What is Social Engineering? Techniques, Examples, Best Practices Preventions

Over the past few years, social engineering attacks have become very common. According to research, they account for 98% of cyberattacks. No doubt, the numbers are horrific, but it is a fact that there is no ‘stop sign’ for cybercrimes.
Given the prevalence of these attacks, it’s crucial for organizations to take the lead in outsmarting these fraudsters. To help you out, we explain some techniques and strategies to combat social engineering threats.
Let’s start by understanding what exactly this attack is!
What is Social Engineering?
Social engineering is a set of tactics where cybercriminals manipulate users to make security mistakes and disclose their personal, sensitive information. These tactics take advantage of the users’ inability to detect an attack, especially the elderly and untrained.
Security is all about knowing who, when, and where to trust. Understand this with the following example.
Imagine a house completely secured with locks, guards, cameras, etc. Suddenly, a person who claims to be a delivery boy comes, and without making sure you let them in.
This entails you’re essentially nullifying all those security measures. Even if you have good security, if you’re not careful, it’s like you don’t have any security at all. (The same applies to social engineering!)
How Does a Social Engineering Attack Work?
A social engineering attack works by tricking human emotions, such as fear or curiosity, into clicking on malicious links. Instead of breaking into computer systems, attackers manipulate people’s trust and emotions.
Imagine someone pretending to be from your bank and asking for the password. They might send an email that looks real, but it’s actually fake. If you believe them and give them the password, they can access your account (a/c) and steal the money.
Below is a detailed explanation of social engineering threat lifecyle.
The social engineering attack lifecycle is divided into four stages:
- Information Gathering: This is the initial stage in which the attacker gathers user information through technical sources, physical reconnaissance, or dumpster diving (collecting information through the organization’s trash).
- Hook/Engagement: Once they have the target in sight, cybercriminals move on to the engagement stage. Here, they use various tactics to trick the user and gain their trust by sending phishing emails, making deceptive phone calls, or creating fake social media profiles.
- Exploitation/Execution: With the user engaged, the hackers execute their attack. This includes tricking the victim into clicking on a malicious link, downloading malware, or revealing sensitive information like passwords or account details.
- Exit: After achieving their objectives, the cybercriminals exit the scene without leaving a trace. They do this by deleting logs, erasing evidence of their presence, or hiding their identity to avoid detection.
Pro Tip: Use a VPN as it encrypts the data by sending it through an encrypted VPN tunnel, which makes the data unreadable. Even if the hacker gets access to it, they will not be able to use it for malicious activities. In simple terms, VPN encryption is one of the most effective ways to safeguard against social engineering scams.
Types of Social Engineering Attacks
Below are some of the types of social engineering attacks that you must stay vigilant of!
Phishing
Number one, our list is the most well-known type of social engineering attack, i.e., phishing. According to a source, almost 3.4 billion phishing emails are sent every day.
In this attack, hackers send deceptive emails or messages to individuals that appear to be from legitimate sources, like banks, social media platforms, or government agencies.
The aim is to entice them to click on malicious links, download harmful attachments, or disclose sensitive or personal information, such as passwords or credit card numbers.
According to the Federal Bureau of Investigation (FBI), phishing is the top cybercrime, with incidents nearly doubling every year.
Baiting
In baiting social engineering attacks, hackers trap users by offering something “free,” which is almost every individual’s weakness. This includes free software downloads, concert tickets, or gift cards. But here’s the catch!
In return for free gifts, the hacker requests personal information, login credentials, or payment details. Also, they might leave infected USB drives in the user’s system, which gives scammers access to that particular system.
Tailgating/Piggybacking
Tailgating or piggybacking is a security breach where an attacker gains entry to a secure facility by exploiting the trust of authorized individuals. Once inside, they can execute malicious activities.
This social engineering attack also extends to scenarios where an unauthorized individual borrows an employee’s device, such as a laptop, to gain access to the organization’s network or systems. In this case, the attacker may install malware that compromises security.
Whaling
This is also a type of phishing attack, but here, the emails or messages are sent with some level of personalization.
Phishing attacks are not personalized and target millions of users, but the scenario is different with the whaling attack as it only selects high-profile individuals within an organization, such as executives, CEOs, or other senior leaders.
Though the victims are high-profile individuals with access to the company’s critical systems, sensitive data, or financial resources, the results are advanced ransomware attacks.
Diversion theft
This social engineering attack is executed offline. It involves manipulating couriers to deliver packages to the wrong place or to the wrong recipient. However, this strategy has now found its way to the Internet as well.
In diversion theft’s online version, hackers trick users by sending sensitive information to the wrong recipient. This can occur through various methods, one of which is spoofing.
What is Spoofing?
It is a technique by which hackers pretend to be a known or trusted source, including spoofed emails, IP addresses, DNS records, GPS coordinates, websites, or phone calls.
Business Email Compromise (BEC)
In business email compromise attacks, hackers pretend to be high-level executives in a company. They monitor the real executive’s actions and then create a fake email account that looks genuine.
Also Read: How to Tell If an Email Is Fake or Real?
