Google Chrome 116 Introduced Hybrid Post-Quantum Cryptographic Algorithm for HTTPS

In a significant leap towards bolstering digital security, Google Chrome has introduced support for a hybrid post-quantum cryptographic algorithm in its latest release, version 116, released on August 15.
An announcement made by Devon O’Brien from the Chromium Project blog post, made live on August 10, signifies this adoption as – “a paramount step in protecting organizational data from quantum computing-based threats while countering present cryptographic challenges.”
As of December 2022, President Joe Biden signed H.R.7535, The Quantum Computing Cybersecurity Preparedness Act, which requires US government agencies to begin moving toward quantum resilient cryptography.
Apart from this, “n” number of multinational corporations, like AWS, IBM, etc., have already incorporated quantum computing algorithms into their systems. But do remember – “Using quantum computers on a large scale can be advantageous; however, it’s the case if used by responsible individuals, not malicious actors.”
What is X25519Kyber768?
Google has been diligently testing new PQC (Post-Quantum Cryptography) algorithms to prepare for a quantum-secure future, and with the official launch of Chrome version 116, it has somewhat achieved it.
The browser (Chrome 116) supports a quantum-resistant algorithm – X25519Kyber768, the first quantum computing hybrid key agreement algorithm available for general purposes.
X25519Kyber768 operates as a hybrid mechanism blending the outputs of two cryptographic algorithms to construct the session key for encrypting most of the TLS connection. Those two algorithms are:
- X25519: An elliptic curve algorithm widely used for key agreement in TLS today. It facilitates the establishment of a shared secret between two parties that can be used to communicate securely over an open connection and uses points on Curve25519 (a type of elliptic curve) to generate a shared secret.
- Kyber-768: A quantum-resistant Key Encapsulation Method (KEM) that’s approximately equivalent to AES-192 regarding data security and NIST’s PQC winner for general encryption.
A client generates a symmetric secret (X25519) for encrypting data in the session. The server’s public key encapsulates the secret using the Kyber-768 KEM encapsulation algorithm. Upon receiving the message, the server employs its private key with a decapsulation algorithm to decrypt the shared key data.
Note: For now, the change is only available on Chrome and Google servers over both TCP and QUIC to ensure compatibility with the ecosystem. It is also important to note that Chrome may use this updated key agreement when connecting to third-party server operators, like Cloudflare, as they add support.
Why is it Important to Protect Data in Transit “Now” Using Quantum-Resistant Encryption?
Before we answer the query mentioned above, it would be better to understand what a quantum computer is. Quantum computers are supercomputers that currently exist only in laboratory environments and use the quantum mechanics principle of superposition to process information differently from classical/modern computers.
Modern computers process bits (1s or 0s) individually, whereas Quantum computers process them differently, using quantum bits (called “qubits”), which can represent 1s and 0s simultaneously, exponentially increasing processing power and shrinking processing times.
It’s currently believed that quantum computers capable of breaking modern classical cryptography won’t become publicly available for another 15 or even 30 years from now. However, it’s crucial to start protecting data traffic today due to the vulnerability of certain cryptography techniques to a specific type of attack known as Harvest Now, Decrypt Later. In this attack, data is collected and stored today, to be decrypted later when cryptanalysis has improved.
In Transport Layer Security (TLS), the encryption algorithms that safeguard the data in transit are deemed secure against quantum cryptanalysis. However, the creation of symmetric keys is not secure against it. As a result, in Chrome, updating TLS to utilize quantum-resistant session keys as soon as possible would enable us to safeguard user network traffic against future quantum cryptanalysis.
In short, “Quantum-resistant encryption or post-quantum cryptography is our best bet against attacks from upcoming quantum computers.”
Why is it Paramount to Merge Post-Quantum and Conventional Algorithms?
Quantum-resistant algorithms are a recent development and their security is yet to be thoroughly tested. Therefore, it is not advisable to entirely replace our current cryptographic algorithms with them. It is still possible that an attacker might find a way to break the algorithm we have chosen, either on a conventional or a quantum computer.
