SHA 256 Algorithm: Know Everything About it

Security is a fundamental and absolute requirement in today’s digital and interconnected world. It is essential for preserving service availability, protecting sensitive data, guaranteeing data integrity, and building trust between people, companies, and governments.
Security is essential for maintaining national security, fostering economic stability, and safeguarding individual privacy in a time when technology is the driving force behind innovation and global interconnectedness.
This is when SHA-256 encryption becomes essential. One of the most dependable cryptographic instruments, it contributes to the maintenance of digital trust and data integrity, both of which are essential for security in the contemporary digital sphere.
Hashing and encryption have been the foundational ideas of many other security modules, among the numerous advances in network security. SHA 256, often known as the secure hash algorithm, is a popular hash algorithm with a digest size of 256 bits. Other variations exist, but SHA 256 is often used in practical applications.
Understanding hashing and its functional aspects is a prerequisite to learning how the SHA 256 algorithm works and digging deeper into cybersecurity.
A thorough review of the SHA-256 algorithm is provided in this article. We’ll explore its internal workings, the significance of protecting anything from confidential documents to cryptocurrency, and its role in preserving the trust that underpins our connections via the internet.
What Exactly Is Hashing?
Hashing is a technique of changing any given information into a fixed value. It comprises data blocks converted from the original string into a brief, fixed-length key, or value. It entails putting the data through a mathematical process to transform it into an original, intricate string of letters.
Data integrity may be efficiently and securely verified by hashing. To be sure the data has not been altered or distorted, you can compare the hash produced when you hash a piece of data to a known or anticipated value. If the hash values match, you can be sure the data has stayed the same since it was first hashed.
The irreversibility of hashing is one of its advantages. It is not possible to obtain the original data using the hash value. This makes hashing useful for password storage since it allows you to save a hash of a password rather than the real password. Without requiring the password, the system may hash input from users and compare it to a stored hash value to confirm that it is a valid password.
Hashing is used in Two Main Applications:
Password Hashing:
Before being saved on the server, user passwords are transformed into a hash value on most website servers. For validation, it contrasts the hash value recalculated upon login with the value maintained in the database.
Integrity Validation:
It shares its hash as a bundle with the file when it uploads it to a website. It may recalculate and compare the hash to ensure data integrity when a user downloads it.
SHA-256 Algorithm: What Are Its Characteristics?
The following are some of the SHA algorithm’s most notable characteristics:
Message Length:
The clear text should not exceed 264 bits in length. The size must fall within the comparison range to maintain the digest’s maximum degree of randomness.
Digest Length:
For the SHA-256 algorithm, the hash digest should be 256 bits long; for SHA-512, 512 bits long, and so on. Larger digests often imply many more computations at the expense of space and speed.
Irreversible:
All hash functions, including the SHA 256, are irreversible by design. When you feed the digest through the hash function again, it shouldn’t return its original value; instead, you should receive a plaintext.
You should have a good understanding of the technical prerequisites for SHA at this point. The next part will walk you through the entire process.
What Is the SHA 256 Algorithm?
Secure hash algorithm 256, or SHA-256, is a cryptographic hashing algorithm (or function) used for data integrity verification, file integrity verification, and message integrity verification. It belongs to the SHA-2 family of hash algorithms that transforms a piece of data into a new, unidentifiable data string of a set length using a 256-bit key. A hash value is a random string of letters and integers that has a length of 256 bits.
A simple overview of hashing’s operation.
How Does SHA-256 Work?
The U.S. federal government and many other organizations worldwide utilize SHA 256 as the industry standard. But what does it do on a more superficial level?
