What is mTLS Authentication (Mutual TLS)?

What is mTLS?
mTLS, which stands for Mutual Transport Layer Security, is a security protocol that can be used between two client and server applications to enable the encryption of their communication sessions while they access each other over a network, such as the internet.
It is a further development on the foundation of the TLS (Transport Layer Security) protocol since it uses an additional layer of validation to be able to verify both the client and the server to mutual satisfaction using a digital certificate.
In mTLS, the client and the server have to provide certificates to each other instead of the server being the only entity that verifies them. The security connection is established only after both parties establish valid certificates.
Authentication implemented on both sides of the communication guarantees that both the communicating parties are trusted members of the channel, thus increasing the security level of the communication.
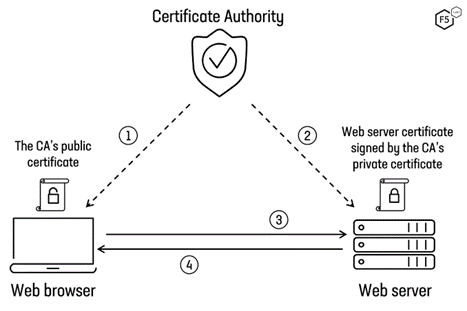
mTLS is a reliable protocol possessing a built-in mechanism that provides each connection between the client and server with proof that both the client and the server are who they claim they are.
Through implementing encryption, authentication, and integrity verification, mTLS boosts data security, prevents unpopular traffic and ensures that the right data is delivered to the intended recipient when communicating over the internet.
What are the Differences Between TLS & mTLS Authentication?
| TLS (HTTPS) | mTLS(HTTPS) | |
| Verification | Server’s identity | Both server & client’s identities |
| Client certificate | Not required | Required |
| Mutual authentication | No | Yes |
| Security | Basic | Enhanced |
| Use cases | General web communication | Secure client-server communication, such as IoT devices, VPNs, and financial transactions |
How does it Work?
mTLS is a safety mechanism that allows the identity of clients and servers to be confirmed by each other through the use of X.509 digital certificates.
Each client has a personal certificate, and a server certificate must be presented for the verification of the identity of both sides in mTLS, ensuring that the corresponding client’s and server’s certificates were not faked.
The client first transfers a request to the server, including its certificate, afterward. This confirms that the server has digitally signed the certificate, and after successful validation, the server sends its own certificate to the client for verification.
The client and the server then exchange a check certificate request for verification, and after their confirmation, a secure TLS link is created, and both parties can exchange information.
Whilst mTLS provides high-level security in areas where confidential information needs to be protected, such as when users log into an organization’s network or applications, and also for cases where the verification process for devices that are being used is not the traditional sign-in process, like in cases of IoT devices.
Is mTLS the same as 2-way SSL?
mTLS (mutual TLS) and two-way SSL are widely used for trading, meaning they assume the process of authentication in which both the client and server get through the presentation of their own certificates before they get verified.
This mutual authentication removes doubts regarding whether the parties are who they claim to be, and whilst the traditional TLS only has the server acknowledge the client, in VPN, the client also has a way of confirming the identity of the server and introduces a greater level of security.
mTLS and two-way SSL are just the same regardless of the fact that they serve as an identification authentication method that requires both four parties, the client and the server, to provide digital certification as a necessity to identify themselves.
It is widely used in cases where the safety of the data should be guaranteed, and one of the most important devices for conducting secure network transmissions is precisely this one.
How do you Use Mutual TLS?
To use mTLS, client and server side certificates based on X.509 must be implemented. The client from the server sends an order that contains a certificate for approval.
Next, the server verifies the validity of the client’s certificate, and if it is successful, then it sends its own certificate to the server for validation.
When neural Endpoints are both verified, a TLS connection is secured, and data can be exchanged between client and server.
mTLS is usually found to be used in scenarios in which accurate information is to be protected, e.g., when people log into an organization’s network or applications.
It can also be used when verifying connections with devices that do not obey the conventional login process, like in IoT contexts. In addition, it is used as a crucial checker in microservices or a zero with each other.
To set up mTLS, you need a custom domain name, at least one certificate configured using AWS Certificate Manager for your custom domain name, and an SSL trust store configured and uploaded to Amazon S3.