Hence, a hybrid approach combining both post-quantum and conventional algorithms is necessary to ensure maximum security.
How to Verify Whether Your Chrome Browser is Equipped with Post-Quantum Security?
There are two ways to verify whether your Chrome browser (version) is equipped with post-quantum hybrid algorithm security or not. Those two ways are:
- Use the Cloudflare Research PQC Key Agreement checker tool.
- Use Chrome’s Developer’s Tools.
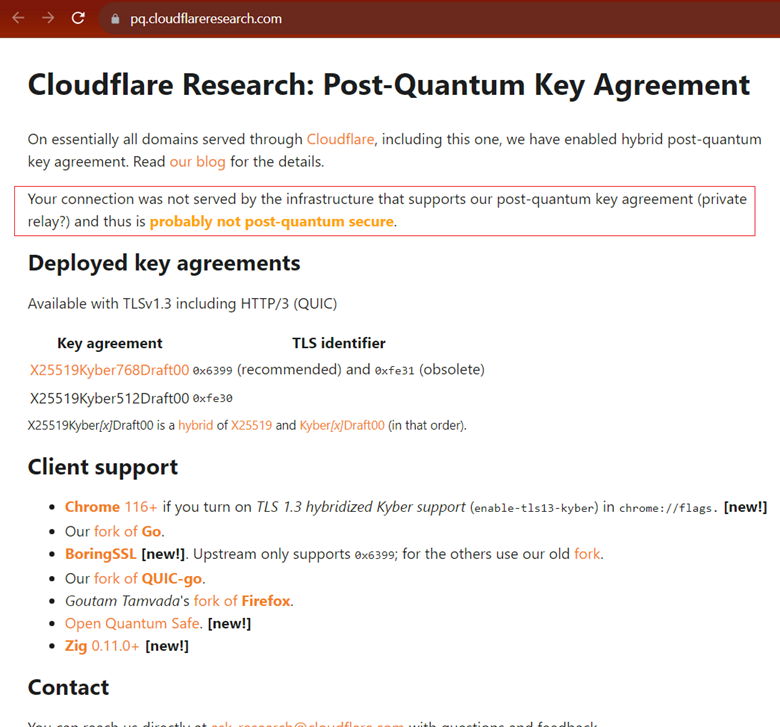
How to Verify Using the Cloudflare Research PQC Key Agreement Checker Tool?
Follow the steps mentioned below to verify the same:
- Open a fresh tab on Chrome.
- In the search bar, type https://pq.cloudflareresearch.com/ and press Enter.
- The page will display the details along with a message stating whether the Chrome browser supports the post-quantum key agreement or not.
How to Verify Using Chrome’s Developer’s Tools?
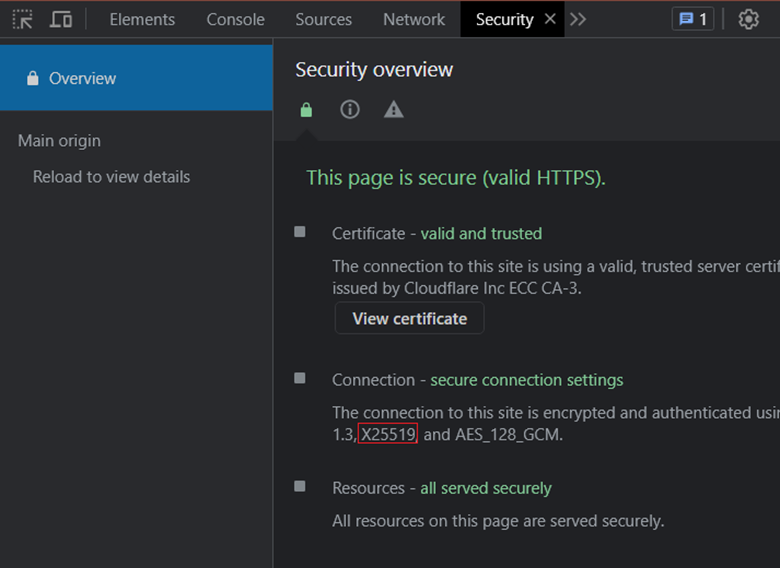
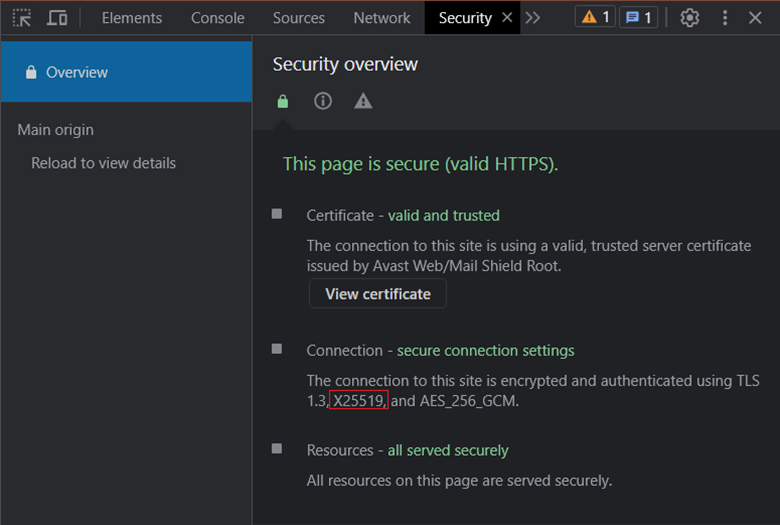
You can use Chrome developer tools to inspect which encryption algorithms Chrome is utilizing for a particular website connection. To accomplish the same, follow the steps mentioned below:
- Open a fresh tab on Chrome.
- Enter the website’s URL for which you want to check the encryption algorithm. (For example – cheapsslweb.com)
- Click on the three vertical dots icon placed in the top-right corner of the tab.
- From the list, select More Tools and click Developer tools.
- Click on the double-right arrowhead icon (>>) if required.
- Click on the Security tab.
- Under the Connection section, you will get the answer to your query.
How to Facilitate Client Support of Kyber in Chrome 116?
Enabling client support of Kyber in Chrome 116 is a straightforward process comprising only seven steps. If you want to enable client support of Kyber in Google Chrome 116, follow the steps mentioned below:
- Open a fresh tab on the Google Chrome browser.
- In the search bar, type chrome://flags.
- Press Enter.
- A new webpage will appear, named Experiments.
- In the Search flags bar, type TLS 1.3 hybridized Kyber support and press Enter.
- From the Default list, select Enabled.
- A message will appear at the bottom: “Your changes will take effect the next time you relaunch Chrome.” (It will only take a few minutes (2-3), and all your existing tabs will be re-loaded.)
- Click the Relaunch button.
Are There Any Deployment Considerations?
Yes, there are! When using Kyber768, an additional kilobyte of data is added to the TLS ClientHello message due to the inclusion of the Kyber-encapsulated key material.
The tests conducted using CECPQ2 showed that most TLS implementations are able to handle this increase in size. However, in some cases, TLS middleboxes may fail if they have hardcoded restrictions on message size.
To help enterprises cope with network appliance incompatibility issues resulting from the rollout of new algorithms, administrators can temporarily disable Kyber768 in Chrome by utilizing the PostQuantumKeyAgreementEnabled enterprise policy, which is available starting in Chrome 116.
But, doing this will be just a temporary fix, and therefore, administrators should work with the affected products’ vendors to ensure that any bugs causing incompatibilities are promptly resolved.
As a final consideration for deployment, it should be noted that both the Kyber768 and Kyber specifications are currently drafts and may undergo changes prior to finalization, causing changes to Chrome’s implementation.
Conclusion
Deploying post-quantum cryptography is crucial and should occur as soon as possible. This is not only necessary to prepare us for the advent of large-scale universal quantum computers but also to ensure that data currently encrypted with standard algorithms remains secure against future decryption attempts.