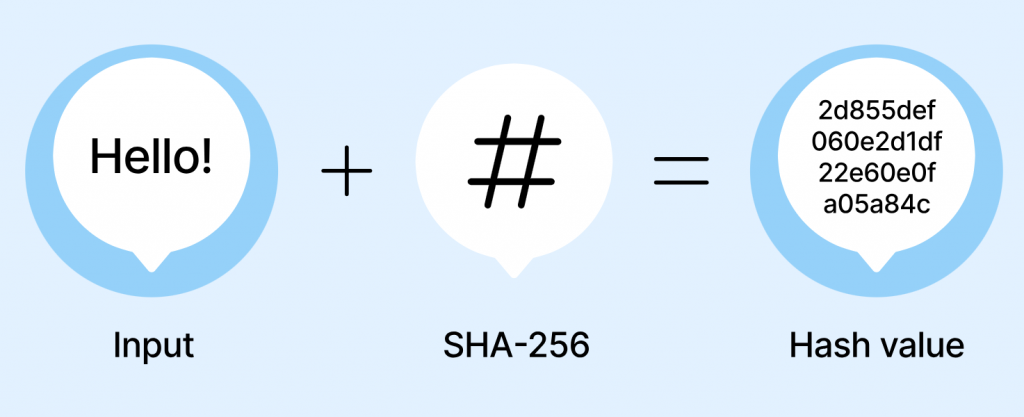
Let us examine the subsequent instance. Let’s say you use a SHA-256 hash method to transcribe the message “Hello” It will seem as follows: 90a90a48e23dcc51ad4a821a301e3440ffeb5e986bd69d7bf347a2ba2da23bd3,…… Say, for example, that you use the same message, “Hello!” The outcome will be a completely different hexadecimal string of the same length.
The SHA-256 has values of three texts that differ by adding/changing the characters displayed in the following image.
One letter can noticeably alter the hash value when added to the message. Notwithstanding the number of characters in the original text, the hash values always have the same number of characters. Because every input, be it a single word or a book, will produce a hash value of the same length, this helps conceal the size of the input data.
What Is the SHA-256 Algorithm Stages?
SHA-256 processes the input data through a cycle of mathematical operations. Preprocessing the input, expanding the message, and performing the message compression function are the stages involved in each cycle. The SHA-256 algorithm consists of the following key steps:
Data Preprocessing:
A one-bit is inserted, followed by zeros, and the length of the original message in bits is appended to guarantee that the input data is padded and extended to be a multiple of 512 bits in length.
Message Expansion:
A sequence of logical operations splits the 512-bit input block into 16 32-bit words, further expanding into 64 32-bit words.
Message Compression:
After the message block has been enlarged to 64 words, it is processed through 64 rounds, each of which consists of many steps:
Find out What the Round Constant is:
Based on the location in the sequence, a distinct 32-bit constant value is created for each round.
Determine the Message Schedule:
The 64-word message block and the round constant create a 64-entry message schedule.
A series of logical operations and the message schedule are used to update the working variables, which are eight 32-bit words that hold intermediate values throughout the hashing process.
Do the Hash Value Calculation:
The 256-bit hash value is generated by combining the final values of the working variables after all 64 cycles have been finished.
A 256-bit final hash value that functions as a digital fingerprint of the input data results from the SHA-256 hash algorithm.
A Look Back at the SHA-256 Hash Algorithms
Developing the Secure Hash Algorithm (SHA) is an example of a dynamic path towards enhancing online safety. In 1993, SHA-0 was introduced as a pioneering effort to safeguard digital data. But because of these flaws, SHA-1 was developed in 1995 as an improvement but was still open to intrusions.
This led to the 2001 introduction of the SHA-2 family, which included the encryption algorithm SHA-256. Due to its robust security characteristics, this 256-bit hash function immediately gained popularity and was extensively employed in vital fields such as password storage, digital signatures, and data integrity verification.
SHA-256 remained significant even after SHA-3 entered the picture in 2015 because of a challenge. Although SHA-256 hash continued to be necessary, SHA-3, based on the Keccak algorithm, provided an alternative cryptography method.
It still has a significant impact, particularly on cutting-edge technology like blockchain, which protects Bitcoin transactions and upholds the reliability of distributed records. The development of SHA hashing algorithms over time highlights a continuous dedication to improving online safety.
