Largest DDoS Attacks Reported till Today

Understanding the 7 Largest DDoS Attacks in the History
Few types of criminal activities on the Internet are more annoying and more difficult to avoid. Distributed denial-of-service (DDoS) attacks fall under such a category. These attacks can bring down even the most robust websites by overloading servers with more requests than they can manage. Servers collapse when they cannot meet the requirement for junk requests, and it can take hours to recover them. Let’s understand more about how these attacks occur and ways to prevent them.
What is a DoS Attack?
A Denial-of-Service (DoS) Attack is a cyber-attack in which a malicious user attempts to make a computer or other device inaccessible to its intended clients by interfering with the targeted system’s regular functionality. DoS attacks typically work by overloading or saturating an intended computer with illegitimate requests until normal traffic cannot be handled, which leads to a denial of service to other legitimate users. It can be identified using a single computer to initiate the disruption (As shown below figure).
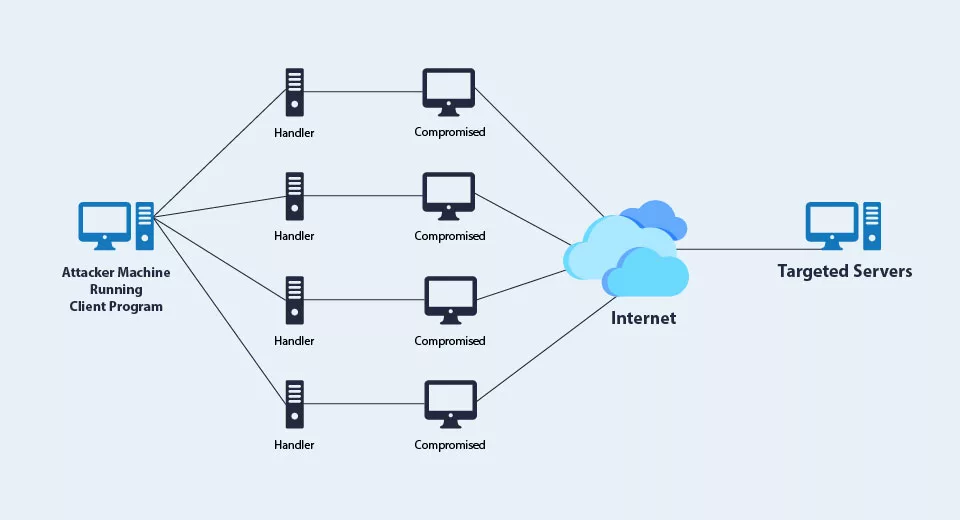
DDoS vs. DoS Attacks: Know What is the Difference!
A DDoS attack is a distributed version of a DoS attack, a type of cyberattack in which various compromised systems attack a single system, typically to overwhelm its resources & render it unavailable to its intended users. It can be initiated from anywhere in the world using any compromised device, which includes laptops, workstations, routers, cell phones, and various internet-connected machines.
It is essential to understand the difference between both attacks. Since just one word separates the two, the nature of these attacks varies significantly.
- Precisely defined, a typical DDoS attack controls multiple distributed machines between the attacker and the victim into executing an unsuspecting attack using legitimate behavior.
- A classic DoS attack does not employ many distributed machines or concentrate on devices between the attacker and the organization. These attacks also do not often use several internet devices. In this attack, a single system targets the victim system.
Nature of DDoS Attack Detection
The Difficulty of Detection: Since a DoS originates in a single location, it is easy to identify and terminate the connection. A capable firewall can identify this. On the contrary, a DDoS attack originates from several remote locations, concealing its source.
Attack Speed: Since a DDoS attack starts from numerous locations, it can be launched much quicker than a DoS attack originating from a single location. The increased attack speed makes detection more difficult, which leads to increased harm or even a disastrous outcome.
Method of Execution: A DDoS attack coordinates multiple hosts infected with malware (bots), forming a botnet managed by a command-and-control (C&C) server. A DoS attack, on the other hand, is usually carried out from a single computer using an application/program.
