Tokenization vs. Encryption: Know the Similarities & Differences

Data breaches are a significant threat to businesses worldwide. Cybercriminals seek to exploit vulnerabilities in data security.
In 2023, data breaches exposed more than 8 million records worldwide, potentially compromising billions of records. Companies now turn to advanced data protection methods like tokenization and encryption to safeguard their sensitive information.
Tokenization and encryption are the most popular techniques for robust protection against data breaches. Both methods aim to secure data but operate differently, each with strengths and weaknesses.
This blog delves into the similarities and differences between tokenization and encryption, exploring their effectiveness in protecting data and their respective use cases in modern data security strategies. So, continue reading and make the right choice between the two.
What is Tokenization?
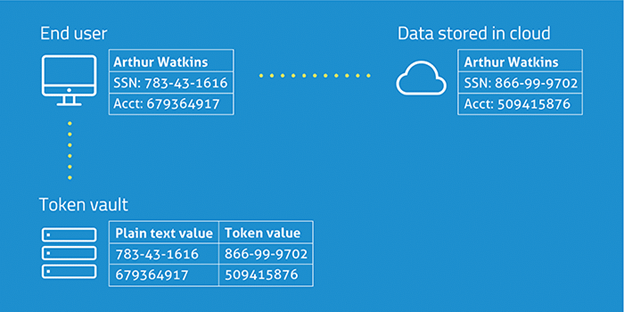
Tokenization is substituting sensitive data elements, such as a bank account number or credit card number, with a non-sensitive equivalent, referred to as a token. The token is a random data string with no specific meaning or use. Tokenized data is imponderable and irrevocable, meaning the token and its source number have a one-way relation.
One might apply no keys or mathematical operations to the token to obtain the original data. Instead, tokenization uses a reference database, a token vault that maintains the relationship between the token and the sensitive value. The confidential data in the vault is then protected, typically via encryption.
Tokenization is designed to safeguard sensitive information while preserving its utility to the business. Although tokens are contextual unorthodox words, they have many definitive features of sensitive data, such as spam or format, making it simple to incorporate into regular business operations.
Real confidential data is retained in a peripheral place, such as a network or data storage system, distinct from the enterprise’s indoor infrastructure. In machine learning, tokenization is used in feature extraction, transforming textual data into a system the model can train.
In addition to natural language processing, tokenization is introduced in data privacy and blockchain security to transform private information into token forms and reduce the risk of exposure to private data while transacting or storing it.
Pros:
- Token’s characters are random and effectively meaningless and can’t be stolen.
- The original sensitive data never has to leave the secure systems of the organization responsible for it.
- Tokenization makes PCI compliance a snap and more affordable because it reduces the amount of your technology infrastructure that has to be fully PCI DSS compliant.
Cons:
- Tokenization can be difficult to scale securely while preserving performance.
- You cannot freely exchange data; the only way to read it is by accessing the token vault.
How does Data Tokenization work?
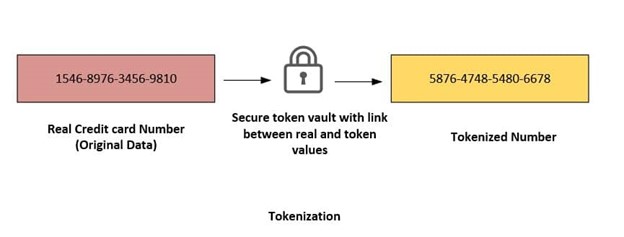
The most popular measure of protecting personal and financial information from criminals is tokenization.
Let’s consider banking, where tokenization secures cardholder data. The systems storing the token do not share the original credit card tokenization system, which replaces the token with the corresponding primary account number (PAN) and forwards the PAN to the processor for authorization.
The system cannot depart – the token is retained, and the tokenization framework determines and replaces the corresponding PAN for inquiries to the payment processors. Also, the PAN record is overlooked rather than intensified – solely the token is saved under the system.
Organizations must secure a payment gateway for tokenization to store sensitive data efficiently. Its merchant services allow direct payment through acknowledgment cards and shipping. The gateway saves credit card numbers securely and responds exactly with the random token.
What is Encryption?

Encryption transforms sensitive data into a disguised, unreadable form known as ciphertext using an algorithm. This text, in turn, can only be decoded by another algorithm, but this time, the original algorithm and the encryption key were used.
Suppose the URL has a lock icon before it. In that case, the page’s information is encrypted using Secure Sockets Layer (SSL), which encrypts data wherever it’s transmitted between a website and browser or between servers.
Recommended: Asymmetric vs. Symmetric Encryption: What are Differences?
For instance, when customers enter their card details at checkout, SSL ensures the data is scrambled during transmission. It can only be decrypted when it reaches your online store’s web server, where your payment processor uses it to finish the transaction, and they are captured for future payments.
Recommended: Hashing vs Encryption – Know the Difference
However, because it is based on an algorithm, encryption can be broken by a hacker. If a criminal managed to steal your systems and capture the encryption key, they could reverse the data to its readable format. This scenario indicates that it is pretty insecure compared to tokenized data.
Pros:
- Encryption is easy to scale as the volume of your data continues to grow.