In our constantly evolving technological environment, the SHA-256 algorithm proves the enduring value of a cryptographic instrument that safeguards information and bolsters digital confidence.
A Brief Overview of SHA-256 Terminology
We must understand the words in the preceding definition to comprehend SHA 256. Now, let’s get started:
Cycles/Rounds:
Previously, we noted that the number of rounds in each of the six SHA-2 algorithms is one of their variations. A round is a series of operations the algorithm performs repeatedly to jumble the input completely. The SHA 256 algorithm has 64 iterations.
Additive Constants:
We refer to the values added to the blocks as additive constants. The blocks in SHA 256 are added using 64 constants. These values are the cube roots of the initial sixty-four prime numbers. s. The fractional numbers’ first 32 bits are used in this stage.
Shift Amount:
Bits are shuffled using a predetermined shift amount mechanism. The blocks of SHA 256 are split up into eight 32-bit segments. The data is then randomly and jumbledly moved in a certain way using these eight components.
The SHA 256 Algorithm’s Features
A powerful cryptographic tool, the SHA-256 algorithm has characteristics that guarantee the security and integrity of data. The following are some salient characteristics of SHA-256 encryption:
Cryptographic Hash Function:
SHA-256 generates a fixed-size output (hash value) from an input (message). Because each unique input produces a unique output that seems random, deducing the original message from the hash value is very difficult.
High Collision Resistance:
It means that it is statistically unlikely for two distinct inputs to give the same hash value, which is what SHA-256 is known for. This characteristic guarantees that a significant difference in the hash value is produced even with a bit of alteration in the input.
The Avalanche Impact:
Occurs when a slight alteration in the input data triggers a significant alteration in the hash value, which cascades into the output. Because of this avalanche effect, even small changes to the input guarantee wildly divergent hash returns.
One-Way Function:
Due to computational constraints, It is not possible to reverse the hashing process and get the original input from the hash value since SHA 256 is meant to be a one-way function. This characteristic makes it useful for digital signatures and password storage.
Fixed Output Length:
A hash value of 256 bits (32 bytes) is produced by SHA-256. The reliable and uniform results provide effective data comparison and integrity confirmation.
Deterministic:
When given the same input, the SHA 256 algorithm will always yield the same hash value. Processes for authentication and verification can be consistent because of this predictability.
Performance:
The security and efficiency aspects are balanced using SHA 256. It may be used for various purposes since it provides a high degree of security and computer quickly.
Broad Applicability:
SHA 256 is extensively used in many fields, including data integrity verification, blockchain technology, digital signatures, and password storage.
Uniformity:
SHA 256 is a NIST-approved standard; its execution and security features have been carefully examined and assessed.
Applications for the SHA 256 Algorithm
SHA 256 has demonstrated its ability to secure a multitude of facets of our online existence. Let’s examine the many uses for the SHA 256 algorithm:-
Ensuring the Integrity of the Data
Data integrity is vigilantly guarded by SHA 256. Converting data into a fixed-size hash value ensures that even the slightest change to the input yields a radically different response.
Discrepancies may be quickly identified by comparing the hash values of the original and received data, which makes it an essential tool for preserving the reliability and correctness of digital information.
Authenticating Digital Signatures
Digital signatures give digital conversations and document validity. By generating a hash value for the material that must be signed, SHA 256 is essential.
Recommended: Digital Certificate vs Digital Signature: 10 Key Difference
The digital signature is then created by encrypting this hash value using a private key. To confirm the sender’s identity and the document’s integrity, recipients can use the matching public key to decode and validate the signature.
Integrity of Files
Documents, movies, software executables, you name it, and hashing may assist in maintaining the integrity of any file. It’s crucial since you can confirm that the file hasn’t been altered, whether you need to update software or sign a contract you’ve been working on for weeks.
Determining Blockchain Transactions
SHA 256 is a fundamental feature of blockchain technology, prioritizing security and transparency. It links transactions into blocks and is utilized in the proof-of-work method.
