What is SSL Cipher Suite, and How it Works?

If you have a website, you must have an SSL certificate. In general, you’re certainly aware of how SSL certificates work. It utilizes the Transport Layer Security (TLS) protocol to ensure that the communication between your website and the web browser (used by the user) is protected and secured. Furthermore, an unauthorized third party cannot exploit it, this phenomenon is known as encryption. However, many don’t know what happens behind the curtain when an SSL certificate establishes this connection.
That is why we intend to focus on cipher suites, an essential component of the encryption process. This article helps you to have a better understanding of What Are Ciphers? What Is an SSL Cipher Suite? What does the SSL cipher list comprise of? How Do SSL Cipher Suites Work? and What is the purpose and usage of cipher suites?
Let’s explore!
What is a cipher?
Before seeing a cipher suite, let us understand what a cipher is. A cipher is an algorithm or method used in cryptography to encrypt or code communication to prevent unauthorized access or theft. A cipher usually takes plaintext (the original message) as input and converts it into ciphertext (the coded message) using a specified set of rules or methods.
Ciphers can range from basic substitution methods like Caesar cipher to even more complicated computational algorithms like RSA.
What is a Cipher suite?
A cipher suite is an ensemble of cryptographic algorithms that determine the encryption, authentication, and exchange of keys to secure and protect network connections.
A cipher suite is a collection of several algorithms and protocols that encrypts, and decrypts data sent between the two parties communicating while maintaining it secure and protected from intruders.
It specifies the encryption, key exchange, and message authentication algorithms. Each cipher suite has a distinct combination of algorithms that operate together to provide a specified level of security.
RSA-AES-GCM-SHA384, AES-CBC-SHA256, and ECDHE-RSA-AES128-GCM-SHA256 are some examples of cipher suites.
Security requirements, compatibility, and performance requirements with existing systems influence the cipher suite selection.
What is an SSL Cipher Suite?
An SSL cipher, also known as an SSL cipher suite, is a collection of algorithms, steps, or instructions designed to help establish a secure connection between two parties.
In the most basic terms, the browser (client) and website (server) transmit a series of messages that authenticate the server’s public key and SSL certificate, generate a session key, and encrypt the connection between the client and the server.
Cipher Suites govern the entire procedure. The client provides the server with a list of the cipher suites it allows and supports, and the server selects the most secure, mutually supported cipher suite. Depending on the version of TLS used, this might happen before or during the handshake. SSL cipher suites decide how to establish a secure connection between entities.
This communication might occur over HTTPS, FTPS, SMTP, or another network protocol. The primary goal is to prevent hackers and man-in-the-middle (MitM) attackers from accessing your data by transforming it into unreadable cipher text.
How Does SSL Cipher Suite Work?
As stated above, the SSL Cipher Suite is a collection of encryption algorithms that protects communication between a web browser & a web server. When a browser connects to a server using HTTPS, it initiates a handshake procedure to create a secure connection. Depending on their compatibility, the browser and server negotiate the cipher suite to employ during the handshake procedure.
When a message is transmitted across a connection, the data in the message is typically encrypted using a secure SSL connection. A TLS Handshake is used to establish this connection. During the TLS Handshake, the client and server exchange available cipher suites to verify they use the same ciphers.
SSL/TLS cipher suites specify how to protect a TLS/SSL connection by indicating which ciphers the client or server uses to generate keys, authenticate users, and so on. To confirm that the ciphers used in the TLS Handshake match and that the client and server can communicate, the client and server must transmit cipher suites between each other.
The following steps may part the TLS handshake procedure:
Client Hello
The client hello phase entails the client sending a request to the server to interact. TLS version, cipher suites supported, and a string of random bytes (usually known as client random) comprise the hello message.