Hackers send phishing emails to employees with that email account, asking them to transfer money to a different bank account or change financial details. Now, if the email comes from a trusted person, why would anyone doubt it?
And unfortunately, cybercriminals take advantage of this! Employees will not think twice after seeing the mail and will do as said, resulting in huge financial losses for the company.
Smishing or SMS-phishing
Smishing, short for SMS phishing, targets individuals through text messages on their mobile phones. In these attacks, the attacker calls the user and pretends to be a relative or a friend they know.
Then, they ask for money by sending a text message with a link and saying that your ’friend’ is stuck here. He/she has been robbed, beaten, and is in the hospital.
When the victim clicks on the link, it takes them to a fake website, which unfortunately results in empty bank accounts.
Smishing attacks are becoming more common because so many people use their phones all the time. Unlike email phishing, where people are more cautious, many folks don’t realize that text messages can be dangerous, too.
Pretexting
In pretexting social engineering attacks, hackers manipulate individuals by creating a convincing backstory. This could involve impersonating someone in authority, such as a bank employee, IT technician, or government official.
After the user believes their story, the scammer then asks for sensitive information, such as passwords, account numbers, or personal details, which they further use to do fraudulent transactions.
The conversation is so convincing that it’s impossible to distinguish between a hacker and a genuine personality.
Honeytrap
A honeytrap attack is when someone pretends to be someone else on dating sites or social media to trick people into giving them money or personal info.
Here’s how it works: The hacker creates a fake profile and starts building a relationship with the victim. Over time, they gain trust and take advantage of that to get money, steal personal info, or even install harmful software on the victim’s device.
Scareware
Have you ever received a pop-up in your browser saying, “Your computer may be infected with harmful virus or software”? If yes, then it may be a scareware attack.
Scareware, also known as deception software or fraudware, is a malware tactic that bombards users with false alarms and fictitious threats. It aims to deceive users into believing their system is infected with malware, leading them to install software that provides no real benefit or, worse, is malware itself.
The threat can also be distributed via spam emails containing fake warnings or offers for users to purchase worthless or harmful services.
Social Engineering Attack Real-World Cases
Below are some of the real-world examples of social engineering threats.
Deepfake Attack on UK Energy Firm
In March 2019, a UK energy firm became a victim of the social engineering attack, resulting in the loss of €220,000.
The scammers used AI voice emulation software to mimic the voice of the CEO of the UK energy firm’s parent company, who was German. Then they contacted the UK CEO and urged him to urgently transfer €220,000 to a Hungarian supplier, which turned out to be the scammers’ account.
Google Drive Scam
In the year 2020, the phishing social engineering attack exploited Google Drive’s notification system.
Scammers sent out emails and push notifications that looked like they came from Google. These messages asked Gmail users to click on a button that said “Open in Docs.” When they clicked on the button, users got directed to Google Docs, where they were asked to give access to their email account data.
Unfortunately, by giving permission, people gave scammers access to their email accounts, contacts, and online documents. The malware then automatically sent out more phishing emails to everyone in the user’s contact list.
What made this scam especially tricky was that the emails and notifications looked like they came directly from Google, making people trust them without thinking twice.
Singapore Bank Phishing Scam
Oversea-Chinese Banking Corporation (OCBC) customers were targeted by a series of phishing attacks in 2021. This resulted in significant financial losses of around $8.5 million and approximately 470 customers.
Helen Wong, the CEO of OCBC, in an interview, described this battle as like “fighting a war.”
Here’s how the threat was executed!
The phishing attacks began with customers receiving deceptive emails that asked them to disclose their account details. Despite the bank’s efforts to stop these scams by shutting down fake websites and warning customers about the scam, the situation quickly escalated.
Wong explained that after the scammers stole the money, they put it into secret “mule” accounts. Even when OCBC shut down these accounts, the scammers quickly made new ones.
This whole situation shows how hard it is for banks to stop these phishing scams!
Microsoft 365 phishing scam
In April 2021, hackers used a phishing attack to target Microsoft 365 users. Here’s how they did it.
The user receives an email that may seem innocuous, such as “price revision.” Inside the email is an attachment that appears to be an Excel spreadsheet file (.xlsx). However, the attachment is actually a disguised .html file.
As soon as the user opens the disguised .html file, they are redirected to a website containing malicious code. This code triggers a pop-up notification, falsely claiming that the user has been logged out of Microsoft 365 and asking them to re-enter their login credentials. The ones who entered the credentials, their data was sent directly to the cybercriminals.
Google and Facebook Spear Phishing Scam
Who can ever imagine that tech giants like Google and Facebook would also become a target of hackers? But yes, it was one of the biggest social engineering attacks of all time, costing $100 million.
This attack was executed by Lithuanian national Evaldas Rimasauskas. He pretends to own a fake computer manufacturer company that worked with Google and Facebook.
The attackers also opened bank accounts in the fake company’s name and sent phishing emails to Google and Facebook employees, asking them to pay for goods and services that the company provided.
But instead of depositing the money into the real company’s account, they directed the payments to their own fraudulent accounts.
Between 2013 & 2015, Rimasauskas and his crew managed to cheat Google and Facebook out of more than $100M.
