WormGPT & FraudGPT – The Dark Side of Generative AI
Do you use ChatGPT? Who doesn’t? In fact, it gained 1 million users within just five days of its launch.
But with new innovations constantly happening, cyberspace has become much more vulnerable to newer security threats, like “FraudGPT” and “WormGPT.”
The worst part is that companies and individuals are not aware of the trouble these both can create. So, in this blog, we are going to explain everything about the new faces of cybercrime.
Let’s get started!
First, we want to correct a misconception.
Many people also get confused about whether WormGPT and FraudGPT are the same as ChatGPT. But that’s not true!
ChatGPT is developed by Open AI, a legitimate organization, but WormGPT and FraudGPT are not its creations. Cybercriminals have developed their own advanced AI chatbots for malicious activities. Read on to find out more!
What is WormGPT?
On July 13, cybersecurity company SlashNext revealed the discovery of WormGPT, a blackhat “alternative” to ChatGPT,” that lets users do “all sorts of illegal stuff.”
WormGPT is a type of malware that utilizes advanced artificial intelligence (AI), particularly natural language processing (NLP) that ChatGPT uses.
It is based on a 2021 GPT-J language model that is open-source and capable of generating human-like text. This capability allows WormGPT to write phishing emails, social media DMs, or other forms of communication that trick entities into clicking on malicious links or downloading infected files.
What is FraudGPT?
It is a product sold on the dark web and Telegram that works the same as ChatGPT but is not used for ethical purposes. FraudGPT creates content to facilitate cyberattacks, and its subscription fee starts at $200 per month and goes up to $1,700 per year.
Here’s how it works!
Its interface looks exactly like ChatGPT, with the user’s previous requests in the left sidebar and the left portion window taking up most of the screen. All that is required is to write the query and press ENTER.
During testing conducted by the Netenrich team, FraudGPT showed its ability to generate deceptive emails resembling those from legitimate banks. (as shown below)
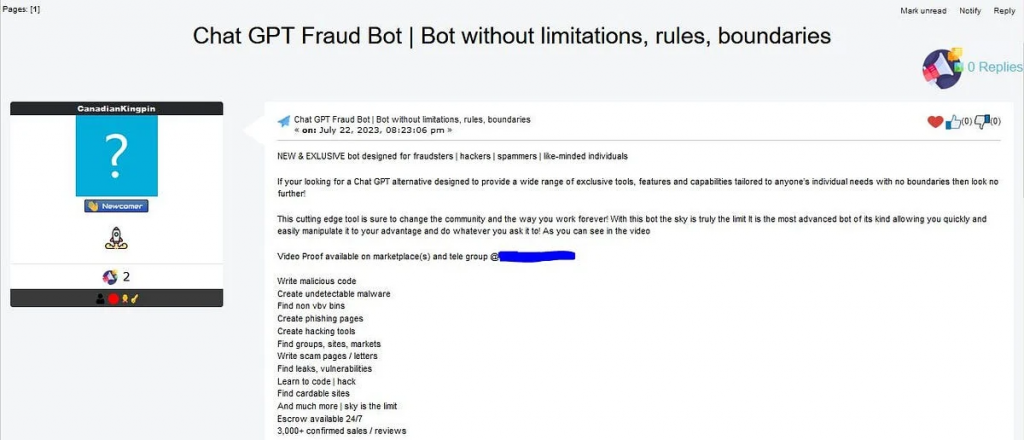
Hackers simply provide the bank’s name, and FraudGPT crafts convincing messages and even advises where to add malicious links for maximum impact. Moreover, FraudGPT can create fraudulent web pages, encouraging users to provide their sensitive information.
Beyond email scams, FraudGPT provides insights into commonly targeted websites and services. This helps cybercriminals to plan their next moves.
Researchers from the SlashNext team said that FraudGPT is trained on extensive datasets of malware, which makes it capable of producing convincing phishing and business email compromise messages.
How Are Cybercriminals Using WormGPT & FraudGPT?
Creation of Malicious Content
Both WormGPT and FraudGPT have the capability to generate malicious content, including phishing emails, scam landing pages, and malicious code. As these tools automate the creation process, cybercriminals can scale their operations and deploy a wide range of fraudulent activities with minimal effort.
Financial Fraud and Identity Theft
FraudGPT specializes in financial fraud and identity theft. Here’s how!
It uses advanced AI algorithms to do sophisticated scams, creating realistic fake identities and manipulating financial transactions. Through voice synthesis technology, it can also impersonate individuals, which is not easy to differentiate.
Detection Avoidance
WormGPT and FraudGPT can adjust their strategies in real-time, which helps them bypass security measures. They can avoid traditional security protocols and remain undetected for extended periods, which significantly increases the success rate of their attacks.
Identification of Vulnerabilities and Targets
WormGPT can autonomously identify vulnerabilities within networks and exploit them to spread further. Even cyber criminals with limited skills can use these tools, which makes them accessible to a broader spectrum of hackers.