The hash of each new block is contained in the preceding block’s hash, forming an unchangeable chain. The SHA-256 algorithm guarantees the integrity and consistency of the whole blockchain network.
Hashing Passwords
Passwords should never be stored or saved in plain text. Passwords are safely hashed using SHA 256 and salt, a random number, before being stored.
Users can verify the authenticity of a password without disclosing the actual one by hashing their password and comparing it to the saved hash when they log in. This prevents possible compromises of critical information.
Illustrations of Applications for SHA 256
SHA 256 is among the most dependable algorithms regarding message integrity and authenticity. Various encryption and authentication techniques and procedures are employed with it, such as:
SSL/TLS: The encryption methods known as SSL/TLS, or secure socket layer and transport layer security, ensure the privacy, integrity, and confidentiality of data while it is being sent.
PGP: An encryption technique called Pretty Good Privacy (PGP) is used to sign, encrypt, and decrypt files, directories, emails, and disc partitions.
S/MIME: The algorithm known as S/MIME, or secure/multipurpose internet mail extensions, protects the secrecy and integrity of communications.
Blockchain: The hash value of the current block in a blockchain is determined by using the hash values of previous blocks.
SSH: Data may be sent securely between two devices using the Secure Shell (SSH) protocol.
IPsec: Internet protocol security, or IPsec, is a group of protocols intended to protect data transmission between various IP networks.
SHA 256: Is It Secure?
Can it break the SHA 256 algorithm? Yes, if you have an almost limitless amount of time and resources. However, in actuality, no one has yet. SHA 256 is used by the Bitcoin network, which is thought to be among the world’s most secure networks. TLS certificates utilize SHA 256 to verify their integrity for the same reason.
The Cryptographic Module Validation Programme (CMCP) of the National Institute of Standards and Technology (NIST) and the Communication Security Establishment (CSE) may be used to verify an algorithm that incorporates the SHA 256 standard. This formal verification is needed for several U.S. government applications.
Wrap up!
Web data security relies heavily on the SHA-256 hash algorithm. We didn’t delve too deeply into the maths or the underlying functions in this post; we only touched the surface. Still, you now have a rough idea of the intent and application of the method.
The industry-standard hashing technique for data and file integrity will continue to be SHA-256 until we develop a quantum computer powerful enough to break complicated hash functions.
For now, SHA-256 will be used in encryption and authentication methods as we are still a few decades away from such a situation.
FAQ’s
What Is an SHA-256 Fingerprint?
The SHA-256 method creates a distinct digital representation of data called the SHA-256 fingerprint.
What exactly is the SHA 256 Algorithm?
Making a distinct digital fingerprint of a piece of data, such as a file or message, is the aim of the SHA-256 algorithm. A sophisticated mathematical algorithm that yields a distinct output value is applied to the input data to generate a SHA-256 hash.
Why is the SHA Algorithm Used?
The term secure hashing algorithm is SHA. A tweaked variant of MD5, SHA, is used to hash certificates and data. A hashing algorithm uses bitwise operations, modular additions, and compression functions to condense the input data into a more diminutive form that is unintelligible.
Recommended: What Distinguishes SHA-1, SHA-2, SHA-256, and SHA-512?
How Is SHA-256 Decrypted?
Since SHA-256 encryption is irreversible, it cannot be broken.
Is SHA 256 a Unique Hash?
Hashes are not unique. It’s simple to demonstrate this: since a SHA256 hash consists of only 256 bits, some 264-bit inputs must have the same hash if all conceivable inputs are hashed; otherwise, there wouldn’t be enough hashes to allow for variety.
In SHA 256, How Many Rounds are there?
64 shots. A round is a series of operations the algorithm performs repeatedly to jumble the input completely. The SHA 256 algorithm has 64 iterations.
What is the Symmetry or Asymmetry of SHA-256?
HS256 (HMAC with SHA-256): a symmetric method, meaning that both parties share a single private key that needs to be kept secure. It is essential to ensure the key is secure because it is needed to create and validate the signature.