Social Engineering Attack Prevention Strategies
It is a fact that social engineering security threats will never vanish, and likewise, the strategies to prevent them will persist. So, here are some of the tactics to prevent these attacks.
Check for an SSL Certificate
If your email, website, or data is protected or encrypted with SSL/TLS certificates, hackers will not be able to access the information easily.
Furthermore, when visiting any website, check if the URL begins with “https://” as it indicates that the site is secured with an SSL cert. The ones with “http://” are not secure.
If you have doubts about a website’s SSL certificate’s validity, you can manually inspect the certificate details. Here’s how!
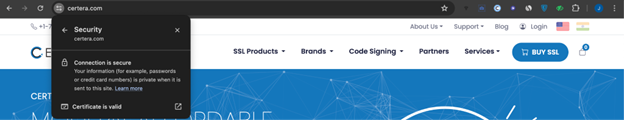
Click on the padlock icon shown on the URL, and click on “connection is secure.”
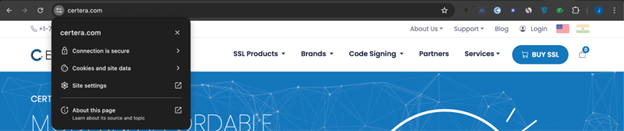
If the dialog box appears written, “certificate is valid,” then the website is secure with an SSL cert. To check its validity, click on the “arrow” sign.
Use Multi-factor Authentication (MFA)
MFA or multi-factor authentication is the most effective way to prevent a social engineering attack. Here’s the proof!
According to sources, almost 96% of bulk phishing attacks are prevented by MFA.
Gone are the days when passwords were enough to protect an account; now, MFA is required to add that extra layer of security.
This involves combining something the individual knows (such as a password) with something they already have (such as a mobile or security token) or something they are (such as biometric data like fingerprints or facial recognition).
Privacy, Privacy & Privacy
Do you know how a social engineering attack is executed successfully? By breaching the user’s privacy.
Today, everyone is majorly active on social media platforms, where they share everything about their lives.
This is what the hackers take advantage of! They execute fraudulent activities by accessing personal information about their targets, such as their interests, habits, or even sensitive data.
That’s why it’s very important for users to distinguish between what to share on social media and what not to stay safe from social engineering scams. The less personal information attackers have, the harder it is for them to trick you.
Use Strong Passwords and a Password Manager
Poor passwords are the reason for almost 81% of data breaches.
Never commit the mistake of using the same or poor password for multiple accounts, as this can make you a victim of a social engineering attack. Use the ones that are strong and unique simultaneously, such as “VuOk7L4htNnNJP4.”
Further, consider using a password manager to store and manage your passwords securely, as it’s not possible to remember such complex passwords.
Be Cautious while Building Online Relationships
Trusting unknown persons online can make you the next target of a social engineering attack in 2024.
To avoid this, follow the below strategies:
- Always stay cautious while building online relationships. Be mindful of the information you share with them. Do not disclose sensitive details like your home address, financial information, or personal identification numbers.
- Look for signs of authenticity, such as common connections.
- Be skeptical of individuals who seem overly eager or pushy.
- Never neglect your instincts and intuition. If something doesn’t feel right, it’s better to block the person immediately and protect yourself from potential harm.
Verify Email Sender’s Identity
As already explained above, phishing attacks are the most common types of security breaches, in which attackers send phishing mail to user accounts.
To combat these:
- Take a close look at the sender’s email address. Beware of suspicious and unfamiliar ones, especially if they contain misspellings or unusual characters.
- Check if the email address domain name matches the legitimate domain associated with the sender’s organization. For instance, if you get any mail from Certera’s team, the sender’s email will be [email protected], which ultimately verifies its authenticity.
- Be cautious of emails that generate a sense of urgency or pressure you to act quickly.
- Avoid clicking on clicks that seem suspicious. To check this, hover your cursor over them to preview the destination URL.
Always remember that legitimate banks and associations never ask their users for confidential information.
Update Software and Systems
Hackers always prioritize systems that use outdated software, as these systems are easier to hack and are more susceptible to malware, ransomware, and other forms of cyberattacks.
So, regularly update the software as it often includes patches that fix known security vulnerabilities. You can also opt to enable automatic updates to streamline the process.
Pro Tip: Be cautious when downloading and installing software updates, especially from third-party sources or unknown vendors. Every authentic software should have a verified publisher’s digital signature signed by a code signing certificate.
Enable Spam Filter
A spam filter helps identify and block unsolicited or malicious emails. By adjusting the email program’s spam filters to the highest setting, you can protect yourself from spam messages.
This proactive approach helps protect your inbox from clutter and minimizes the risk of falling individuals to phishing threats or other social engineering scams carried out via email.
Final Takeaways!
The social engineering attack threat is increasing continuously. But it can be overcome by
- Staying vigilant and up-to-date on the latest social engineering tactics and scams.
- Implementing security measures.
For expert assistance in safeguarding your data from social engineering attacks, get Certera’s Cyber Security Services and enjoy peace of mind!