Traffic volume: Since a DDoS attack uses multiple remote machines (zombies or bots), it can transmit much more traffic (than DoS) from different locations simultaneously, overloading a server quickly and avoiding detection.
How Does a DDoS Attack Work?
DDoS attacks are carried out using the network of computers associated with the Internet; these networks are made up of PCs & other systems (such as IoT devices) that have been infected with malicious software, enabling a malicious user to influence or compromise them remotely. These infected devices are known as zombies (or bots), & a network of bots is known as a botnet. After establishing a botnet, the attacker can direct an attack by transmitting remote commands to each zombie.
When the botnet targets a network or victim’s server, every single bot (or zombie) transmits requests to the target’s IP address, possibly overloading the server or network and causing an interruption of service to normal traffic, which leads to denial of service to legitimate users. Since each bot is a legitimate network device, discriminating between attack traffic and regular data can be challenging.
What are the Common Types of DDoS Attacks?
Categorizing DDoS attacks into three as
- Volume-Based Attacks
- Protocol Attacks
- Application Layer attacks
Volume-Based Attacks
Examples of attacks flood the target with massive amounts of traffic, making it difficult or impossible to access. The attack’s goal is to saturate the bandwidth of the targeted system, and the attack magnitude is measured in bits per second (Bps). UDP floods, ICMP floods, and DNS escalation assaults are some examples.
Protocol Attacks
This attack uses server resources or intermediary communication devices like firewalls and load balancers, and it can be measured in packets per second. (Pps). Examples include SYN floods, fragmented packet assaults, Ping of Death, Smurf DDoS, and other threats.
Application Layer attacks
This type of attack aims at the application layer instead of the network layer. Attackers exploit web applications’ vulnerabilities and misuse platform resources, causing the system to slow down, crash, or become unavailable. The magnitude of the is measured in Requests per second. Examples include low-and-slow attacks, GET/POST floods, and attacks targeting Apache, Windows, or OpenBSD vulnerabilities.
Common Types of DDoS Attacks:
- UDP Flooding
- ICMP (Ping) Flood
- DRDoS (Distributed Reflection Denial of Service)
- SYN-Flood Attack
- Low and Slow Attacks
- Zero-Day Attacks
- Internet of Things (IoT) DDoS Attacks
- Mobile DDoS Attacks
Let’s understand each attack in detail.
UDP Flooding
By definition, a UDP floods a targeted system with User Datagram Protocol (UDP) packets. The attack aims to overwhelm random ports on a remote server. This forces the host to keep looking for an application waiting on that port frequently and (if no application is found) respond with an ICMP ‘Destination Unreachable’ packet. This action drains server resources, eventually resulting in the unavailability of services to legitimate users.
ICMP (Ping) Flood
An ICMP flood attack, like a UDP flood attack, overwhelms the intended resource with ICMP Echo Request (ping) packets, usually transmitting packets as quickly as possible without waiting for responses. Since the victim’s servers frequently try to react with ICMP Echo Reply messages, this type of attack can occupy both outward and inward bandwidth, which causes a significant overall system delay.
DRDoS (Distributed Reflection Denial of Service)
This attack benefits services that respond to network traffic directed at a server. For example, an attacker sends a request to a server, which causes it to reply with a significant amount of data, which is then sent to the victim (server).
SYN-Flood Attack
SYN-flood DDoS attack is a form of Distributed Denial of Service attack in which a target network or server is overwhelmed with an inflow of SYN packets. In an SYN-flood attack, the attacker floods the intended server with SYN packets but never completes the 3-way handshake by delivering an ACK message. It causes the server’s connection queue to fill up, rendering it unable to take new connections and, consequently, creating denial-of-service for genuine users.
Low and Slow Attacks
These attacks are slow and constant to go undetected. They transmit fewer requests over time, slowly consuming resources and overloading the system.
Zero-day Attacks
Zero-day exploit refers to the method or technique hackers use to exploit a vulnerability, often through malware, and execute the attack. The phrase is well-known among members of the hacker community, where trading zero-day weaknesses is an everyday activity.
