How to Guide on Settingup Passwordless SSH on Linux?

Have you ever felt threatened at a place that was actually meant for your convenience? Yes, we are talking about your digital space right now. No doubt, the advancement in technology was to ensure our comfort to elevate the business, but now it has been a place full of terrors of cybercrime.
But how can you prevent such dangers when providing sensitive information is the only way to access any particular service? Well, what if I tell you no more? Or that you don’t need your passwords to sign into SSH in Linux?
We have got the simplest way to ignore the use of your passwords anymore to set up your SSH via Linux. Protecting your network from potential breaches is crucial, and one effective approach is to adopt a passwordless authentication system.
By eliminating traditional passwords, you can fortify your security defenses and minimize the risk of becoming the next victim.
All you have to do is follow each method carefully, stay tuned until the end to avoid any warnings or important notes, then sit back and relax! As you will have a secure environment ever since. So, let’s get started, readers.
Why Should You Opt for Using Passwordless SSH in Linux?
To begin, credentials serve as the gateway to your organization, and cybercriminals are drawn to them just as vampires are drawn to blood. These malicious individuals actively target credentials using phishing and man-in-the-middle attacks.
However, what if there is nothing to steal? Implementing passwordless SSH in Linux elevates the security game to a new level.
The Alarming Risks and Threats:
According to SpyCloud, a leading cybersecurity company, a staggering 721.5 million stolen credentials were recovered from the darknet in 2022 alone. This alarming statistic is a wake-up call, emphasizing the urgent need for more robust authentication methods.
Cybercriminals often exploit weak passwords or use sophisticated techniques like phishing and brute-force attacks to gain unauthorized access to networks. You can remarkably reduce the chances of falling prey to these malicious tactics by going passwordless.
Embracing Passwordless Authentication for a Safer Digital Space:
Passwordless authentication replaces the traditional username-password combination with more secure alternatives, such as biometrics, cryptographic keys, or multi-factor authentication (MFA).
This innovative approach eliminates passwords’ vulnerability and enhances your network’s overall security posture.
Secure Shell (SSH) and Passwordless Login in Linux:
SSH is a prominently used protocol for secure remote access to Linux servers. Unfortunately, attackers often target SSH login credentials to gain control over a system. By implementing passwordless login for SSH in Linux, you can eliminate the risk associated with weak or compromised passwords. Instead, you’ll rely on cryptographic keys, providing a robust and secure method for authenticating users.
How is it Convenient to use Passwordless SSH?
Have you ever wondered why many developers store their project usernames and passwords in their commits? They do so for the same reason you might be tempted to use the same password across multiple websites: convenience.
However, this convenience can come at a hefty cost if attackers gain access to your credentials.
According to IBM, such a breach can result in a cost that exceeds the average expense of a data breach, which was already estimated at $4.35 million per breach for organizations globally in 2022.
How do you Log in to SSH Without a Password in Linux?
Generate a Cryptographic Key-Pair:
Begin by generating a public-private key pair on your local machine using the ssh-keygen command.
Copy the Public Key to the Remote Server:
Use the ssh-copy-id command to securely transfer your public key to the Linux server you wish to access.
Configure SSH to Use Key-based Authentication:
Edit the SSH configuration file on the server (/etc/ssh/sshd_config) and ensure that PasswordAuthentication is set to ‘no’ and PubkeyAuthentication is set to ‘yes.’
Test your Passwordless Login:
Once the configuration is complete, attempt to log in to the remote server using SSH. You should be able to access the system without entering a password.
How to Set Up Passwordless SSH in Linux with Quick Steps?
SSH quickly gained popularity and became an essential tool in the field. Why? Because it was a network communication protocol that offered the following:
- Execution of commands.
- File transfers.
- Configuration of remote servers.
- Remote management of systems and applications.
- The significant advantage of SSH was its use of encryption, which ensured that communication and data transmission were protected against eavesdropping and dangerous man-in-the-middle attacks.
SSH supports various authentication methods, but password-based and public-key-based authentication are the two most commonly used. Using a password becomes optional with public-key-based authentication, also known as key-based authentication or passwordless SSH.
Considering that Verizon has identified stolen credentials as the leading cause of web application breaches, it would be prudent to consider utilizing this method.
Before setting up SSH without a password in Linux, it is crucial to ensure that you still need an SSH key pair saved on your device.
