Decoy Dog Malware Toolkit uncovered after analyzing 70 billion DNS Requests
Explore the detection methodology employed in uncovering the Decoy Dog Malware Toolkit.
A novel enterprise-targeting malware toolkit named ‘Decoy Dog’ was observed after examining strange DNS traffic that differed from regular internet activity,
Decoy Dog enables malicious users to escape normal detection methods through smart domain aging and DNS query dribbling to establish a good reputation with security providers before switching to supporting criminal activities.
Decoy Dog is a multi-stage attack that targets financial institutions, hospitals, and government entities, among other organizations. The toolkit is intended to fool security software and firewalls by masquerading as legitimate network traffic. It consists of remote access trojans, keyloggers, and backdoors. Decoy Dog can capture sensitive data, like login passwords and financial information, and transport it to command-and-control servers controlled by the attackers once inside a targeted network.
Infoblox, a cybersecurity organization, uncovered and exposed this significant security risk.
According to Infobox, Decoy Dog’s DNS fingerprint is exceptionally unusual and peculiar among the internet’s 370 million active domains, which makes it easier to figure out and track. As a result, the research into Decoy Dog’s infrastructure swiftly led to the identification of various command and control (C2) domains linked to the same activity, with most communications from these servers coming from Russian servers and strategically targeting organizations all around the world.
The researchers at Infobox found the toolkit in early April 2023 as part of their daily inspection of over 70 billion DNS records for signs of unusual or suspicious behavior.
Customers of the company’s BloxOne® Threat Protection are secured and protected from these dangerous websites. Renée Burton, Infoblox’s Head of Threat Intelligence Group, published the news on Mastodon last week and will explain more about this issue at the RSA Conference, which begins on April 25. On April 20, the organization is going to provide more details on the Decoy Dog Toolkit and the importance of a protective DNS approach.
Further study indicated that the DNS tunnels on these domains had characteristics of a remote access trojan, Pupy RAT, deployed by the Decoy Dog toolkit.
Pupy RAT is an adaptable open-source post-exploitation toolkit renowned among criminal groups due to its secretive (fileless) and stealthy nature, support for encrypted C2 connections, and ability to blend in with other tool users seamlessly. It supports payloads in popular OS such as Windows, Android, macOS, and Linux.
Like other remote access trojans, it allows cybercriminals to execute and implement malicious commands remotely and steal confidential credentials effortlessly.
Further analyses discovered additional domains were being registered and aged for varied durations of time before being spotted in global DNS or Infoblox networks.
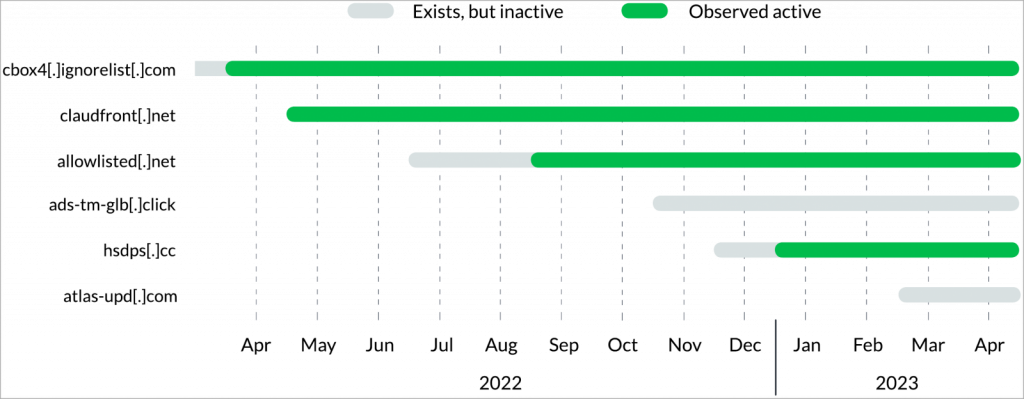
All these domains rely heavily on Pupy RAT and the Decoy Dog toolset.
Usually, Decoy Dog domains have also been identified only on corporate networks, with no indication of activity on devices used by customers.
According to the Infoblox Threat Intelligence Group, nearly no major security vendors have labeled Decoy Dog suspicious or dangerous, with some saying that the domains were low-risk or reputable.
“This multiple-part (DNS) signature gave us strong confidence that the (correlated) domains were not only using Pupy but that they were all part of Decoy Dog – a large, single toolkit that deployed Pupy in a very specific manner on enterprise or large organizational, non-consumer, devices,” Infoblox reported.
Additionally, the researchers noticed a unique DNS beaconing behavior on all Decoy Dog domains that has been configured to generate periodic but extremely uncommon DNS requests.
The identification of Decoy Dog shows the potential of using massive amounts of data analytics to identify unusual behavior in the broadens of the internet.
Infoblox has noticed active C2 communications in sectors such as technology, healthcare, financial, and other fields in the United States, South America, Europe, and Asia, and it is advising various organizations to block domains associated with vicious Decoy Dog, like claudfront[.]net, allowlisted[.]net, ads-tm-glb[.]click, atlas-upd[.]com, cbox4[.]ignorelist[.]com, and hsdps[.]cc.
The Infoblox Threat Intelligence Group is investigating the intentions of the perpetrator, as well as the nature of the hack. The organization uses several custom-built algorithms and DNS-based threat hunting to identify dangerous domains. Infoblox is committed to producing high-fidelity “block-and-forget” DNS intelligence data for use in BloxOne Threat Defence. The organization concentrates on DNS and infrastructure actors and can detect suspicious behavior before other areas of the business are aware of it. Infobox has also provided compromise indications on its public GitHub repository, which may be manually added to blocklists.
