What Is Public Key Encryption? Public vs. Private Key Encryption
According to a report by PingSafe, 45% of data breaches occur on the cloud, and 80% of companies have experienced an increase in the frequency of cloud attacks.
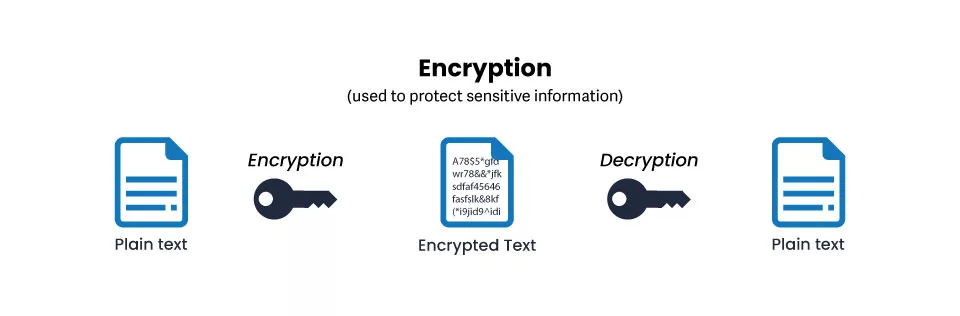
To combat these attacks, encryption is used so that only authorized parties can read the encoding information.
Now, encryption has two types, i.e., public key encryption and private key encryption. In this blog, we will discuss everything about these and how they differ from each other.
Let’s begin!
What is Public Key Encryption?
Public key encryption, or asymmetric encryption, is a cryptographic method that utilizes a pair of keys to secure digital communication and transactions.
This method uses two related keys:
- Public key (Used to encrypt data)
- Private key (Used to decrypt data)
The Rivest-Sharmir-Adleman (RSA) algorithm is used for public key encryption, as it is especially useful when sending sensitive data over an insecure network.
It’s based on the idea that it’s easy to multiply two big prime numbers together, but it’s really hard to figure out what those two prime numbers are if you only know their product.
How Public Key Encryption Works?
Here’s the typical process of how public key encryption works!
Key Generation: By using the cryptographic algorithm, the user generates a pair of keys, namely, a public key and a private key.
Both keys are co-related, and one private key can only have one public key or vice versa. In simple terms, these come in pairs, and a private/public key will only work with the associated public/private key.
Recommended: How to Generate Your Private Key With Your Certificate?
Encryption: Let’s say Jes (sender) wants to send a secure message to Ruth (receiver). To do this, Jes uses Ruth’s public key to encrypt her message. This process transforms the original message into an unreadable format (ciphertext).
Recommended: What is Encryption? How does it Work?
Decryption: Ruth receives the encrypted message from Jes. To read it, she uses his private key to decrypt and retrieve the original message. Since the private key is kept secret and only known to Ruth, the decryption process ensures that only Ruth can access the message.
How SSL/TLS Certificates use Public Key Encryption?
When a website wants to secure its communication with clients, it obtains an SSL/TLS certificate. It contains the public key, which is shared publicly, and the private key is installed on the origin server, which is “owned” by the website.
When a client (e.g., a web browser) connects to a secure website, the TLS handshake process begins.
The server sends its SSL/TLS certificate (including the public key) to the client. During the handshake process, the client and server exchange keys using public key cryptography. They agree on session keys (temporary keys) using asymmetric encryption algorithms like RSA or Diffie-Hellman.
Finally, the client encrypts a session key with the server’s public key and sends it securely to the server.
Advantages of Public Key Encryption
Public key encryption offers several advantages, as explained below.
- It ensures that the sensitive information between two parties remains secure and only the intended recipient can access the message.
- Maintains confidentiality by allowing data to be encrypted with a recipient’s public key.
- It supports non-repudiation. This means that a sender cannot deny sending a message that has been digitally signed with their private key.
- Enables strong authentication mechanisms.