Ensure Whether Your Client Already Has an SSH Key
In this stage, avoid overwriting existing keys by verifying their absence. Here’s how you can check for any existing keys:
Step 1: Open a terminal using the shortcut (e.g., pressing CTRL+ALT+T) or clicking the Show Applications button on the dash bar.
Step 2: In the search box, type “terminal” and select the terminal application.
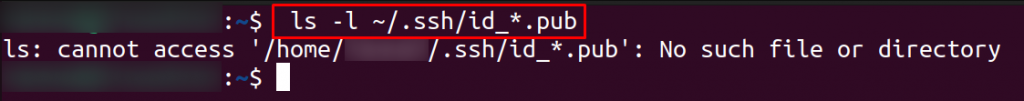
Step 3: Run the command “ls -al ~/.ssh/id_*.pub.”
If you receive an error message such as “no such file or directory” or “no matches found,” it indicates that you do not have any SSH keys, and you can proceed to the next step.
Step 4: Did you discover that you already possess a key pair? In that case, you have two options:
You can proceed directly to the next stage to continue setting up passwordless SSH in Linux or back up the existing keys and generate new ones by following the above instructions.
Create Your SSH Key Pair on Linux to Avoid Passwords
SSH keys are generated using a key generator tool in the SSH command line tool suite. This tool employs a one-way mathematical algorithm to create public and private keys.
To generate your key pair on your local machine, follow these steps:
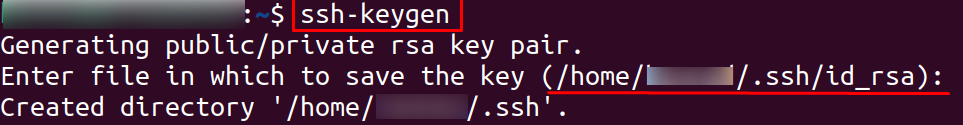
Step 1: Open the terminal and enter the command “ssh-keygen” followed by pressing Enter.
Step 2: The key generator will default generate Rivest–Shamir–Adleman (RSA) based keys.
- However, SSH supports other algorithms, such as DSA and ECDSA.
- If you wish to use a different algorithm, specify it by adding “-t” followed by the algorithm name to the command. For example, “ssh-keygen -t dsa”.
How to Get Additional Security?
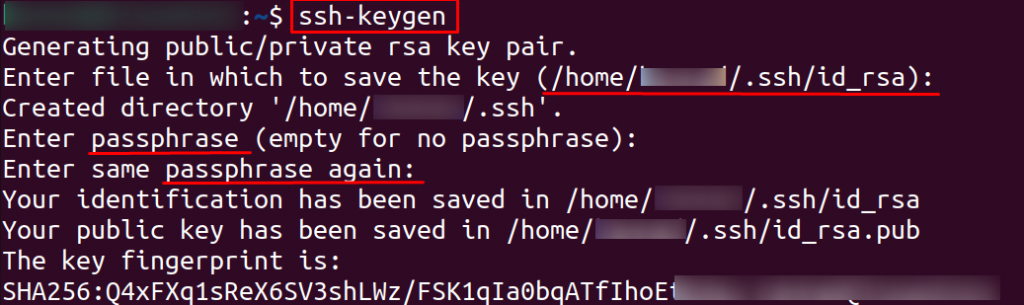
When prompted, specify the path to the file where you want to store your RSA private key.
- For added security, consider storing the private key in a secure location, such as Sectigo Certificate Manager. In this example, we will stick to the default folder (~/.ssh).
- You will have the option to set a password for the private key. If you choose not to set a password, leave it blank and press Enter.
- Alternatively, enter your chosen password, noting that the characters will not be visible as you type.
- Confirm the password by re-entering it. This password will only be required when starting a new session.
- Using a password for an additional layer of security is recommended, even though it may be more convenient for fully automated systems to use SSH without a password. Enter the password only once at the beginning of each session.
You have successfully generated your key pair. The private key (id_rsa) and public key (id_rsa.pub) will be stored in the .ssh folder.
