SHA1 vs SHA2 vs SHA256 vs SHA512 Hash Algorithms – Know the Difference
Hackers do not take a break. As a result, it’s essential that you fully understand every cybersecurity term.
During your cybersecurity journey, you could have encountered the term “Secure Hashing Algorithm.“
The Secure Hash Algorithm, sometimes called SHA1, SHA2, SHA256, and SHA512, is among the most common topics. There needs to be more clarity about what they’re used for, what hashing is, and how it all relates to PKI and TLS, even though it’s evident that the various numbers at the end have meaning.
Let’s begin with some fundamental ideas regarding hashing and how it works with other TLS characteristics.
However, to create the groundwork for our primary star, you should review a few words first briefly.
Here is a list of issues that our comprehensive article will cover to ensure that you are in the correct area for the right type of hash.
Why is hashing required right now?
Theft of data has escalated over time, leading to enormous economic losses. Research claims that by 2021, losses from cybercrime will total $6 trillion. By enabling you to hash data files without exposing yourself, hashing algorithms can assist you in avoiding such scenarios.
Given that hash values are utilized in SSL certificates and digital signatures, you could not be utilizing them directly. As a result, we will discuss about hash values, hashing algorithms, and other variations like SHA-1 and others.
What exactly is Hashing?
The cryptographic procedure known as “hashing” is used to assess the authenticity of multiple inputs. It is also used to verify the accuracy of your documents and other types of data that travel around the internet.
In simple terms, Hashing is a mathematical procedure used to assess the reliability of the data source you receive. Additionally, they are used in SSL certificates, coding languages, passwords, etc.
The improper usage of hashing functions can result in devastating data breaches. However, the harm might be worse if they aren’t used at all.
‘Hashes’ are used in the hashing process to check the reliability of the data you received. Let’s take a closer look at these “Hashes” now.
Hash’s applications include:
- Databases use hash for indexing.
- In disk-based data structures, the hash is employed.
- JavaScript hash implements objects in various computer languages, such as Python.
- Systems for caching often use hash tables.
Caches:
Caches use hashes to quickly seek up frequently accessed material. Data that has been recently accessed could be stored in a cache using a hash, with the data itself serving as the key and the time it was accessed or other information as the value.
Cryptography:
In cryptography, hashes generate digital signatures, check data accuracy, and store passwords. Hash functions help confirm the legitimacy of data since they are made so that it is challenging to reconstruct the original data from the hash.
Distributed Systems:
Hashes divide work across many servers or nodes in distributed systems. For instance, a load balancer could employ a hash to assign incoming requests to various servers by the request URL or other factors.
File Systems:
In file systems, hashes are used to identify files or data blocks quickly. A hash, for instance, can be used by a file system to record the locations of files on a disc, with the file names serving as the keys and the disc locations serving as the values.
Symbol Tables:
In symbol tables, key-value pairs that represent identifiers and the properties that go with them are stored in hashes. For instance, a compiler may utilize a hash to record the names and types of variables.
What is a Hash?
A mathematical technique (Hash Function) that transforms simple data input into a format that is unreadable and produces a hash. Any text, image, audio file, or video turned into a string of characters can be considered “Simple” data. This collection of letters and numbers, or “Hash Values,” also appears weird to human sight. You’ll understand why.
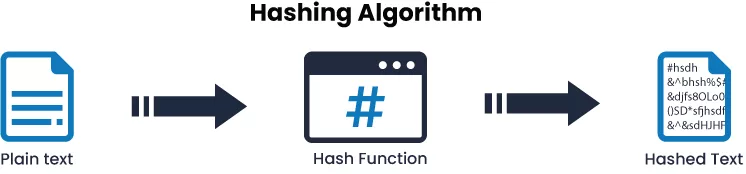
In its most basic form, a hash function accepts a string of inputs of any conceivable length and transforms it into distinct, unreadable data of a fixed size.
