How to Create CSR and Import Code Signing Certificate in Azure KeyVault HSM?
Ensuring the security of your data in today’s vicious cyberspace requires encrypted connections, generating certificates, and securing your private keys. Microsoft Azure KeyVault is an effective and trustworthy solution to these important security requirements.
Azure Key Vault protects your keys using HSMs verified to FIPS 140-2 Level 2 and Level 3 standards. This compliance ensures that your assets are secured within the hardware, offering reliable security and confidence.
This tutorial will use Microsoft Azure KeyVault for secure key management.
We will guide you through importing certificates into Microsoft Azure KeyVault, creating Certificate Signing Requests (CSRs), and generating private keys. Moreover, we will discuss how you can leverage KeyVault’s ability to guarantee the highest integrity and confidentiality for your confidential information, focusing on cloud Hardware Security Modules (HSM).
To protect your data and strengthen your security posture in the constantly changing cyber landscape, let’s explore secure key management on Microsoft Azure KeyVault.
Important Note: Legitimate certificates like DigiCert Code Signing and DigiCert EV Code Signing support the Azure Vault Standard and Premium levels! For Cloud HSM, a Premium Subscription is a must.
Steps to Create a Certificate Signing Request (CSR) in Microsoft Azure Cloud HSM
Use Microsoft Azure KeyVault to create a Certificate Signing Request (CSR) by carrying out the following steps:
1. Go into your Azure Portal and select the “Create a resource” option to set up the Azure Key Vault.
2. To start your vault, search for “Key Vault” and click “Create“.
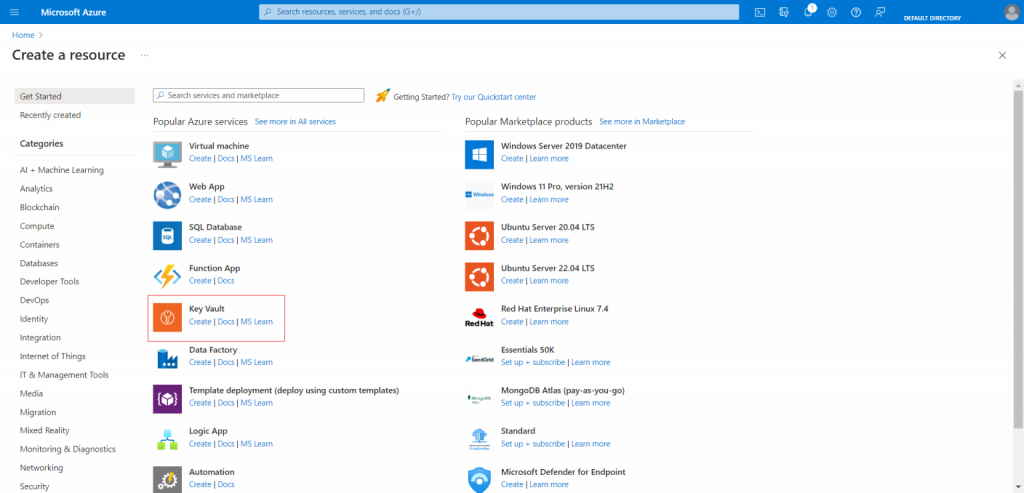
3. Create your Key Vault by choosing the settings that best suit your application.
Note: Choose the “Premium” price category to comply with the FIPS 140-2 standard. If you decide against selecting “Premium,” there’s a chance your certificate may be canceled.
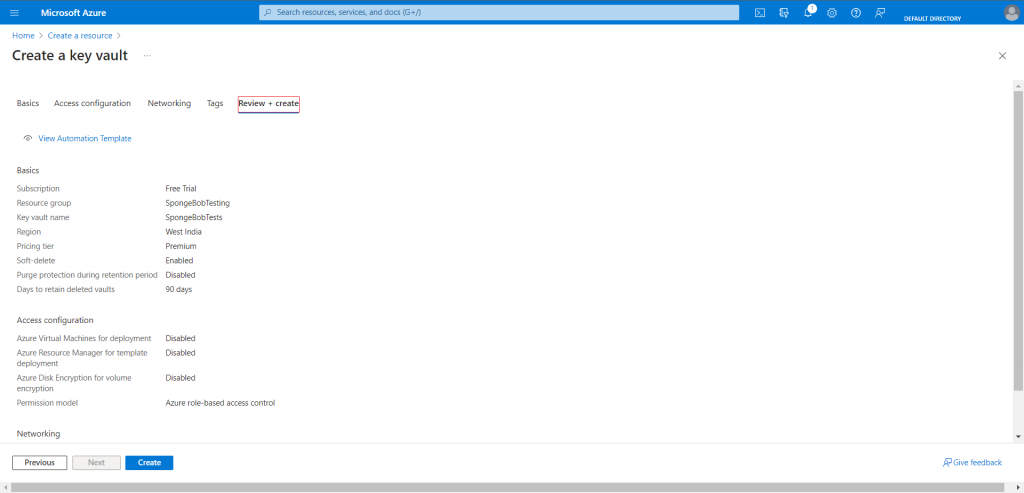
4. After creating your vault, Please select “Certificates” from the action bar on the left. To get started creating your Code Signing CSR, select “Generate/Import“.
5. Enter the subject name and certificate name. The company name needs to appear as a subject name, and the name of the company should be the subject line. Ensure that the subject name is defined using CN=.
