Understanding The Difference: Authentication vs. Authorization
Administrators employ two essential information security procedures to secure systems and data: Authorization and authentication.
A service’s identity is confirmed by Authentication, and its access permissions are established through Authorization.
Though they have similar sounds, the two concepts are different yet just as crucial to the security of data and applications. It is essential to recognize the difference. They assess a system’s security when taken as a whole. You cannot have a secure solution unless authentication and Authorization are correctly configured.
What Is Authentication?
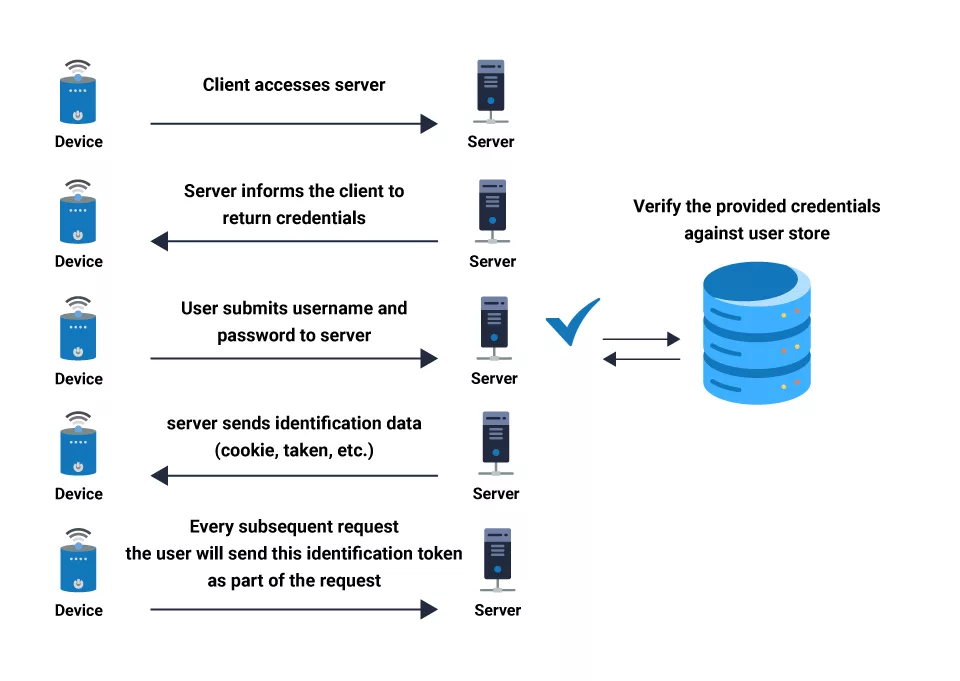
Regarding system security, Authentication is the process of identifying or verifying who someone is, it confirms that users are who they say they are.
Authentication is the first step of identification that determines whether the person is a user or not. It needs usually the user’s login details.
Why is Authentication Necessary?
Verifying that someone or something is who or what they claim to be is the objective of authentication. There are several ways to authenticate. For instance, the art industry includes procedures and establishments that verify a sculpture or painting is the creation of a particular artist.
Governments also employ various authentication methods to prevent counterfeiting of their currencies. Authentication often safeguards valuables; it secures data and systems in the information era.
Types of Authentication
Verifying the identity of people gaining access to a system, website, or application is a critical procedure known as authentication. In today’s digital environment, various authentication techniques provide safe access to sensitive data. The most typical ones consist of:
Password-based Authentication
Users using this conventional technique must enter a unique combination of characters they only know. Although passwords are easy to use, their management may lead to security breaches.
Multiple-Factor Authentication
By combining two or more authentication factors—passwords, biometrics (facial recognition or fingerprint), or one-time codes sent to a user’s registered device—multi-factor authentication (MFA) improves security. This tired strategy significantly decreases the danger of unauthorized access.
Authentication using Two Factors
Two distinct authentication factors are used in 2FA, a subset of MFA, to confirm the user’s identity. This usually includes an SMS or mobile app-generated password and a one-time code.
Biometric Authentication
This innovative technique verifies a user’s identification using distinctive biological characteristics like fingerprints, iris scans, or facial features. Although biometrics provide high security and convenience, privacy issues could arise.
Benefits of Verification/Authentication
Reasonable authentication procedures provide a secure and easy-to-use user experience while providing many advantages to people, companies, and online platforms.
Improved Security Authentication
By preventing unwanted access and shielding private information from prying eyes, improved safety authentication lowers the possibility of data breaches and cyberattacks.
User Self-Assurance and Confidence
Robust authentication procedures boost users’ confidence by reassuring them that the platform or service is secure and protecting their data.
Decreased Identity Theft and Fraud
By requiring users to verify themselves, the likelihood of fraud and identity theft is greatly decreased.
Personalized Access Control
Various authentication techniques can be customized to meet specific security requirements, enabling organizations to provide various user groups with the right amount of access.
