What is Email Spoofing? Definition, Example & Prevention

You’ve certainly been the victim of email spoofing at least once. This is because email spoofing touches everyone, whether they are high-profile companies or ordinary individuals. You will find all you need to know about email spoofing in this article, including what it is, why it occurs, and how to deal with it.
Let’s Dive in,
What is Email Spoofing?
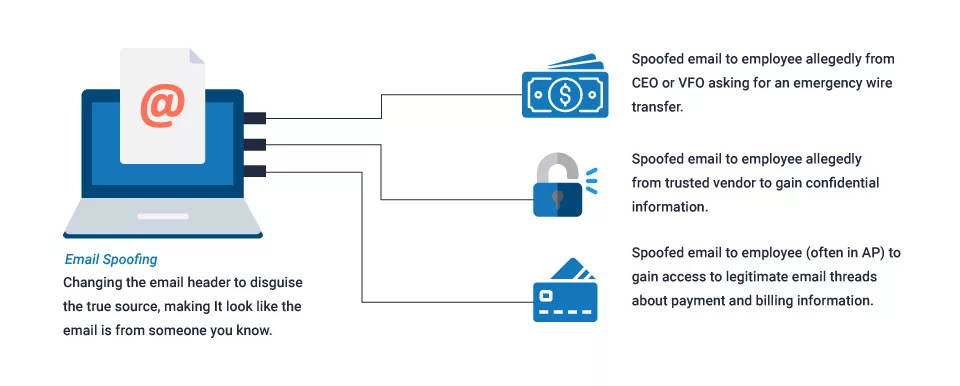
The practice of sending emails from a fraudulent sender address is called email spoofing. The email’s sender is made to appear familiar or trustworthy to deceive the receiver. Typically, it’s a phishing attack, a tool used to steal your internet accounts, deliver malware, or steal money.
Generally, in an email spoofing attack, a malicious user sends an email that has been altered to appear as though it came from a reliable source. Because customers are more likely to read an email when they believe it has been sent from a trusted sender, email spoofing is a common strategy employed in phishing and spam operations. To deceive recipients into opening or replying to the message is the primary objective of email spoofing.
Both the creation and detection of forged email messages are simple. But more malicious and specifically targeted variants can be extremely harmful and a serious security risk.
While email spoofing is a specific strategy that involves falsifying email header information, attackers can employ different techniques to accomplish the same results. Attackers could, for instance, design an email domain that closely resembles the sender’s domain to ensure receivers won’t notice the error.
As an illustration, an attacker can use the domain “@1egitimatesource.com” rather than “@legitimatesource.com.” Criminals can also change the display name to masquerade as the sender; for instance, they can send malicious emails from “[email protected]” rather than “[email protected]“.
A Brief History of Email Spoofing
Since the 1970s, email spoofing has been a concern because of how email protocols work. Spammers were the first to utilize it as a means of bypassing email filters. In the 1990s, the issue gradually developed more frequently before expanding to become a global cybersecurity challenge in the 2000s.
2014 saw the introduction of security techniques designed to fight email spoofing and phishing. Since then, many spoof emails are either rejected and never forwarded to the recipient’s inbox or sent to the user’s spam folder.
Why do People Spoof Emails?
You are probably asking why somebody would want to counterfeit the email address of a different individual or company in the first place. It’s simple: they want the receiver to think the email was sent from a reliable source.
It is frequently used for the following activities:
Phishing
Phishing attacks are the common outcomes of email spoofing attempts. A phishing email may claim to be from your bank, place of employment, or boss, or it could use other techniques to get information out of you, like posing as a government agency.
The hacker may use ransomware, steal current account confidential credentials, or gather enough data to create a fake account.
Bypassing Spam Filters
Hackers use fake emails to get around spam screening in emails. A fake email frequently resembles one you get every day and is unlikely to be detected by spam filters.
Identity Masking
A spoof email is anonymous and private. Hackers can utilize forged emails to hide their identities and earn the user’s trust by pretending to be from a legitimate company or person.
Theft of Identity
Numerous naïve people give hackers personal information and login passwords when the forged email seems trustworthy. For example, hackers can demand identification confirmation or medical information.
Business Email Compromise (BEC)
It is the term used to describe phishing attacks that use a fake, hacked, or impersonated business email account.
CEO Fraud
It is a BEC attack in which an attacker poses as a senior company executive and picks targets for an employee.
Vendor Email Compromise (VEC)
It is a BEC attack where the attacker pretends to be a vendor or another company in the target organization’s supply chain.
How Email Spoofing Works?
