What is Certificate Lifecycle Management (CLM) in Cybersecurity? [Detailed Guide]

Digital certificate management is vital to maintaining a secure and trusted cybersecurity environment. Every single legitimate website that uses a certificate must understand the importance of CLM or Certificate Lifecycle Management.
Here, we’ll delve into what CLM means, why it’s important, and how organizations can effectively implement it.
What is Certificate Management?
Certificate management is the procedure of monitoring, processing, and executing every certificate process for uninterrupted network operations.
In simple terms, we can say that certificate management holds the responsibility of purchasing, deploying, renewing, and replacing certificates on their respective endpoint, like applications, servers, devices, or any other network component.
This allows the respective organization to monitor and manage the life cycle of all certificates deployed in a network.
What is a Digital Certificate?
Digital or X.509 certificates include all the information required to authenticate the identity of different entities, such as individuals, websites, organizations, and more.
Basically, digital certs are the same as SSL/TLS certificates.
They use a unique private/public key to ensure the security of information exchanged over the Internet. Overall, this certificate identifies and validates digital communications and communicators.
Now, a misconception is very popular that the process of employing digital certification is very complex. But this is not true! In fact, it’s very sorted!
All you need to do is purchase it from a CA or certificate authority like Certera and install it on the endpoint, like a device, server, or website. Make sure to renew the cert once it expires, so keep an eye on that as well.
What is Certificate Lifecycle Management?
Certificates are first issued, then used, and finally expire, so they have a well-defined lifecycle. The process of managing all of these is known as CLM or Certificate Lifecycle Management.
Before we explain further, let’s first understand why you need a certificate lifecycle management system.
With the emergence of digital transformation, nearly every enterprise process is moving to the cloud. This has led to a surge in connected devices, from cloud applications to IoT devices. Managing all of these can be a typical task, as there are hundreds or even thousands of certificates, each with its own unique properties.
Manual methods like using spreadsheets become impractical due to the volume and complexity. Here comes the role of a certificate management system for managing all these with ease.
It consists of five steps, as explained below.
Certificate Request & Enrolment
This marks the first stage of CLM, i.e., certificate request and enrolment phase. Here, a user or device requests a cert from CA by providing the below information,
- Organization details
- Domain owner details
- Identities of the individuals requesting the certificate
- Contact details
- The intended reason for requesting the cert
- Company identity.
Disclaimer: CA can also ask for additional information based on the requested certificate type.
After submitting the above information, the following details must also be provided for digital signature creation.
- Public key for the CA’s signature
- Hashing algorithm and
- Digital signature
Issuance and Provisioning
The public key, along with the private key, is created by Cryptographic Service Provider (CSP) and forwarded to the CA.
After the CA receives the request, it decrypts the digital signature using the public key, calculates a hash, and verifies the same. All the above information will also be verified according to proper rules and regulations for validation.
If the Validation procedure is successful, the digitally signed public key will be sent to the user. Now comes their role of storing it on the server and taking note of its destination.
Certificate Usage
Now, the user uses the certificate to interact with devices, browsers, and websites. Then, the monitoring system generates usage data and provides alerts regarding certificate expiry.
Certificate Monitoring & Reporting
Monitoring & reporting plays a very important role in the whole Certificate Lifecycle Management. It helps administrators with several queries, like:
- How many certificates have been issued?
- Which ones are required to be renewed or replaced?
- Any potential problems that need to be addressed.
Overall, this stage proactively avoids outages in the whole process.
Certificate Expiration & Renewal
After the certificate expiry date comes near or if it expires, the CA or certificate holder initiates the renewal process. This process can be automated as well. Remember, it should be done in a timely to avoid potential connectivity problems.
The holder gets a new certificate after the cert renewal. Similar to the original one, it comes with a digital stamp from the CA to verify its legitimacy.
Retirement or Revoked
This step is completely subjective and depends on the particular situation, like
- If the certificate authority (CA) had improperly issued a certificate
- If a private key is compromised
- If the identified entity does not adhere to the rules
- User no longer being in sole possession of the private key
- Violation of any other policy
Certificate Management and PKI Architecture
As explained above, certificate management involves analyzing and monitoring all digital certificates deployed by the Certificate Authority.
This concept relates to PKI to a great extent. Read on to find out how!
What is PKI or Public Key Infrastructure?
Public key infrastructure (PKI) is an underlying framework that establishes secure internet connections through public key encryption. In layman’s terms, PKI refers to any software, policy, or procedure that helps configure and manage certificates and keys.
How does PKI Make Online Interactions Secure?