What is Authorization?
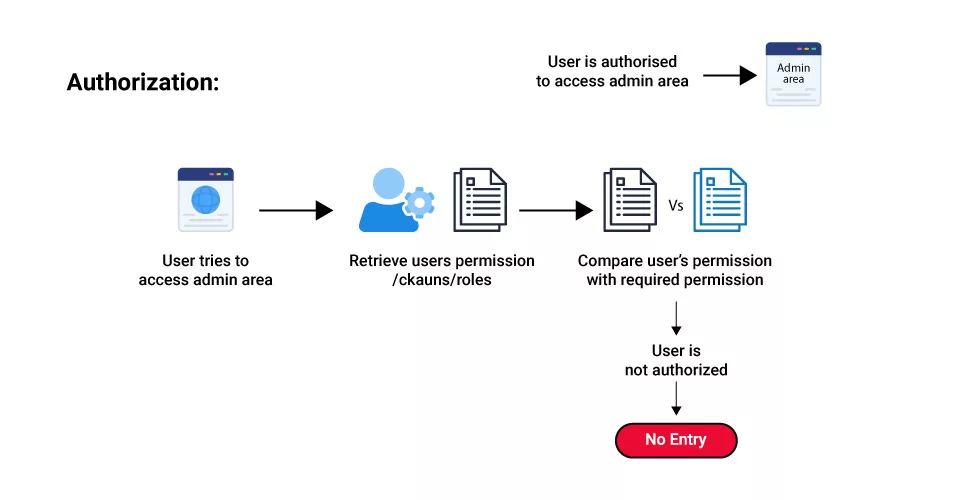
Once a user’s identity has been properly authenticated, Authorization takes place. Providing full or restricted access rights to resources like databases, cash, and other vital information is essential to completing the task.
Determining the resources an employee will have access to is the following stage in an organization, for instance, once they have been authenticated and validated using an ID and password.
Why is Authorization Necessary?
Authorization’s primary objective is to ensure that users have the appropriate amount of access to their roles and security guidelines. Granting access to someone to a resource is known as Authorization. This description can appear cryptic, but plenty of real-world examples clarify what permission entails, allowing you to apply the ideas to computer systems. Homeownership is a prime example.
Types of Authorization
To guarantee that specific people or entities are given the proper access to resources and activities inside a system, Authorization is an essential component of identity and access management. Organizations utilize various authorization systems to manage access and safeguard confidential data.
Authority Based on Roles and Responsibilities
This method assigns access privileges based on jobs or job responsibilities already established inside the company. Individuals are classified into distinct roles, and every function is bestowed with a corresponding set of authorizations that correspond with its assigned duties. This lowers administrative overhead and improves access control, particularly in large businesses.
Authorization Based on Characteristics
This kind of permission assesses access requests according to specific user characteristics, such as department, location, or clearance level. Whether a user’s characteristics fit the requirements for using certain resources or carrying out specific tasks determines whether access is allowed.
Rule-Based Authorization
Access control is enforced by rule-based Authorization according to predetermined guidelines and requirements. The conditions under which access should be allowed or refused are outlined in these regulations. Using rule-based Authorization, organizations may create complicated access controls to meet specific business needs.
Mandatory Access Control (MAC)
A typical high-security authorization approach in military and government contexts is MAC. Strict access constraints set by the system administrator govern how it functions. Users can only access material at or below their clearance level because of the assignment of access privileges based on labels and categories.
Discretionary Access Control (DAC)
DAC gives consumers more control over who gets access to their own resources than MAC does. Every resource has an owner who has the authority to decide who else can use it and to what extent. DAC is frequently utilized in less secure settings where people have greater control over their data.
Role-Based Access Control (RBAC)
Managing user access based on roles and the rights accompanying them is the primary goal of role-based Authorization, or RBAC. Enabling administrators to manage roles and provide or revoke rights to whole user groups improves access control.
Advantages of Authorization
Robust authorization procedures have several benefits that improve an organization’s overall access control plans and security posture.
Greater Protection
Only authorized users can access resources and carry out allowed actions thanks to Authorization. Organizations can lower their risk of data breaches, unauthorized access, and other security issues by implementing appropriate access controls.
Controlled Access Levels
Systems for granting access at a granular level are made flexible by Authorization. Accordingly, administrators can assign specific users’ access rights depending on their responsibilities, characteristics, or other criteria. A less privileged, more customized approach to access management is made possible by granular access control.
Monitoring and Compliance
Regarding data access and protection, several sectors have specific compliance needs. By minimizing access to sensitive data and monitoring its usage, authorization methods assist organizations in keeping to these rules.
Furthermore, audit logs provide the ability to monitor user activity, which offers valuable information for compliance reporting and security investigations.
User Characteristics
Users can access resources without needless obstacles when an authorization system is well-designed. When a pleasant and efficient user experience is provided, staff members may focus on their tasks without becoming distracted by access restrictions.