This scenario means that any length of incoming data will be transformed into a fixed-size hash. However, the resulting hash will be entirely different if you slightly alter the input numbers.
What is a Secure Hashing Algorithm (SHA)?
The NIST (National Institute of Standards and Technology) released a set of cryptographic hash functions known as the Secure Hash Algorithms (SHA) as a Federal Information Processing Standard (FIPS) for the United States.
Data, certificate files, and other cryptographic reasons, such as in cryptocurrencies like bitcoin, are hashed using SHA encryptions, which are employed in several ways. These hashing approaches secure the core of contemporary internet infrastructure.
Message Digest-5 (MD5) has been changed and is now known as Secure Hashing Algorithm (SHA). It allows for the secure hashing of data and files. SHA is also used to hash data in digital signatures and SSL certificates. However, it compresses the input data into a more minor form that is challenging to comprehend and hard to alter using modulations, functions, or bitwise operations.
The capability of SHA to protect data that is only accessible to hackers by brute force makes it a trustworthy security choice. This is so that, unlike encryption, SHA hashing prevents the information from being decoded.
The message or data must be changed once to produce a new hash value. As a result, two distinct hash results will be if two data types identical to one another are hashed with a small change, such as a capital letter.
Many SHA algorithms exist, including SHA-1, SHA-2, SHA-384, and SHA-512. Let’s first talk about how SHA is used before moving on to other SHA types
Utilization of Hashing in SSL/TLS
You can now comprehend how hash algorithms are utilized in the SSL certificate system since you know what they are. So, what precisely is SSL? Transmitting data over HTTP becomes HTTPS due to the secure socket layer (SSL) encrypting the initial data. It works by encrypting and decrypting the data to secure information transfer.
Only the communicating parties can access the key for converting the data into user-intelligible form. SSL certificates provide confidence and authentication. It operates with two asymmetric keys. Public critical infrastructure (PKI) is producing a single public key for secure encryption and another private key for decryption. Web browsers can access the public key, but the private key is securely saved on the server.
When compared to symmetric encryption, this asymmetric encryption demands considerably more computing. Asymmetric encryption is utilized to exchange keys between the server and the end user securely. Symmetric keys are used to transmit data between the two conversing parties. This is a more feasible strategy for the sharing of lots of data.
As a result, the client creates a session key after checking the certificate. The server receives this session key once it has been encoded. This key is decrypted for future communication at the server’s end.
Trusted and Reputed SSL/TLS Certificate starts at Just $3.99/Year
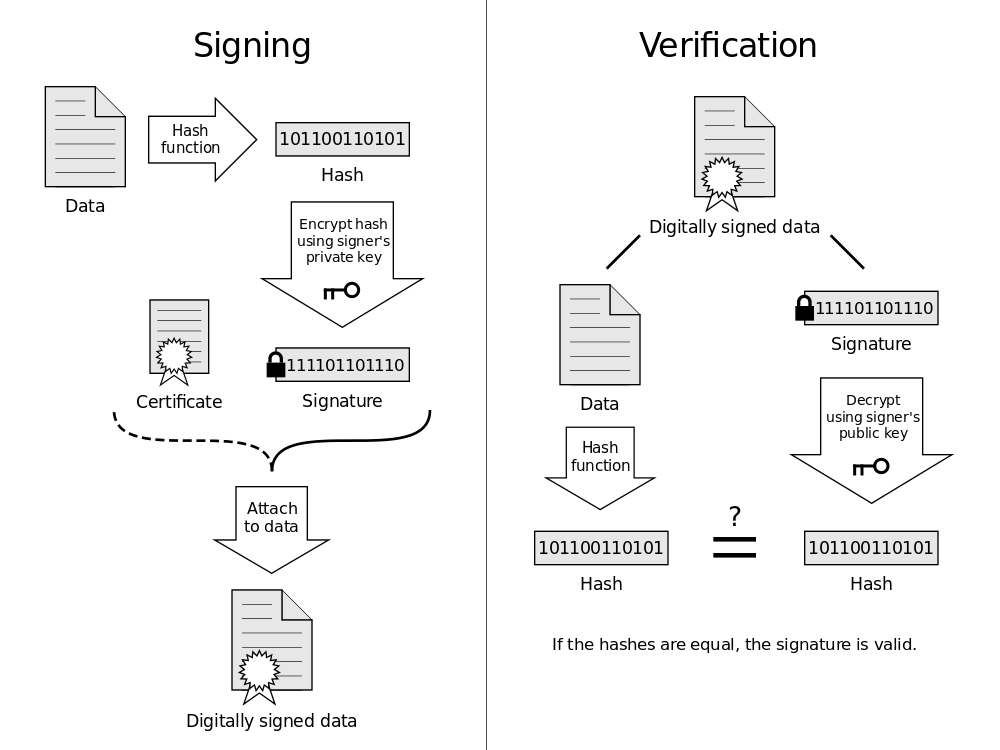
