Encryption: Beginner’s Guide to Understand What is it & How it Works

From Plain Text to Cipher Text: Beginner’s Journey into Encryption
In today’s world, where technology has taken over every aspect of our lives, it’s essential to secure our online presence. Cyberattacks are on the rise, and we are all vulnerable to them. This is where Encryption comes in.
Encryption is like a secret code that only the intended recipient can decipher. It’s the process of converting plain text into an unreadable form to prevent unauthorized access. It ensures the confidentiality, integrity, and authenticity of our data. Be it our confidential emails or online purchases, it has proven to be a safe pass.
Think of encryption as a lock for your digital information. Without it, anyone can access or steal your sensitive data. But with encryption, you can rest assured that your information is safe from prying eyes. So, let’s all decode it and understand how it helps secure our online presence.
What is Encryption?
Encryption is a security technique that transforms plain text into an unintelligible form called ciphertext. This is achieved by using a mathematical and secure hashing algorithm & a key to perform a series of complex operations on the plain text. The ciphertext can only be transformed back into plain text using the key, which is required to be kept secret.
Key Components
- Plaintext: This is the original message or data that needs to be protected.
- Encryption Algorithm: This is a mathematical formula used to convert plaintext into ciphertext.
- Key: This is a secret value used by the encryption algorithm to encrypt the plaintext. It is essential to keep the key secret to ensure the security of the encrypted data.
- Public Key: A public key is used for encryption and is made available to everyone. It is used to encrypt plaintext, which can only be decrypted using the corresponding private key. It is widely distributed, & anyone can use them to encrypt data and send it to the intended recipient.
- Private Key: A private key is used for decryption & it is kept secret by the owner. It is mainly used to decrypt ciphertext that has been encrypted using the corresponding public key.
- Ciphertext: Encrypted message or data produced by the Encryption Algorithm. It appears as a series of random characters and cannot read without the correct decryption key.
- Decryption Algorithm: This is a mathematical formula which can convert the ciphertext back into the original plaintext.
- Decryption Key: A secret value used by the decryption algorithm to decrypt the ciphertext and reveal the original plaintext.
What is the Importance of Encryption?
It is a critical tool in ensuring the security and privacy of digital communication in the modern world. With the rapid increase in digital communication & storage, the risk of cyber threats and security breaches are also increasing. It can protect sensitive information from unauthorized access by scrambling the data in a way that can only readable by someone with the appropriate decryption key. So, if an attacker gains access to the encrypted data, they would not be able to read or make sense of it without the decryption key.
Some of the important benefits of encryption in cybersecurity include the following:
- Confidentiality: It ensures that sensitive information remains confidential & is only accessible to authorized persons. If an attacker intercepts the ciphertext, they will not be able to read it without the key.
- Security: It also helps to prevent unauthorized access, data breaches, & identity theft as it makes difficult for hackers and cybercriminals to access sensitive information.
- Compliance: Many industries/organizations use encryption by law to protect private & confidential data, such as personal health information or financial data.
- Trust can help build trust between users, especially when sensitive information shared, such as in financial transactions or legal documentation.
- Data integrity: It helps to ensure that data is not alter/tamper during the data transmission and ensures accuracy and reliability.
- Assurance: Knowing that sensitive information remains secured by encryption assures both individuals/organizations, reducing the risk of data loss or theft.
Examples of Encryption
Here are some of the real-world applications of encryption:
- Online Banking: When a user logs in to their bank’s website to access the account, their personal or financial information remains encrypted using SSL/TLS encryption. It assures their login credentials & transactions are secure and hackers cannot intercepted it.
- E-Commerce Transactions: When a user buys something online using a credit card, the website or app they are using will protect their financial information using encryption. Hence, credit card details or other sensitive information remains encrypted, making it difficult for anyone to access them without permission. The website/app they are using will also store the credit card details securely so hackers or other unauthorized parties can’t steal them.
- Email: Email providers make use of encryption mechanism to secure the messages sent between two users. This is important while sending sensitive information, as passwords/financial data, which should not be accessible to unauthorized parties.
- Virtual Private Networks: VPN encrypts all internet traffic between a user’s device & VPN server, protects from interception by cyber criminals. This is particularly useful for remote workers who need to access company networks from outside the office.
What are the Types of Encryption?
There are two types of encryption: symmetric encryption and asymmetric encryption. Let’s see both in details.
Symmetric Encryption:
Symmetric Encryption is a type of encryption where the same key is used for both the encryption & decryption of a message or data. The encryption key is used to convert the plaintext (original message) into a ciphertext (encrypted message). The decryption key is used to convert the ciphertext back into plaintext. Hence, both the sender and receiver of the message must have the same secret key to communicate.