- It is resistant to key compromise, which entails that even if a public key is compromised, the corresponding private key remains secret and secure.
- Public key encryption forms the basis of secure online transactions, like e-commerce and online banking. It ensures that sensitive or private information like credit card details or personal data is transferred securely over the Internet.
Limitations of Public Key Encryption
Public key encryption, despite its many advantages, also has certain limitations.
- Slower and require more computing power compared to other types of encryption.
- These are prone to data security breaches and man-in-the-middle (MITM) attacks.
- Encrypting large files or data with public key encryption can be inefficient due to its slower processing speed and larger key sizes.
- Uses larger keys, which can be challenging to handle and store.
What is Private Key Encryption?
In private or symmetric key encryption, a single key is employed for both data encryption and decryption. Here, the same secret key is utilized by both the recipient and the sender to encrypt and decrypt messages.
How Private Key Encryption Works?
Below is a simplified explanation of how private key encryption works.
- Key Generation: A secret key is generated, which is kept confidential and shared securely with the sender and recipient.
- Encryption: To encrypt a message, the sender uses the secret key to transform the plaintext message into ciphertext (encrypted data).
- Transmission: The message is transferred through a communication channel, like the Internet.
- Decryption: The recipient uses the same secret key to decrypt the ciphertext and retrieve the original plaintext message.
Limitations of Private Key Encryption
- One of the major limitations of private key encryption is key exchange. Both the sender and receiver must possess and securely share the same secret key. If the key is compromised, it can lead to data loss or unauthorized access.
- Not suitable for secure communication between multiple parties.
- It does not provide a secure way to exchange keys between parties.
Advantages of Private Key Encryption
Some of the advantages of private key encryption are explained below.
- This type of encryption is fast and efficient for encrypting large amounts of data because it uses a single secret key for the procedure of both encryption and decryption.
- Managing one secret key per pair of communicating parties is simpler.
- It is a flexible encryption technique used for a variety of applications and environments, including email, secure file transfer, and web transactions.
- It is one of the most secure forms of encryption and works well to encrypt large files or data in bulk.
- Allows for secure communication between parties that share the same secret key, as long as the key remains private and is shared securely.
- Easy to understand and implement because it involves using just one secret key.
Public vs. Private Key Encryption: Difference
Below are some of the notable differences between public key encryption and private key encryption.
| Particulars | Public Key Encryption | Private Key Encryption |
| Key management | Involves managing a pair of keys (public and private) | Uses a single secret key |
| Complexity | More complex | Less complex |
| Key exchange algorithm | Diffie-Hellman is a widely used public key encryption algorithm for key exchange | RSA is a popular private key encryption algorithm |
| Use cases | Suitable for digital signatures and secure key exchange | Not applicable for digital signatures or secure key exchange |
| Encryption algorithm | Commonly used in PGP encryption | Commonly used in AES encryption |
| Security | Provides features like key exchange and digital signatures, enhancing security for communication and data integrity. | Relies on secure key distribution to maintain confidentiality, typically used for direct communication between trusted parties. |
| Knowledge requirement | Message sender does not required to know the recipient’s private key | Both message sender and recipient must possess the same private key |
| Common usage | Utilized in SSL/TLS protocols for secure web browsing | Employed in symmetric-key cryptography |
| Vulnerabilities | Vulnerable to man-in-the-middle attacks and brute-force attacks | Vulnerable to key distribution and insider attacks |
| Key privacy | Public key is openly shared and known, while the private key remains confidential | Private key is kept confidential by both the sender and recipient |
Now that we have understood everything about private and public key encryption, you must be wondering which one is right for your business.
Choosing between public key encryption and private key encryption depends on your business’s specific security requirements and use cases. Both of these have their own pros and cons, which we have explained above. So, analyze them carefully and choose accordingly.
Conclusion
To conclude, understanding the differences between public and private key encryption is essential for implementing effective data protection strategies in business environments.
To ensure more website security, get certified SSL certificates from Certera, starting from $3.99/Yr.