- It is easy to share encrypted data with a 3rd party, providing they have the proper encryption key.
Cons:
- Encrypted data becomes readable by hackers if they get their hands on the encryption key.
- Although it is encrypted, the original plaintext data does have to leave the organization to complete the transaction, which makes it more vulnerable.
- You cannot reduce the scope or cost of meeting your compliance obligations because your whole technology infrastructure must be fully PCI-compliant.
How does Encryption work?
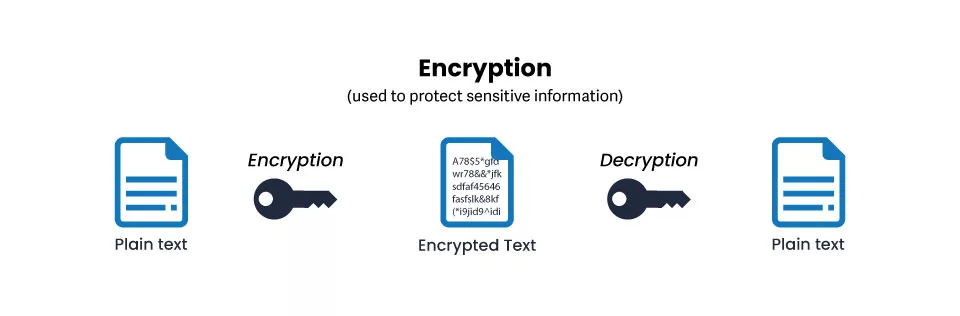
Encryption entails converting ‘plaintext’ into ‘ciphertext.’ This is accomplished through encryption algorithms and mathematical models based on cryptography. Decrypting the text back to plaintext necessitates applying a decryption key, which is a fair number of digits or a password also created to the order of an algorithm.
Recommended: What is a Cipher? Types of Ciphers in Cryptography
In practice, secure encryption has such an enormous number of cryptographic keys that an unauthorized person cannot guess which key to use. Nor can a computer easily calculate the correct string of digits by trial and error, using every potential combination.
An early example of simple cryptographic substitution is the “Caesar cipher,” named after the Roman emperor Julius Caesar, who used this encryption in his private notebooks. In the Caesar cipher, each letter in the plaintext is replaced by another letter, a fixed number of positions down the alphabet.
For example, a shift of ‘5’ to the right against the classic English alphabet would change the plaintext “E” to “T,” and, correspondingly, “Y” would be decrypted into “E.” As a result, modern cryptography uses hundreds, even thousands, of randomly computer-generated characters as decryption keys.
Comparison of Tokenization and Encryption: Features, Similarities, and Differences
| Feature | Tokenization | Encryption | Similarities |
| Definition | Process of replacing sensitive data with non-sensitive tokens. | Process of converting data into a secure format that can only be decrypted with a key. | Both techniques aim to protect sensitive data. |
| Purpose | Protect sensitive data while preserving usability. | Secure data from unauthorized access. | Both aim to enhance data security. |
| Reversibility | Usually reversible, allowing original data retrieval. | Reversible with the correct decryption key. | Both can be reversed to retrieve original data. |
| Security | Provides security through obfuscation. | Provides security through encryption algorithms. | Both provide security against unauthorized access. |
| Data Type | Typically used for payment processing and data masking. | Used for securing a wide range of sensitive information. | Both can be used for different types of data. |
| Usability | Tokens are not useful outside of the tokenization system. | Encrypted data must be decrypted for use. | Both involve a process to render data usable. |
| Performance | Generally faster than encryption due to simpler algorithms. | Encryption can be more resource-intensive, depending on the algorithm. | Both can impact performance based on implementation. |
| Compliance | Often used to comply with PCI DSS standards for payment data. | Used to comply with various data protection regulations. | Both can be used to comply with data protection standards. |
| Examples | Tokenized credit card numbers and loyalty card IDs. | Encrypted messages, files, and passwords. | Tokenized credit card numbers, and loyalty card IDs. |
What should you Choose between Tokenization and Encryption for your Business?
Tokenization versus encryption is not always an “either-or” question—most of the decisions to use tokenization or encryption inform your organizational demand.
Tokenization is an excellent solution for remaining compliant while reducing your liability and scope under the Payment Card Industry Data Security Standard.
For its part, Encryption is well-suited for scalability, as well as the encryption of large data volumes, since you only need to protect an encryption key.
By employing either tokenization or encryption for safeguarding personal information, your business can be assured of fulfilling the regulatory standards of the Payment Card Industry Data Security Standard, HIPAA-HITECH, GLBA, ITAR, and the coming European Union Data Protection Regulation.
Concluding Thoughts
Our strategy and methodology around data protection must evolve with the interaction of payment security threats. Encryption and tokenization are essential data protection tools; however, tokenization is more secure and robust due to its unique characteristics and strengths.
Additionally, the movement on the card networks’ and fintech service providers’ side — whether through innovation initiatives or momentum — shows that the tokenization concept will progressively be taken in new directions to further outfit payment flow optimization advanced, minimal-friction payment data management solutions.
Recommended: What is SSL Cipher Suite, and How it Works?