Let’s talk about digital signatures now. They play a crucial role in delivering SSL-based authentication. The Certificate Authorities (CA), a group of trustworthy and reputable parties, are the ones that issue SSL certificates. The CA offers the signature that attests to the validity of the SSL certificate. This digital signature offers cryptographical evidence that the certificate has not been changed, demonstrating that it is secure for future communications.
Here, the digital certificate is signed using a pair of asymmetric keys. Hashing is utilized to securely establish and verify these signatures while also greatly simplifying the computations for the computer. The certificate’s document is hashed by the certificate authorities, who also sign the hash key. Compared to signing the entire certificate, this is more effective.
These signatures show beyond a reasonable doubt that the certificate has not been tampered with. Due to the extraordinary sensitivity of digital signatures, the hash key will remain completely unchanged even if a single part of the document has been altered.
As a result, it is difficult for a cybercriminal to tamper with an authentic certificate or generate a fake certificate that looks authentic. An error message is shown, and communication with the party is prevented when your operating system comes across an incorrect signature. The hash technique guarantees that the data a user enters does not get into unauthorized hands.
The Difference Between SHA-1, SHA-2, SHA-256 and SHA-512
The SHA function families you will see most frequently are:
What is SHA-1?
Secure Hashing Algorithm-1, usually SHA-1, is a mathematical cryptographic hash algorithm. This algorithm is a Federal Information Processing Standard created by the US National Security Agency in the early 1990s. A “message direct” is a 160-bit (20-byte) hash key SHA-1 generated from an input. This is often represented as a hexadecimal number of 40 digits.
This encryption technique is commonly used in SSL, TLS, S/MIME, and other security protocols and applications. This secure hashing method is mandated in United States government protocols and applications for protecting sensitive data.
Additionally, it is utilized by software programs like Monotone and Git to guarantee that the data has not been altered. They mostly employ it to detect data corruption rather than for security. Since it was created, Certificate Authorities (CAs) have started to favor this method.
The SHA-1 algorithm experienced a collision attack in February 2017. Google and CWI Amsterdam created two distinct PDFs that the SHA-1 algorithm used to obtain the identical hash key. However, HMAC (hash-based message authentication code) was still discovered to be highly safe.
What is SHA-2?
Secure Hash Algorithm 2 or SHA-2. This was initially released in 2001. The National Security Agency (NSA) developed SHA-2. The family of cryptographic hash algorithms is called SHA-2. There are six distinct functions in SHA-2. This was created as SHA-1’s successor. Some initiatives, including TLS, SSL, PGP, SSH, and others, use SHA-2. Compared to SHA-1, this offers more safety and security.
In security protocols and applications like SSL, TLS, S/MIME, and many more, the SHA2 hash is frequently used for encryption decryption. Along with the SHA-1 hash, this secure hashing method is also used to secure sensitive data, particularly United States federal law enforcement data-sharing protocols. In SSL certification, end users prefer to utilize this hashing.