Server Hello
In the server hello, the server confirms the client hello and acknowledges using a TLS version that supports the client TLS type. The server likewise chooses a suitable cipher suite from the client and sends back its certificate, the TLS version, a string of random bytes, cipher suites supported, and the public key to the client (usually known as server random)
Validation of certificate
The client will verify the validity of the server-side certificate through the CA (certificate authority).
Pre-Master String
At this phase, the client encrypts/encodes a random length of bytes, termed the “Pre-Master String”, using the server’s public key and passing it back to the server; Hence, just the server can decrypt the key using its private key, providing additional security and privacy to the entire procedure.
Generating a Session Key
The server then decrypts the pre-master key, and the client and the server generate session keys using the client and server random and premaster string.
Finished Messaging
Lastly, the client and server transmit each other messages stating that they are done generating and comparing keys. The TLS Handshake is completed if the session keys match up, and the session keys are utilized for encryption and decoding any data passed between the server and client.
Since we know the functioning of TLS Handshake, we can concentrate especially on cipher suites in a TLS Handshake.
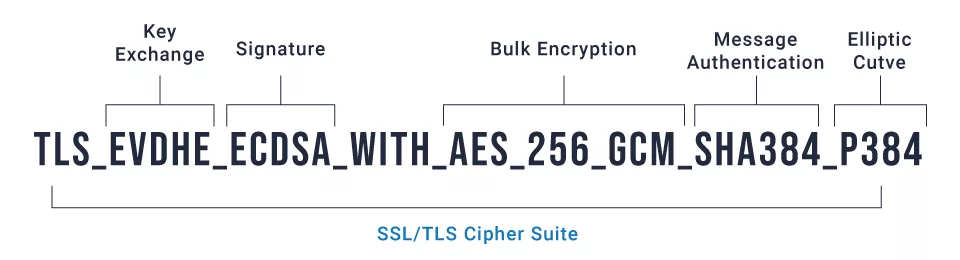
The SSL Cipher Suite comprises the following components:
- Key Exchange Algorithm
- Authentication Algorithm
- Bulk Encryption Algorithm
- Message Authentication Code (MAC) Algorithm
The Key Exchange Algorithm
Governs how symmetric keys are exchanged; Diffie-Hellman (DH), Elliptic Curve Diffie-Hellman (ECDH), or RSA are a few examples.
An Authentication Algorithm
It is a digital signature that indicates what kind of certificate and helps the customer determine the legitimacy of the website’s SSL. RSA and DSA are two different authentication techniques. e.g. HMAC (Hash-based Message Authentication Code), RSA, or DSA (Digital Signature Algorithm)
The Bulk Encryption Algorithm
Determines which symmetric key algorithm will be used to encrypt the actual data. The most prevalent bulk data encryption algorithms cipher suites use are AES, 3DES, and CAMELLA.
Message Authentication Code (MAC) Algorithm
Provides a checksum for verifying the integrity of the data. For example, HMAC or Galois/Counter Mode (GCM).
A cipher suite could look like this:
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256let’s break it down.
Here
- TLS indicates the protocol.
- key exchange algorithm: ECDHE (Elliptic Curve Diffie-Hellman Ephemeral);
- RSA is an authentication algorithm.
- Encryption algorithm: AES-128-GCM (Advanced Encryption Standard having a key length of 128 bits as well as Counter Mode for authenticated encryption)
- SHA-256 (Secure Hash Algorithm with a 256-bit output size) is Message Authentication Code (MAC) algorithm.
The design of a cipher suite varies based on the version of the TLS protocol utilized. TLS 1.2 and 1.3 are the most recent standards. While version 1.3 is the more current and secure, version 1.2 is still in use extensively.
The number of Ciphers used and the length of their cipher suites clearly distinguish these two variants. TLS 1.2 has 37 ciphers. Nevertheless, TLS 1.3 is limited to 5.
Cipher Suite Examples
- TLS_ECDSA_ECDHE_WITH_AES_256_GCM_SHA384 is a TLS 1.2 cipher suite.