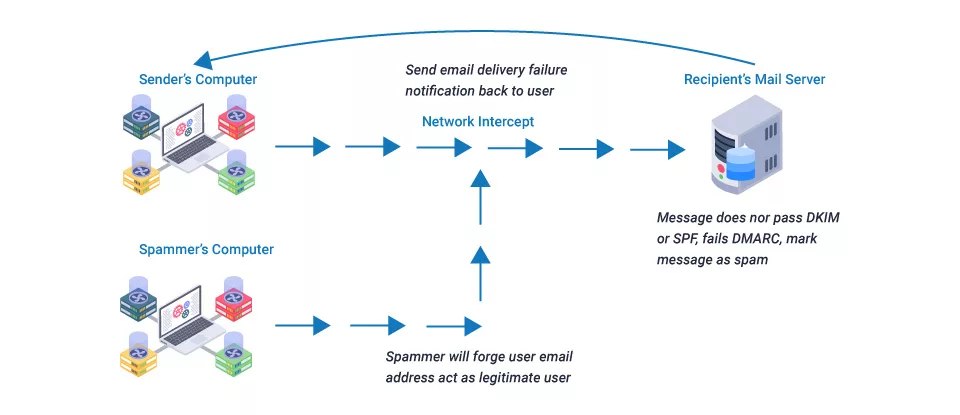
Email spoofing aims to deceive recipients into assuming the message comes from a familiar or reliable source—typically a co-worker, vendor, or company. The attacker invites the target to provide information or perform a different action while taking advantage of that trust.
A popular email client (like Microsoft Outlook) automatically inserts the sender address whenever a user sends a new email message. The sender address can be set to a specific email address, enabling an attacker to send messages programmatically using any language’s simple scripts. Even if the address does not exist, email API endpoints let a sender specify the sender address. Additionally, email servers for outgoing messages are unable to verify the validity of the sender’s address.
Utilizing the Simple Mail Transfer Protocol (SMTP), outgoing email is recovered and forwarded. The first place an email message goes when a user hits “Send” in an email client is to the outbound SMTP server set up in the client software. The SMTP server recognizes the recipient domain and directs the message to the email server for that domain. The message is forwarded to the correct user’s inbox through the recipient’s email server.
The IP address of each server visited during an email message’s “hop” as it moves from one server to another online is recorded and stored in the email’s headers. These headers reveal the truth about the route and sender. However, many users must pay more attention to the headers before communicating with an email sender.
An email consists of three main parts:
- The sender’s address.
- The recipient’s address.
- The body of the email
The Reply-To field is yet another component that is frequently utilized in phishing. This field can be modified by the sender and used in phishing attacks. The Reply-To address, which might be different from the sender’s address, instructs the client email program where to send a reply. Again, neither email servers nor the SMTP protocol verify if this email is authentic or faked. The user must recognize that the reply is being sent to an unauthorized person.
Day-to-day Email Spoofing Examples
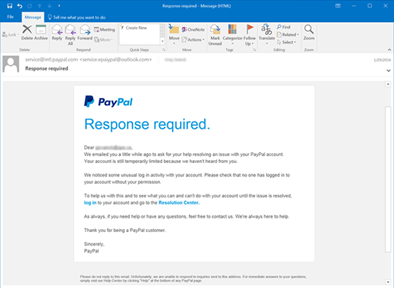
Example 1: An attacker can create an email that appears to be from PayPal as an example of email spoofing. The user is notified that their account will be suspended if they don’t click a link, log in to the website, and change the password. If the victim is successfully duped into providing their credentials, the attacker can withdraw their money into their PayPal account. Because many attackers use components from the official website to make the message appear more trustworthy, a fake email message appears authentic to the user. Here is an example of email spoofing using a PayPal phishing scam:
Example 2: A few years ago, All Seagate workers received emails from a fake CEO asking for their W-2 forms. Most workers were unaware that their yearly salaries were released since they thought the email was internal communication.
Example 3. When a worker at the multi-media messaging giant Snapchat disclosed his coworker’s payroll information, email spoofing also victimized the company. A CEO letter was delivered to an unnamed employee. The guy complied with the request since the email that was used appeared to be credible.
Statistics on Email Spoofing
If SPF and DMARC are enabled, email clients will automatically reject emails that don’t pass validation or forward them to the user’s spam folder. Attackers target individuals and companies, and even one person who is successfully deceived can steal funds, data, and credentials.
It’s understandable why email spoofing has become a popular attack vector for hackers. Consider the statistics below:
- Every day, 3.1 billion domain spoofing emails are sent.
- Email messages are the origin of more than 90% of cyberattacks.
- Since 2016, email spoofing and phishing have caused approximately $26 billion in damages worldwide.
- According to the FBI, 2019 had 467,000 successful cyberattacks, 24% of which were email-based.
- Only 9% of bait emails come from other sending domains, and 91% of them are sent through Gmail (Source: Threat Spotlight Bait Attacks on Barracuda’s Blog, 2021 November 10)
- CEO fraud, often called business email compromise (BEC), is a frequent attack that takes advantage of email spoofing. In BEC, the attacker uses email spoofing to pretend to be a company executive or owner. The attack often targets an accounting, finance, or accounts payable employee.
- On average, consumers were defrauded of $75,000 by scams.