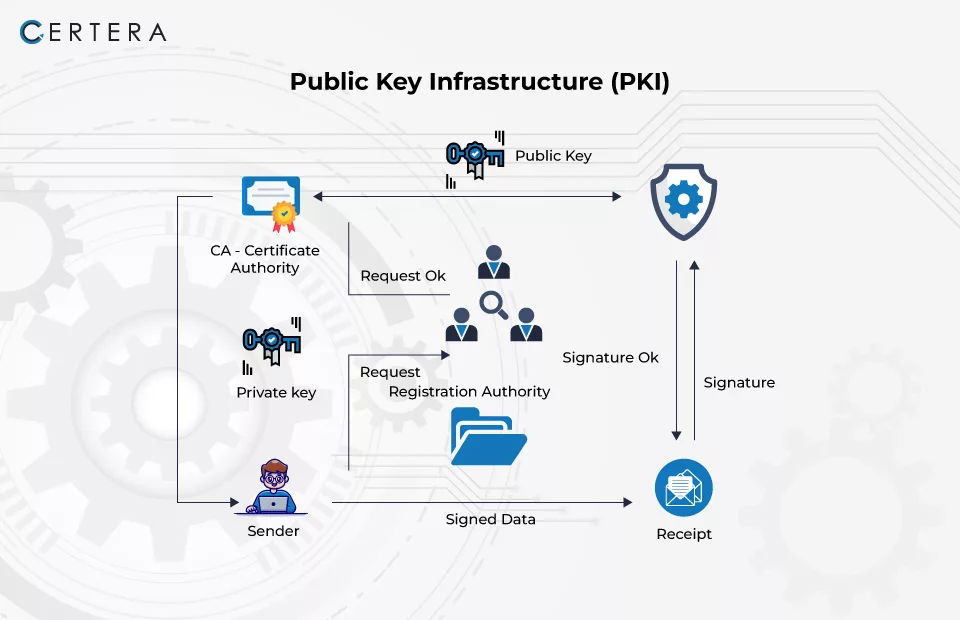
It establishes the identification of endpoints and encrypts the data flow via the network’s communication channels. (as shown above)
PKI architecture exists in multiple forms:
Publicly Trusted PKI
This includes Certificate Authorities like Certera, DigiCert, Sectigo, Entrust, and others that issue digital certificates that are recognized and publicly trusted by clients and operating systems. Here, the PKI architecture is in full control of the CA.
Privately Trusted PKI
If you want to secure internal assets or networks, then a private CA is the best option.
Main Elements or Components of Public Key Infrastructure
Digital Certificates:
These certs enable encryption for a variety of use cases. Some of the common categories include:
- SSL/TLS Certificates: These certificates make the secure padlock icons appear on a web browser, so they will not show “not secure” warnings to users.
- Code Signing Certificates: Ensure the software’s legitimacy and hasn’t been tampered with.
- Document Signing Certificates: These certificates employ cryptographic functions and digital signatures to ensure the document is legitimate.
- Email Signing Certificates: Also known as S/MIME certificates, these provide end-to-end encryption and encrypt email content.
- Client Authentication Certificates: Enable passwordless authentication on the internal network.
Public Key:
It is a cryptographic mathematical key that is available and is used for encrypting or verifying digital signatures.
Private Key:
It is kept secret by the owner and used to decrypt a message encrypted by the public key.
Certificate Authority (CA):
It is the main component that manages all aspects of PKI certificate management, including issuing, revoking, and managing digital certificates.
Do you know there are intermediate CAs as well? Here’s a quick overview.
- Root CAs: The root CA is at the top of the Certificate Authority (CA) hierarchy. It establishes the foundation of trust in a Public Key Infrastructure (PKI) and is kept really safe, usually offline, to ensure security.
- Subordinate CAs: Sitting beneath the Root CA are subordinate CAs. These CAs act as intermediaries between the Root CA and end entities, such as websites or individuals, requesting digital certificates. Unlike Root CAs, these are typically online and actively involved in day-to-day certificate issuance activities.
- Registration Authority (RA): The registration authority behaves as an intermediary between users and the CA. It verifies the legitimacy of entities requesting digital certificates before forwarding the requests to the CA for issuance.
- Public Key Certificate: It is an electronically signed document that verifies public key ownership and is issued by Certificate Authorities.
- Key encryption and secure storage: Private keys are valuable, and if they get compromised, the situation can be troublesome. That’s why these are stored in encrypted vaults.
Most Significant Risks in Certificate Management
Still, in 2024, the management of certificates is an under-recognized problem for many companies. The risks of poor cert management cannot be ignored or overstated; doing so can create the following issues.