- TLS_AES_256_GCM_SHA384 is a TLS 1.3 cipher suite.
As you can see, the TLS 1.3 suite is significantly shorter in length. The smaller the name and the fewer ciphers used, the quicker the TLS Handshake.
What is the significance of SSL/TSL cipher suites, and where are they used?
- Modern ciphers such as SSL/TLS cipher suites are used in SSL/TLS protocols to provide secure and confidential internet connections between clients and servers and provision of network traffic encryption.
- They guarantee the data being communicated between the client and server is encrypted, authenticated, and unaltered.
- Network protocols such as HTTPS, WebDAV, FTPS, POP3, AS2, and IMAP all implement cipher suites.
- Cipher suites are used in various applications, including web browsers, email clients, virtual private networks (VPNs), and other secure and private communication protocols.
- Advanced ciphers are used in many communication technologies, like cell phones, digital television, and ATMs, to provide security and privacy.
Wrap up!
The cipher suite provides forward confidentiality, which means that even if the server’s private key is compromised, previous conversations cannot be deciphered. It also employs a powerful encryption technique with authenticated key encryption and an advanced hash algorithm for message authentication.
While this is a brief and essential summary of cipher suites and the functions they execute, perhaps it has given you a greater understanding of the Transport Layer Security protocol & the website’s encryption procedure. To guarantee that your website employs the latest recent cipher suites, ensure your server supports TLS 1.3 and that the settings are set to the specific ones.
FAQ’s
1. What is Cipher Suite in Cryptography?
A cipher suite is essentially a comprehensive set of methods (also known as called algorithms) required to protect a network connection using SSL (protect Sockets Layer) / TLS (Transport Layer Security). Each set’s name is a representation of the individual algorithms that comprise it.
2. How to find a cipher suite in SSL?
Using Chrome, find the cipher.
- Open Chrome.
- In the browser, type the URL you want to verify.
- In the browser, click the ellipsis in the upper-right corner.
- More tools > Developer tools > Security
- Find the line “Connection.”; this will describe the TLS or SSL version.
3. What are TLS 1.2 cipher suites?
A cipher suite is a collection of cryptographic algorithms that encrypt messages between clients/servers and other servers. Dataverse employs the most recent TLS 1.2 cipher suites certified by the Microsoft Crypto Board.
4. What is the distinction between the TLS 1.2 and TLS 1.3 cipher suites?
TLS 1.3 improves previous versions in various ways, notably a faster TLS handshake, and easier, more secure cipher suites. Key exchanges with zero round-trip time (0-RTT) greatly simplify the TLS handshake.
5. How do I enable TLS 1.2 cipher suites?
To enable TLS 1.2 strong cipher suites, run a script.
- Log in to the manager.
- At the top, select Administration.
- Select Scheduled Tasks on the left.
- Select New in the main pane.
- The New Scheduled Task Wizard is shown.
- Select Run Script from the Type drop-down menu.
- Choose Run Script. Only select once. Next, click.
- Accept the defaults for the date, time, and time zone, then click Next.
- Select EnableStrongCiphers.script for the Script. Next, click.
- Enter a name for the script in the Name field, such as Enable Strong Cipher Suites. Check that Task Enabled is selected. On the ‘Finish’ tab, click Run Task. Finally, click Finish.
The script is executed.
- Start the Deep Security Manager service once more.
Your agents, relays, and managers should now only communicate with one another using TLS 1.2 strong cipher suites.
6. How Block Cipher and Stream Ciphers are different?
- Technically Block Cipher divides the data into blocks & encrypts each block individually, whereas Stream Cipher encrypts data bit by bit or byte by byte.
- Block Ciphers are way slower than Stream Ciphers when it comes to encrypting large amounts of data.
- Even reverse encryption or decryption is more difficult in block cipher than in stream cipher because more bits are combined to be encrypted in this situation.
Read our guide to learn more about the difference between block cipher vs stream cipher.