Internet of Things (IoT) DDoS Attacks
With the spread of IoT devices, attackers may penetrate these devices and initiate attacks. Mirai, for example, compromised IoT devices such as routers and CCTV cameras to trigger attacks.
Mobile DDoS Attacks
These attacks target mobile apps or networks, sending traffic to the target via botnets or malware-infected mobile devices.
Examples of the Largest DDoS Attacks Reported
Distributed Denial of Service Attacks is becoming increasingly prevalent & more widespread. The world has seen a nearly 300 percent increase in these attacks yearly. Over the last two decades, some recent DoS attacks have targeted significant brands which provide services to millions of customers. These attacks are expected to continue to increase in number & complexity as botnets and inexpensive DDoS-as-a-service platforms proliferate.
During the COVID-19 pandemic, cybercriminals have had two busy years, with rapidly increasing numbers of DDoS weapons, widespread botnet activity, and some of the largest DDoS attacks ever recorded.
Let’s look at the most famous DDoS attacks that happened to date; our list includes some DDoS attacks that are famous for their intensity, while others are because of their impact and consequences.
- The AWS Attack
- The GitHub Attack
- The Mirai Botnet Dyn Attack
- The Mirai Krebs and OVH DDoS Attacks
- The GitHub Attack
- The Spamhaus Attack
- The Mafiaboy Attack
The AWS Attack (Feb 2020)
This is one of the most recent & massive DOS attacks reported in February 2020. With a peak traffic rate of 2.3 Tbps (Terabits per second), the AWS attack in February 2020 was one of the largest DDoS attacks ever seen. The three-day attack on Amazon Web Services (AWS) infrastructure caused significant disruptions to different AWS services worldwide.
The hackers carried out this malicious activity by leveraging a weakness in the Internet’s Domain Name System (DNS), enabling them to transmit a massive amount of data to AWS servers. The attack has overburdened the computers, which led to slower load speeds and interrupted service for many users. AWS rapidly reacted to the attack by deploying mitigation measures to block malicious traffic and secure its customers. AWS also collaborated with law enforcement to identify and capture the culprits.
The GitHub Attack (Feb 2018)
GitHub is a centralized collaboration tool that software developers from all over the globe can use. In 2018, hackers saw a chance to use Memcached, a caching system, to directly transmit 1.3 Tbps of data to the GitHub servers, which shows that they did not use the typical zombie bot army. The Memcached computers enabled the hackers to multiply their attacks by 50,000. This is one of the biggest DDoS attacks GitHub has experienced so far. Because GitHub has powerful DDoS protection measures, the attack endured only about 20 minutes. Within 10 minutes of this malicious event, an alert was triggered, and the protection service stopped the attack before it became uncontrollable.
The Mirai Botnet Dyn Attack (Sep 2016):
In 2016, a botnet, “Mirai,” initiated several DDoS attacks. The Mirai network was built by infecting IoT (Internet of Things) devices with malicious software, like webcams, modems, & other smart devices. The network was then used to initiate massive Distributed Denial of Service (DDoS) attacks on DNS providers, online hosting businesses, and other targets, causing extensive damage. The attacks started in September 2016, with the DNS provider Dyn being the first significant target. The Dyn attack prompted widespread internet outages, with services like Twitter, Reddit, and Airbnb falling offline for several hours. Luckily, Dyn was able to solve the attack within a day. However, the intention of the attack was never revealed.
The Mirai Krebs & OVH DDoS Attacks (Sep 2016):
This botnet was also used to initiate attacks against the KrebsOnSecurity.com website. On September 20, 2016, a DDoS attack with a throughput of more than 620 Gbps was launched against cybersecurity specialist Brian Krebs’ site. Krebs’ website had previously been targeted. Krebs had logged 269 attacks since July 2012, but this strike was nearly three times larger than anything the Internet or his site had seen.
On September 19, the next Mirai botnet attack targeted OVH, one of Europe’s biggest hosting providers, which serves approximately 18 million applications for over one million customers. This attack was aimed at a single unnamed OVH client and was carried out by 145,000 bots, resulting in a traffic load of up to 1.1 terabits per second. It ran for approximately seven days. However, OVH would not be the last Mirai malware casualty in 2016. The Mirai botnet identified a major increase in the potency of an attack. The Mirai network’s magnitude and sophistication were unimaginable, as were the scale and level of the attacks.