Expiration & Renewal Timeline
Just like other things, certificates also have expiration dates and failing to review them on time can lead to security vulnerabilities.
The next big concern is tracking and managing certificate lifecycles across numerous systems and devices without proper oversight.
Certificate Misconfiguration
Incorrectly configured certificates can lead to potential issues, such as weak encryption settings, misused certificate authorities (CAs), and compatibility problems.
Recommended: What is Cryptographic Failure? Real-life Examples, Prevention, Mitigation
For instance, if a cert gets misconfigured, cybercriminals can hack the sensitive data, resulting in inaccessible services or displaying warning messages to users.
Lack of Visibility and Control
This is the most significant risk, especially in large corporations where maintaining visibility into all issued certificates and their usage is difficult.
In fact, 71% of organizations are not aware of how many certificates exactly they have. As a result, without centralized monitoring, unauthorized access can lead to security breaches.
Recommended: What is SSL Certificate Monitoring? Explained
Compliance and Governance Challenges
Compliance requirements (e.g., PCI DSS, HIPAA) often mandate strict controls over certificate management. Failure to comply or follow regulations can result in legal consequences, fines, and damage to brand reputation.
For example, the healthcare industry has HIPAA requirements for protecting data and violating rules can result in fines of up to $50,000.
Downtime or Outages
73% of organizations experience unanticipated downtime or outages due to poor digital certificate management. These disruptions can have significant unfortunate impacts on businesses, causing financial losses, reputation damage, and customer dissatisfaction.
Certificate Authority (CA) Compromise
This risk is something that is outside the control of an organization, but we’ll say indirectly it is!
How? If the certificate authority from which you buy the certificate gets compromised, it can undermine the security of all certificates issued by that CA.
That’s why it’s your responsibility to select trusted CAs, like Certera, that implement proper mechanisms to detect compromises and potential breaches.
Key Compromise
The private keys associated with certificates are valuable. If a private key is compromised or leaked, it can be used for unauthorized access or man-in-the-middle attacks.
Certificate Lifecycle Management Best Practices
Reading the above blog, it is pretty clear that managing certificates is not a simple task, but the process can be eased by the following CLM best practices.
Implement Strong Crypto Standards
The effectiveness of cryptography is decided by the crypto standards. With new cyber threats continuously evolving, standards are also being updated to combat them.
The commonly recommended algorithms include AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman) and Hashing.
Follow the below tips to implement strong crypto standards:
- Regularly review all the certificates
- Identify the ones with weak standards
- If you find any certificate that is not according to standards, replace them as soon as possible.
Maintain a Certificate Inventory
Maintaining certificate inventory is one of the best and most essential CLM best practices. Here’s how to do it!
- Make a list of all the digital certificates your organization uses, including both public and private trust certificates.
- Note down important information about each certificate, like when it was issued, when it expires, and what it’s used for.
- Keep all this information in one central location and ensure that the list is regularly checked and updated.
This practice is also necessary for adhering to compliance.
Automate Provisioning & Renewal
By automating the provisioning and renewal of certificates, the chances of manual errors are reduced and timely updates can be ensured. Use tools and scripts to automate certificate issuance, renewal, and deployment processes.
Use Organization Validation (OV) or Extended Validation (EV) SSL
OV SSL and EV SSL Certificates offer better authentication and protection against threats. This helps build trust among users that you care about their data privacy and can’t put that at risk.
The best part is that it provides control over who can issue certificates for your properties, and you’ll have greater visibility.
Perform Weekly Network Scan
Precaution is always better than cure! Right? The same applies here as well!
Why wait for a certificate to get compromised? Instead, run a weekly discovery scan and monitor the CT logs for the domains.
If you find any issue, report it to the certificate authority.
Maintain Certificate Management Procedures Documentation
Always maintain certificate management procedures documentation, including policies, processes, and controls.
No matter if you have established automated processes for certificate lifecycle management, it needs to be continuously monitored. Set up a monitoring system that provides every detail about the certificate, like its expiry and issuance date.
Do not forget to establish a warning system that alerts the owner about impending issues that require their attention.
Recommended: PKI Certificate Management: Avoid Common Pitfalls & Embrace Best Practices
The Bottom Line
To conclude, managing digital certificates with precision and ease is crucial. It involves overseeing digital certificates from the time they’re issued until they’re retired. Proper CLM ensures that certificates are valid, renewed when necessary, and revoked if compromised.
Manage certificates effectively and maintain your organization’s security and integrity. At Certera Digital Security Certificates starts at just $2.99/Yr