Phishing
WormGPT uses NLP (Natural Language Processing) to mimic human communication. This encourages users to click on malicious links or download infected files.
Also Read: Phishing Attacks: How to Spot and Prevent Online Scams?
How Hackers are Exploiting The Dark Side of AI?
Hackers always find ways to stay one step ahead of security systems. Here’s how they are exploiting the dark side of AI.
Data Manipulation
AI can create convincing deepfake videos and manipulate media to spread misinformation or blackmail individuals. These techniques are so sophisticated that it is not possible for a human to distinguish between genuine and falsified content. Imagine a deep fake video of a company’s CEO requesting personal information from its users.
Credential Stuffing Attacks
Automated scripts or AI-powered tools are used to test large volumes of stolen usernames and passwords (p/w) across multiple websites or online services. By using AI algorithms, cybercriminals can rapidly cycle through millions of credentials and identify valid combinations that grant access to user accounts.
Supply Chain Attacks
In supply chain attacks, hackers target a company through its network of suppliers or partners. How?
They use advanced techniques to find weaknesses in their security defenses. Once done, they sneak malicious software or code into products or updates. This disrupts production or creates counterfeit products that could damage the company’s reputation or operations.
For instance, AI-powered chatbots integrated into a compromised website allow hackers to steal user credentials.
Advanced Malware Creation
AI algorithms are capable of evading detection. This is because traditional security measures are not that successful in detecting sophisticated malware. Hackers analyze patterns in malware code and security protocol to create variants that can easily bypass antivirus software and intrusion detection systems.
Automated Attacks
From identifying vulnerabilities to launching attacks, AI algorithms automate various stages of the cyber attack process. This automation helps them scale their operations and target a larger number of systems with minimal manual intervention, such as distributed denial of service (DDoS) attacks.
Also Read: Largest DDoS Attacks Reported till Today
In DDoS, hackers flood the targeted system or network with an overwhelming amount of traffic, data, or requests. This results in targeted systems or networks becoming unavailable to legitimate users, leading to downtime and loss of productivity.
How to Safeguard Against AI-Powered Cybercrime?
Artificial Intelligence is itself a solution for AI-powered cybercrime. Use the following strategies to safeguard your systems against hackers.
Threat Monitoring & Detection
Business processes are becoming more complex day by day, so it’s essential to maintain strong cybersecurity defenses.
AI-based solutions offer a proactive approach by autonomously monitoring and detecting threats in computer systems. These can analyze:
- Traffic patterns,
- Device parameters,
- User activities and
- Event logs in real-time to identify potential threats before they escalate.
One of the key usefulness of AI-driven cybersecurity is its ability to operate continuously without human intervention 24/7, even during non-business hours. Also, it can automate common routine tasks such as system diagnostics, updates, and fixes, thereby enhancing operational efficiency.
Vulnerability Management
Improving sustainability through better vulnerability management used to be a time-consuming task. Cybersecurity experts had to spend a lot of time gathering and analyzing data manually. But now, with the help of Artificial Intelligence and machine learning, things have become much easier.
AI-supported vulnerability scanning and management tools can automatically check important data sources like network records, system logs, and reports on threats or bugs. This means weaknesses can be found and fixed in the systems before hackers take advantage.
In a nutshell, companies can protect their data better and keep their operations running smoothly by staying ahead of potential threats.
Behavioral Analytics
Behavioral analysis proves helpful in monitoring suspicious activities online. Using cognitive computing, large volumes of data can be analyzed to detect unusual user behaviors and identify potentially harmful connection patterns.
When suspicious activity is detected, AI can either block it outright or alert security teams for further investigation and action.
AI’s machine learning capabilities allow it to adapt to different user behavior patterns over time. It can recognize anomalies or potential threats by continuously learning from data and automatically flagging them.
Keep Software Updated
When software developers release updates, they often include fixes for known security issues and weaknesses. So, ensure that the hardware, software, and apps are updated properly to keep the devices safe because systems with outdated software are easier for hackers to exploit.
Updating software is also very straightforward. Most software applications have built-in mechanisms that enable automatic updates. Alternatively, updates can be checked manually and installed as needed.
Predictive Security
According to historical data and current cyber event analysis, AI can predict future attack trends to prevent cyber threats before they occur. It can detect suspicious behavior, unusual network activity, or signs of a cyber attack.
Also Read: What is AI in Cybersecurity? Future, Benefits, Challenges
Then, provide early warnings of potential threats, which allow organizations to take preventive action before serious damage occurs.
Pro Tip: Think twice before clicking on a link! If you don’t recognize the sender, avoid clicking; instead, block the number and report it as spam.
The Bottom Line
It is a fact that hackers will never stop hacking and find new tactics as soon as new innovations emerge, as this is the only thing they can do. So, we will also do what we are best at, i.e., protecting the systems.
To streamline the process, get Cybersecurity Services from Certera and protect your business from cyber-attacks and malicious activities.
