the CRL Certificate Revocation List?
A few global information elements, including the version, signature algorithm, issuer name, CRL issue date, and next update date, are also included in the CRL. X. 509 v2 Certificate Revocation Lists are the most prevalent type and are often encoded in DER (binary) or PEM (text) formats.
How do I Revoke a CRL Certificate?
- Go to the System > Cert Manager tab and click the Certificate Revocation button.
- Find the CRL to modify in the list.
- At the end of the row, choose the CRL by clicking the fa-pencil icon.
- If the certificate is being revoked, choose a reason from the drop-down menu.
- To revoke the certificate, choose the certificate(s) from the Revoke Certificates list
- Enter one or more certificate serial numbers into the Revoke by Serial field, distinguishing them with spaces.
- Select fa-plus Add and the certificate(s) will be added to the CRL.
What happens when a Certificate is revoked?
When you revoke an SSL certificate, HTTPS is instantly removed from the website. Your website could display errors or temporarily go offline depending on your Web host.