Understanding the Differences Between Authorization and Authentication
What distinguishes Authorization from authentication, then? Put, Authorization verifies which files, apps, and data a user can access, whereas authentication confirms who someone is.
The situation is comparable to that of an airline deciding who can board. Verifying a passenger’s identification to make sure they are who they claim to be is the first step. Verifying a passenger’s access to special services, such as first-class travel or VIP lounge visits, comes after their identification has been established.
Authentication and Authorization serve the same purposes in the realm of technology. Authentication aims to confirm that users are who they say they are. After this is verified, Authorization provides the user access to varying degrees of data and carries out tasks according to the guidelines defined for various user categories.
Let’s analyze the key differences between Authorization and authentication:
| Authentication | Authorization |
| Users’ identities are verified during the authentication process to allow them access to the system. | A person’s authority is verified during the authorization procedure to allow access to the resources. |
| Before the authorization procedure, it is performed. | However, the authentication procedure is completed before this one. |
| Establishes if users are who they say they are. | Decides what information users can and cannot access. |
| Invites the user to verify their credentials (by usernames and passwords security question answers, or face recognition, for example) | Determines if access is permitted by policies and guidelines |
| Use an ID token to transport data. | Use an Access Token for transmitting information. |
| The user authentication procedure will be handled using the OpenID Connect (OIDC) protocol. | The user authorization procedure is governed by the OAuth 2.0 protocol. |
| The user may see and partially change authentication. | The user cannot see or alter authorization. |
| Commonly Used Authentication Methods: Password-Related Verification Password-free Verification Multi-Factor Authentication/Two-Factor Authentication, or 2FA/MFA Single sign-on (SSO) societal verification | Common Authorization Methods: Role-Based Access Controls (RBAC) Authorization through SAML OpenID Authorization OAuth 2.0 Authorization JSON web token authorization (JWT) |
| Example: Employees may access a human resources (HR) application that contains information about their income, vacation time, and 401(k) by authenticating their identification. | Example: Depending on the permissions specified by the company, workers and HR managers can view varying amounts of data after their degree of access has been approved |
According to the discussion above, Authorization validates the user’s access and permissions, while authentication confirms the user’s identity. The user can only access the system if they can provide identification. You can only access something if you have been verified as the right person but are allowed to carry out a specific task. However, it’s common practice to combine the two security measures.
Wrap up!
It’s Important for Employing a Robust Authentication and Authorization Strategy
Authentication and Authorization are necessary for resource protection in a strong security framework. By implementing a robust authentication and authorization framework, organizations might reliably confirm each user’s identity and the extent of their authority, therefore averting potentially dangerous and illegal activities.
In an era where data breaches cost organizations money and damage their brand, organizations can improve security while optimizing efficiency by ensuring all users correctly identify themselves and have access to only the resources they require.
FAQ’s
What are Authentication and Authorization, for example?
Through authentication, the user’s identity is validated. What resources a user can access depends on their Authorization. Passwords, one-time pins, biometric data, and additional information submitted or supplied by the user are some ways that authentication functions.
What are Some Instances of Permission and Authentication in the Real World?
Establish post privacy guidelines (authorization) and use your username and password to authenticate yourself when logging onto social media accounts.
Authentication vs. Access Control?
Authorization and access control are frequently used synonymously. Even though access control includes various authorization policies, Authorization still includes access control. The authorization procedure is used by access control to allow or prohibit access to systems and data. Put differently, permission establishes rules about what a person or service can access. These regulations are enforced via access control.
The contrast between Authorization and authentication holds when comparing access control and authentication. Access control leverages the user’s identity, verified through authentication, to decide whether to give or prohibit access.
How do Permission and Authentication Enhance Security?
Although Authorization limits the actions of authorized users, it lessens the possibility of threats from unauthorized users by ensuring that only genuine users may access resources.
Are Authentication and Authorization Similar?
Like each other, Authorization and authentication are two components of the underlying process that grants access. Because they both have the same “auth” acronym, the two phrases are frequently misunderstood in the information security community.
How permission and authentication both make use of identification is another similarity between them. For instance, one utilizes the identity that has been validated to manage access, while the other uses it to verify identities before allowing access.
API Authentication and Authorization Best Practices
Best Practices to follow for Safe API Authentication and Authorization
- Utilize Gateway APIs
- Utilize Encryption
- Make use of Input Validation
- Install API Keys
- Utilise OpenID Connect
What are Authn and Authz in API?
Before allowing access to an API, a user’s identity is verified. This procedure is known as authentication. Determining which resources a user is authorized to access is the process of Authorization.
Authorization and authentication are two distinct processes. For instance, the server uses Alice’s password to authenticate her if Alice signs in with her login and password. Determining a user’s Authorization to do something is called Authorization. Alice, for instance, is allowed to use resources but not produce new ones.
Professional IT Consulting and Cyber Security Services to protect your data, website, and organization!
– Take to Our Experts