SHA-224, SHA-256, SHA-384, SHA-512/224, SHA-512, and SHA-512/256 are the six modified hash functions that make up this method, typically a family of algorithms. Two of them—SHA-256 and SHA-512—are regarded as innovative hashing algorithms.
What is SHA-256?
Secure Hashing Algorithm – 256, often known as SHA256, belongs to the family of SHA-2 computations, which was previously discussed. Additionally, it uses a sequence of mathematical operations on digital data to perform a cryptographic hash function.
This hashing algorithm overtook SHA-1 as the most used replacement. The data is divided into chunks of 512 bits, or 64 bytes, for this method to function. As the name indicates, it creates the encryption and produces a 256-bit hash key.
This scenario is the most extensively used protocol after the secure hashing algorithm one collision. It is frequently suggested for usage with several cryptocurrencies, with Bitcoin being the most prevalent.
This hash computes the proof of work and stake in cryptocurrencies and validates transactions. It also offers the appropriate amount of password hashing in addition to the computation and verification. Given this, suppliers for Linux and Unix are starting to employ this hashing technique for password protection. It has been stated that DNSSEC (Domain Name System Security Extensions) makes use of it.
What is SHA-512?
SHA-512 is a Cryptographic Hash Algorithm. A text or data file “signature” can be represented by a cryptographic hash, sometimes called a “digest.” SHA-512 creates a 512-bit (32-byte) signature for an almost unique text. SHA-512 produces 512-bit hash values.
In simple terms, this hashing process turns any text length into a fixed-size string. A SHA-512 length of 512 bits (64 bytes) is generated for each output. Though it is a little slower, the bigger hash size it gives makes it less vulnerable to attacks.
This method is frequently used for hashing passwords and email addresses and verifying digital records. Blockchain technology also employs SHA-512, with the BitShares network as the most notable example.
The adoption of the SHA-512 algorithm by blockchain projects has been significantly slower than that of the SHA-256 algorithm. Scrypt, Lyra2REv2, Equihash, and CryptoNight are some of the most popular hashing algorithms used by blockchain networks instead of SHA-256.
What Distinguishes SHA-1, SHA-2, SHA-256, and SHA-512?
As previously stated, “SHA” stands for the Secure Hash Algorithm. However, SHA-2 is only the upgraded version of the Secure Hash Algorithms, not an independent technique.
The hash length is where SHA-1 and SHA-2 significantly diverge from one other. Here, SHA-1 is a simple hashing method that is like MD5. Here, SHA-1 is a simple hashing algorithm that is like MD5 in nature. As a result, SHA-1 has a shorter code than SHA-2 or SHA-256, which reduces the chance of unique combinations.
Additionally, the US government-developed SHA-1 provides 20 bytes (160 bits) of hash values, represented by a 40-digit hexadecimal text value. On the other hand, SHA-2, a family of algorithms that includes six alternative hash functions that yield hash/digest values of differing lengths, such as 224, 256, 384, or 512, was also created by the US government, particularly the NSA.
In simple terms, SHA-2 refers to a distinct family of hashing operations that also includes SHA-256. Finally, due to SHA-1’s security flaws, it was phased out in 2015, and starting in 2016, it became mandatory to use SHA-2 for all newly issued SSL/TLS certificates.
Conclusion
By reading this article, learn about the differences between SHA-1 and SHA-256 and how the hashing method affects SSL/TLS certificates. Knowing the three most popular secure hashing algorithms will enable you to compare them and choose the most effective and suitable one.
Moreover, SHA-1 is an outdated, less secure variant, whereas SHA-256 is commonly utilized today. Furthermore, SHA-256 is a member of the SHA-2 family of cryptographic hash functions, which is the most used in today’s world and is used in SSL/TLS certificates and blockchain.