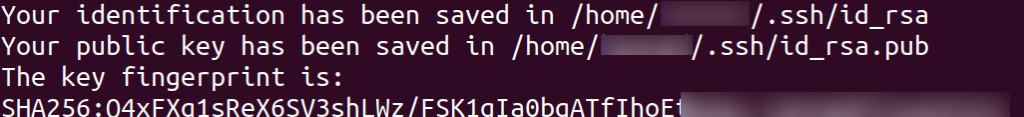
Check the Successful Generation of Keys and Copy SSH Public Key
To confirm the successful generation of the keys, you can use the command “ls -al ~/.ssh/id_*.pub.” Or “ls -l /home/your_username/.ssh/” to check the contents of the .ssh directory and verify if the public and private keys are saved on your device.
Then, enable passwordless access to the remote server. You need to copy the public key and upload it to the server. Follow these steps to accomplish that:
Step 1: Open the terminal and enter the command “ssh-copy-id” followed by your server’s username, IP address, or hostname.
The command should be in the format:
ssh-copy-id username@server_ip_address.Step 2: When prompted, enter the password you usually use to access the server. As you type the password, it will not be displayed on the screen for security reasons. It can be protected against shoulder surfing.
Step 3: After authentication, your public key will be automatically added to the remote user-authorized keys file. It enables you to access the server without being prompted for credentials.
Step 4: Once you copy and upload the public key to the server, establish a secure connection using key-based authentication. It will eliminate the need for passwords during SSH sessions.
Log in to your Server and Verify your Passwordless SSH
Congratulations on completing the setup of passwordless SSH in Linux!
However, verifying if the configuration is successful before you begin celebrating is essential. You can do this by testing the login to your remote server using the SSH command.
Follow these steps:
Step 1: Open your terminal and type the command “ssh server_username@server_ip_address” (or hostname) into the terminal.
QUICK NOTE: Make sure to replace “server_username” with the actual username used on the remote server and “server_ip_address” (or hostname) with the corresponding IP address or hostname.
Step 2: Press Enter to execute the command.
Step 3: If the setup is successful, you will be logged in to the remote server without being prompted for a password.
Step 4: The above action confirms that the passwordless SSH setup is functioning correctly.
Why my SSH passwordless login is not working in Linux?
When facing difficulties with SSH passwordless login, consider the following checks:
Target Server Verification Steps:
Step 1: Ensure that the id_rsa.pub file has been added to the $HOME/.ssh/authorized_keys file for the specific user on the target server.
# cat $HOME/.ssh/authorized_keysStep 2: Verify that the write (w) bit is not set for the group or others on the user’s home directory on the target server.
Step 3: Examine the sshd_config file on the target server for any access restrictions. Pay attention to the presence of a PubkeyAcceptedKeyTypes entry and confirm that the necessary key types are defined.
Step 4: For more detailed information, enable debug mode for sshd on the target server and attempt an SSH connection to it.
For example, the debug logs might display the following error:
debug2: input_userauth_request: try method public key [preauth]
debug2: userauth_pubkey: valid user <username> querying public key rsa-sha2-512
userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedKeyTypes [preauth]
debug2: userauth_pubkey: authenticated 0 pkalg rsa-sha2-512 [preauth]
Step 5: Check the sshd_config file for a PubkeyAcceptedKeyTypes entry. If present, ensure that it includes rsa-sha2-256 and rsa-sha2-512. If not, add these key types at the end of the line in sshd_config. Remember to stop and restart the sshd service.
These troubleshooting steps can address common issues encountered when SSH passwordless login is not functioning as expected. Still facing issues? No worries!
Did your Remote Server’s SSH Set up to Accept Public Key Authentication?
To confirm this, follow these steps:
Navigate to the /etc/ssh/sshd_config file and access it using your preferred text editor.
Ensure that the “PubkeyAuthentication” option is set to “Yes.” If it is not already set to “Yes,” make the necessary modification, save the changes to the file, and proceed to restart the SSH service.
If you encounter trouble with the passwordless SSH setup again, it’s essential to perform the following checks:
Did You Copy the Public Key to the Correct Location?
Log in to your server by providing your username and password. Navigate to the home directory of your remote server and verify if the public key is located in the “~/.ssh/authorized_keys” file. You can use the command “cat .ssh/authorized_keys” to view the file’s contents.
If the public key is not in the “~/.ssh/authorized_keys” file
Here, you must move it to that location. Once you’ve moved the key, try the passwordless login again to see if it resolves the issue.