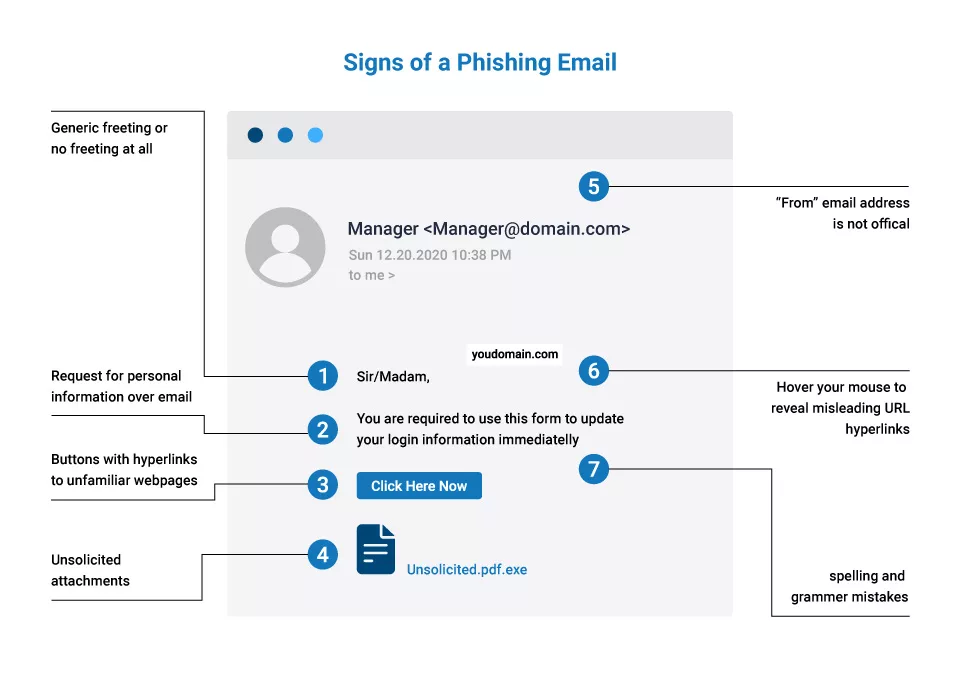
How to Recognize a Fraudulent Email?
- The email address and sender name that are displayed are different.
- The email signature contains information inconsistent with what is known about the sender, such as a phone number with a Massachusetts area code while the sender is in California. The RECEIVED line may be found in the email header. It should correspond to the email address shown in the email.
- Look for RECEIVED-SPF in the email’s header. The pass should be there. The email could have been faked if it stated Fail or Softfail.
- If the company uses DKIM and DMARC, the AUTHENTICATION-RESULTS will indicate if the email complied with its standards.
How to Protect and Secure Yourself from Email Spoofing?
Apply Email Security Protocols
Domain authentication is used in email security protocols to reduce threats and spam. SPF (Sender Policy Framework), DomainKeys Identified Mail (DKIM), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) are the effective email security protocols now in use.
SPF can only identify forged sender addresses in the email’s envelope, which is utilized when an email bounce back during the delivery phase of an email. However, when used with DMARC authentication, SPF could recognize a fake “visible sender,” a scam frequently employed in spam and phishing.
Encrypt Email
Public and private keys are used by DKIM to verify a sender’s identity. A set of keys matching to a public DNS record must be included in every SMTP message, and the recipient mail server must verify the keys.
Be Cautious of Messages calling for Urgent or Immediate Action
Any unexpected or unsolicited emails requesting personal information, money, or other urgent action should raise suspicion in the recipients. For instance, it would be suspect if an application suddenly asked you to update your login details.
Install a Security Gateway for Email
A group of approaches known as email security gateways, sometimes known as Secure Email Gateways, work on a network level to filter emails that fail to adhere to security policy standards.
All the emails (incoming and outgoing) are scanned and verified by an email security gateway, which may additionally have features for preventing viruses, spam, content filtering, and email archiving. These preventative measures do not attack users because they occur at the network level.
Apply an Anti-malware Solution
Before faked emails reach recipients’ inboxes, antivirus software can detect and prevent them efficiently. Because malicious users are aware of newly discovered vulnerabilities and rush to exploit them, it’s critical to maintain anti-malware software up to date.
Check Email Headers
Several email applications provide a method for seeing an email’s header. For instance, selecting “Show original” on a specific email will display the email header in Gmail. To find the “Received” section, find the header’s “Received” section. The email is probably forged if a domain other than the one in the “From” address appears.
Educating Users
Train your employees how to identify spoofing attacks and avoid them. Discuss how to recognize phishing emails that should be notified and reported before opening.
Wrap Up!
To sum up, email spoofing is a deceptive technique that can be employed for various malicious ends. Individuals and companies can secure as well as protect themselves from these damaging attacks by knowing how email spoofing works and taking the required security measures. Be vigilant in protecting your digital communication.
Secure your Email and Documents with Trusted S/MIME (Email Certificates) Starts at Just $12.99 Per Year!