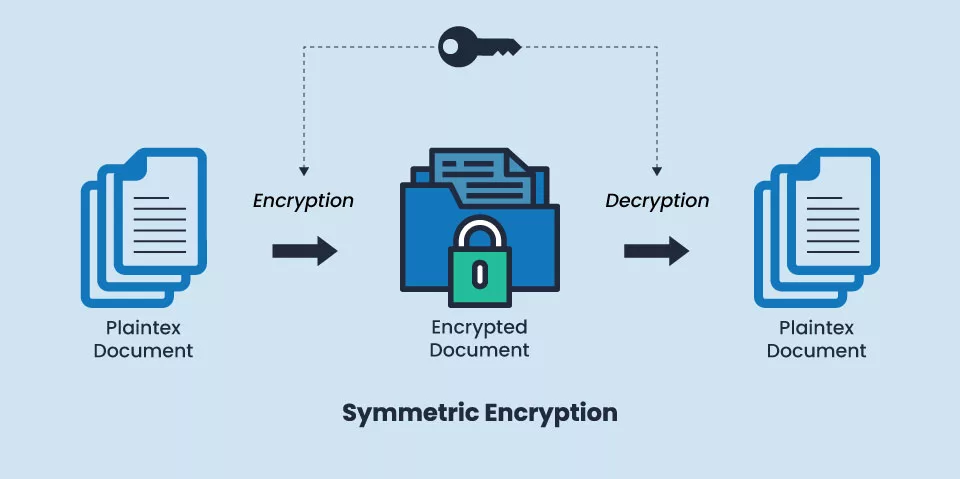
It is mainly used when a large amount of data needs to be encrypted quickly, as it is generally faster than asymmetric encryption. Examples of uses for symmetric encryption include securing emails, documents, & files on a local computer or network.
However, It is also more vulnerable to attacks than Asymmetric Encryption because if the secret key is compromised, all the encrypted data can be accessed by the attacker. To mitigate this risk, it is important to keep the secret key as secure as possible, limit access to the encrypted data, and periodically change the secret key.
One way to strengthen Symmetric Encryption is to use a longer key length, which increases the number of possible keys & makes it more difficult for an attacker to guess the key. Another method is to use key exchange algorithms, such as Diffie-Hellman, to securely exchange the secret key between the sender and receiver without revealing it to anyone else.
Asymmetric Encryption:
Asymmetric Encryption, also known as public key cryptography, is a type of encryption where two different keys are used for encryption & decryption purpose. A public key & a private key. The public key is available to anyone who wants to send an encrypted message, while the private key is kept secret and is used to decrypt the message.
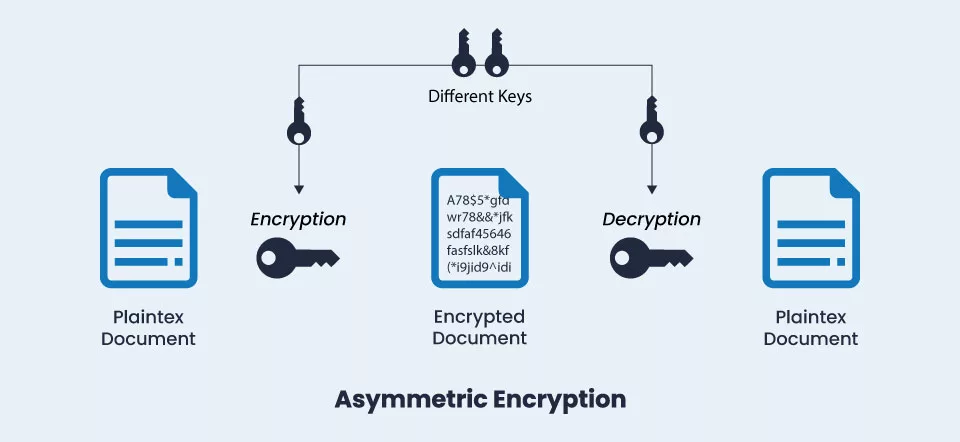
When a sender sends a message to a receiver, they first obtain the receiver’s public key. The sender then uses the public key to encrypt the message before sending it to the receiver. Once the receiver receives the encrypted message, they use their private key to decrypt the message & read it.
It is more secure than symmetric encryption because the private key is never shared and only the intended recipient can decrypt the message. As a result, Asymmetric encryption is commonly used in when security is of the utmost importance, such as online banking, social media, healthcare, government agencies & e-commerce transactions.
Learn more about Difference Types of Encryption Algorithm.
Common Application of Encryption
SSL is the common area where encryption mostly used is SSL Certificate.
Secure Sockets Layer are encryption protocols that can secure internet communication between devices. It creates secure channel between two devices known as a ‘handshake,’ where both devices agree for the encryption method and the encryption key to use. Once the handshake is complete, data is encrypted & decrypted as it is transmitted between the two devices.
SSL/TLS is used for a variety of purposes, including:
- Online banking and financial transactions
- E-commerce transactions
- Secure login pages (such as those used by online services and applications)
- Secure file transfers
- Virtual private networks (VPNs)
- Boost SEO Score & Brand Reputation by enabling SSL
Encryption and Website Security
Here is an overview of how encryption is used to secure websites, the importance of implementing encryption, & how website owners and administrators can implement encryption on their sites.
How is Encryption Used to Secure Websites?
As we already know, encryption is achieved with the help of SSL certificate, which encrypts data using the PKI (Public Key Infrastructure). Verified Certificate Authorities like Certera, Sectigo and Comodo can issue the SSL Certificate. Website owners can obtain them and install them on their servers to enable secure communication with users’ browsers. When a user visits a website with SSL enabled, their browser checks the website’s SSL certificate to ensure it’s valid and hasn’t been tampered with and then establishes a secure connection with the server.
Concluding Thoughts
Encryption has assumed a pivotal role in safeguarding sensitive information. The absence of encryption exposes data to risks of interception by cybercriminals who could potentially pilfer personal information, financial data, and other critical details. It adds an additional layer of security, which significantly raises the level of complexity and difficulty involved in breaching the security of the data. Therefore, it is crucial to acknowledge and appreciate the importance of encryption in ensuring the security and integrity of digital communication, be it sending a message or making a purchase online.