The GitHub Attack (Mar 2015)
The largest DDoS attack in history targeted GitHub and lasted for several days. The politically driven attack adapted to DDoS mitigation techniques that had been implemented. The activity started in China and mainly targeted two GitHub projects geared at evading Chinese state censorship, with the goal of putting pressure on GitHub to remove those projects.
Attackers generated malicious traffic by inserting JavaScript code into the computers of all visitors to Baidu, China’s most famous search engine, and infecting other websites that used Baidu’s analytics services with malicious code. Affected browsers transmitted HTTP queries to the targeted GitHub pages.
The Spamhaus Attack (Mar 2013)
Spamhaus is a worldwide non-profit organization that monitors spam and other cyber threats. The attack overwhelmed Spamhaus’ servers, disrupting its services and slowing internet access for millions of users around the globe. CyberBunker, an online hosting firm that Spamhaus had banned for hosting spam domains, launched the attack. CyberBunker reportedly used a botnet, hacked PCs, and IoT devices to initiate the vast DDoS attack on Spamhaus.
The attack escalated at 300 Gbps, making it one of the most powerful DDoS attacks ever documented. In response to the attack, law enforcement agencies in several nations started investigations and arrested some suspects. The attack also focused on the need for improved DDoS security and the significance of cooperation among internet stakeholders to mitigate such threats.
The Mafiaboy Attack (Feb 2000)
A 15-year-old hacker known as ‘Mafiaboy’ took down several reputed websites in 2000, including CNN, Dell, E-Trade, Yahoo!, and eBay, the most renowned search engines in the world. The attack had devastating effects, including stock market chaos.
Michael Calce, a high school student, coordinated the attacks by hacking into the networks of several colleges and using their servers to launch the attack. The fallout of this attack directly influenced many of today’s cybercrime regulations.
Checklist to understand whether a website is fake or real.
What are the DDoS Mitigation Techniques?
The attackers often target high-profile websites, such as those belonging to government agencies, financial institutions, e-commerce websites, and social media platforms. Attackers may target any organization with a significant online presence or rely on its website for revenue or operations. Attackers may also target specific industries like healthcare or online gaming to disrupt services or extort money. As such, having an incident response strategy that allows for malicious activities against an organization is essential. The planning part of an incident response plan includes all activities and measures enacted to avoid and prepare for an attack response.
To minimize the danger and effect of these cruel attacks, you should implement the following defensive steps:
Data Filtering: Data Filtering is detecting and filtering malicious data before it enters the network. Firewalls, intrusion monitoring systems, and other security tools can help.
Load Balancing: Load Balancing helps to spread inbound traffic across numerous computers or networks, lessening the effect of an attack on a single system.
Network Segmentation: Network segmentation divides a network into smaller segments that are simpler to manage and secure. It can help limit the attack’s effect by altering the attacker to a single network section.
Scrubbing: Scrubbing entails sending incoming data to a third-party service provider, where it is filtered to eliminate malicious traffic. The system returns filtered traffic to its initial location.
Blackhole Routing: Blackhole Routing involves redirecting all traffic to a null path, essentially deleting all traffic to the targeted system. It can be an efficient method to mitigate the attack, but it can have unintended effects if not done correctly.
Cloud-based DDoS Security Services: Cloud-based DDoS security services may assist in mitigating attacks by absorbing large amounts of traffic and filtering out malicious traffic before it hits the targeted system.
Additionally, users can hide a Website Security Service Provider who will take care of all attacks and threats.
Conclusion
DDoS attacks are becoming increasingly prevalent and more massive in size. Cybercriminals are employing sophisticated methods to carry out these crimes, and companies must be ready to defend themselves. To mitigate such incidents’ impacts, it is essential to have strong security measures in place, such as using DDoS protection services. The attacks mentioned above emphasize the need for the most robust mitigation methods and the significance of staying vigilant against these ruthless activities.