Check the permissions of the “~/.ssh/” directory. It should be set to 700, which restricts access to only yourself. You can modify the permissions using the “chmod 700 ~/.ssh” command.
Verify the permissions of the “~/.ssh/authorized_keys” file. It should be set to 600, allowing only you to read and write the file. You can adjust the permissions using the command “chmod 600 ~/.ssh/authorized_keys”.
How to Disable Authentication for SSH Password?
Suppose you desire to enhance the security of your remote server connections to a level comparable to the North American Aerospace Defense Command (NORAD) at Cheyenne Mountain.
In that case, disabling password authentication in your SSH setup is crucial. Follow these steps to achieve it:
Step 1: Access your remote server as the root user using the command:
ssh sudo_user@server_ip_address.Step 2: Navigate to the typically located in the.SSH folder at /etc/ssh/sshd_config.
Step 3: Launch the file with your preferred text editor and change the following entries to “no“:
PasswordAuthentication.
ChallengeResponseAuthentication.
UsePAM.
Step 4: Save the modifications and restart the SSH service using one of the following commands:
sudo systemctl restart ssh (for Ubuntu and Debian servers).sudo systemctl restart sshd (for Fedora or CentOS servers).Step 5: Suppose you still question the importance of investing your time in setting up passwordless SSH in Linux, considering that SSH already provides secure connections through encryption.
In that case, we have some insights that might change your perspective on the value of this knowledge.
Tricks to Safeguard Your Sensitive Passwords and Codes
No matter how complex you create your passwords, attackers have methods to crack them. And, in certain instances, these compromises are simply beyond your control.
For example, did you write down your passwords or reuse them for multiple accounts? Both of these practices are unwise. What if you misplace those written notes or if another account that uses the same password gets hacked? A malicious third party could discover your password, and you’ll be in trouble.
According to the GitGuardian report, in 2022 alone, 10 million credentials were exposed due to developers including them in GitHub commits. That’s alarming. Such is life; we all make mistakes.
However, certain errors can be avoided by employing the appropriate defensive security techniques.
How can you achieve that?
- Get rid of password-only authentication, which is vulnerable to brute force and phishing attacks.
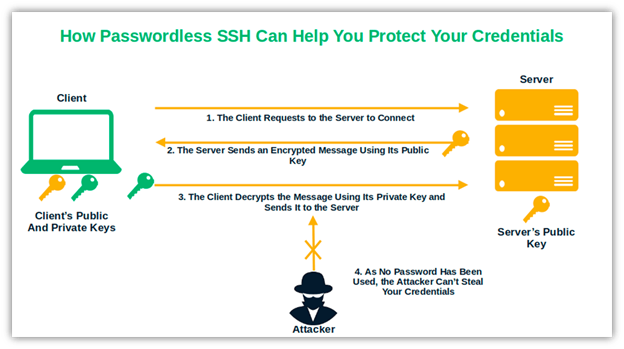
- Ensure the secure storage and protection of your private keys.
- Follow the best practices for SSH key management.
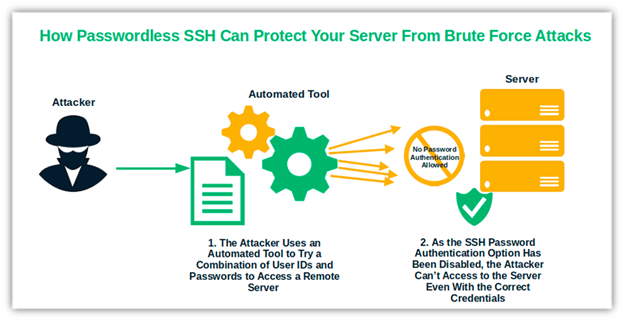
- Since keys do not expire, you must handle them with care to prevent compromise. By implementing these techniques, you can mitigate many of these risks. No more stolen passwords through man-in-the-middle or brute force attacks.
It’s a Wrap!
By implementing passwordless SSH in Linux, you can enjoy the utmost convenience while also eliminating the risk of having your credentials stolen whenever you log in to your remote server. How does it work? Once you initiate a session, you will no longer need to enter your credentials.
Our brains lack the capacity to store such an extensive assortment of jumbled characters as passwords. So, an SSH setup without a password in Linux can significantly reduce the burden of remembering numerous credentials. You won’t have to concern yourself with regular password changes.