You can allow a custom domain name to be protected by mTLS and then provide this mTLS domain name to your clients. To make API requests via custom domain names with mTLS enabled, you must have access to certificates the API server trusts in order to show root certificate authority in API requests.
SSL vs TLS vs mTLS
| Feature | SSL | TLS | mTLS |
| Full Name | Secure Sockets Layer | Transport Layer Security | Mutual Transport Layer Security |
| Purpose | Secure communication | Secure communication | Secure communication with mutual authentication |
| Authentication | Server-side only | Server-side only | Both client and server |
| Encryption | Yes | Yes | Yes |
| Integrity | Yes | Yes | Yes |
| Handshake | SSL Handshake | TLS Handshake | TLS Handshake followed by client authentication |
| Certificate Exchange | Server presents certificate | Server presents certificate | Both client and server present certificates |
| Common Use Cases | Legacy systems, obsolete | Modern web, email, VPN | Securing microservices, IoT devices, API gateways |
| Security Level | Less secure, vulnerable to attacks | More secure, widely adopted | High security, robust against various threats |
Applications of Mutual TLS
Securing Microservices Communication
Microservice architecture is based on communication between multiple services that are made by the network, and mTLS guarantees that only these trusted services can be communicated with.
A certificate is presented to each of them in order to verify their identity. As a result, if someone tries to access unauthorizedly or hack man-in-the-middle, the attack will be defeated.
IoT Device Authentication
An area of increasing importance in the current world is the need-based provision of communication security amid the rising population of Internet of Things (IoT) devices.
SSL mTLS applies certificates for authentication of devices performed to the server to ensure that only those related with permission can access the sensitive data or perform any action.
API Gateways
API gateways stand as the intermediaries, further providing clients with a secured pathway to the backend services, which handle all sensitive data and transactions.
Implementing mTLS warrants the presentation of the certificates for clients’ verification, which, in return, allows access to the protected resources. This makes API endpoints more secure, considering that the relationship between the created user and the system is strictly defined by the system rather than the user.
Client-to-Server Authentication
Traditional TLS processes include server certificates that can be presented to clients. Authentication is achieved in these situations when the clients need to be authenticated to the server, and it proves beneficial when the clients can authenticate each other.
For instance, they can use sensitive resources or they can perform financial transactions. This has an effect of keeping up the integrity of the system and results in increased security.
Secure Remote Access
In enterprise setups, mTLS is used to control internal systems such as VPNs and corporate networks, among others.
The network clients should issue the certificate that certifies their identity and signifies that the users can access the resources only when the certificate is presented.
Such an approach ensures functionality and that the intrusion into your company’s corporate data can be properly prevented.
Cloud-Based Applications
Cloud applications are usually characterized by the necessity of secure communication between components, which can be performed through different existing and new services.
Such services need to be deployed in an intermediate and distributed environment. Using mTLS will help cloud-native applications run in highly secure environments where all the communication between various components is secured, and the data is protected from illegitimate access and breaches.
Advantages & Disadvantages of Mutual TLS
Advantages of mTLS include:
- Enhanced Security: mTLS gives extra security before the client, and the server enables TLS to handshake supplementary layers of the protocol, securing both client and server.
- Prevention of Man-in-the-Middle Attacks: mTLS is effective in thwarting man-in-the-middle attacks by ensuring that Kong Gateway and PostgreSQL server can verify communication with the actual PostgreSQL server, the Kong Gateway and PostgreSQL server itself.
Disadvantages of mTLS include:
- Complexity: mTLS is more complicated than just regular TLS; it involves the advanced configuration of the authenticated certificates
- Performance Overhead: Authentication procedures in the mTLS can cause additional load multiplied with the risk of coping with the speed and streaminess of data transfer.
- Certificate Management: Tracking digital certificates for mTLS use is a difficult task. Certificate updating frequency and integrity must be configured to avoid ridding of the secured communication channels.
Conclusion
mTLS is a strong security mechanism that will strengthen the communication passed through your organization’s network channels.
When you know what a technology is designed to do, how it helps, and potential problems it can cause, and apply best practices in your implementation and management, you can use mTLS to provide secure and reliable communication between clients and servers in applications.
Certera Security Services helps in the implementation of mTLS and other security good practices with the help of our experienced team. Also they are always ready to keep you informed and secure in the ever-developing scenario of spy techniques.