6. After selecting Advanced Policy Configuration, change the Type of Certificate Authority to non-integrated CA.
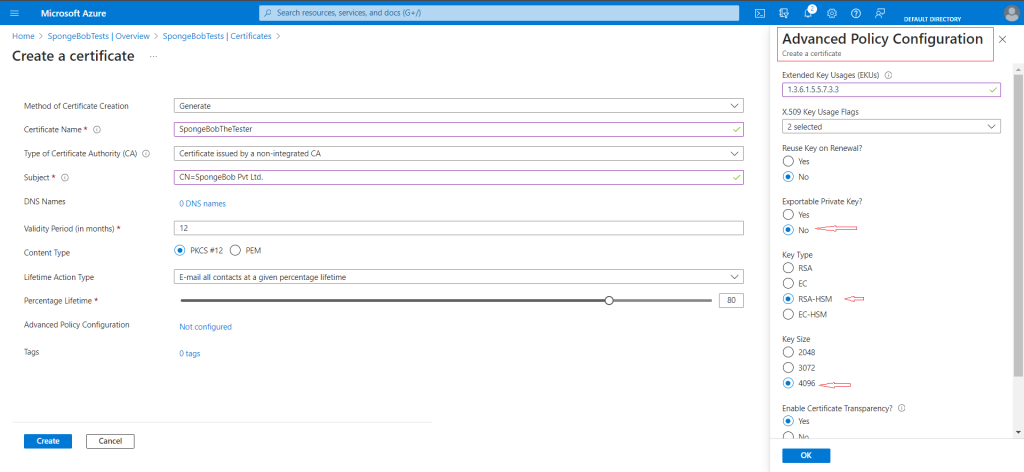
Add 1.3.6.1.5.5.7.3.3 to the Extended Key Usages (EKUs) field.
This EKU recognizes the certificate as a Code Signing certificate.
Additionally, you’ll be required to select RSA-HSM as the “Key Type” and “Exportable Private Key” as No.
Note: Every code DigiCert signing certificate must be issued with a minimum key size of 4096 bits.
7. Click “Okay” and “Create” after completing the policy configuration.
8. The certificate will appear as an “In progress” certificate under the Certificates tab.
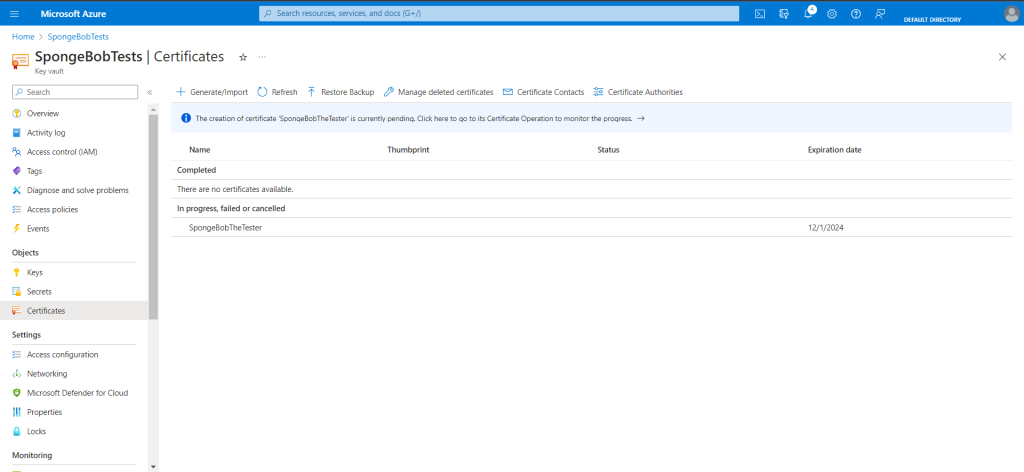
9. In progress, click the certificate you have. Click “Download CSR” after selecting “Certificate Operation.”
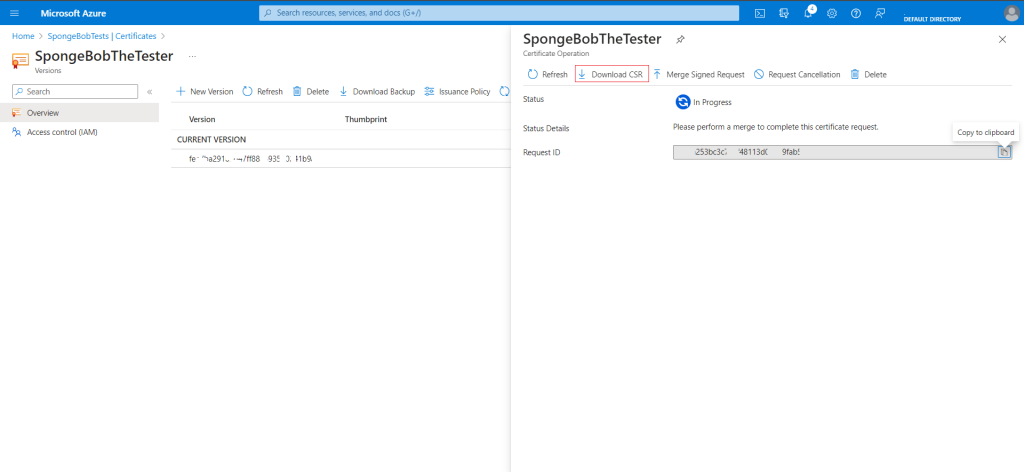
10. Save the CSR file in a secure location of your preference.
11. Navigate to the order enrollment page and go to the “Input CSR” section.
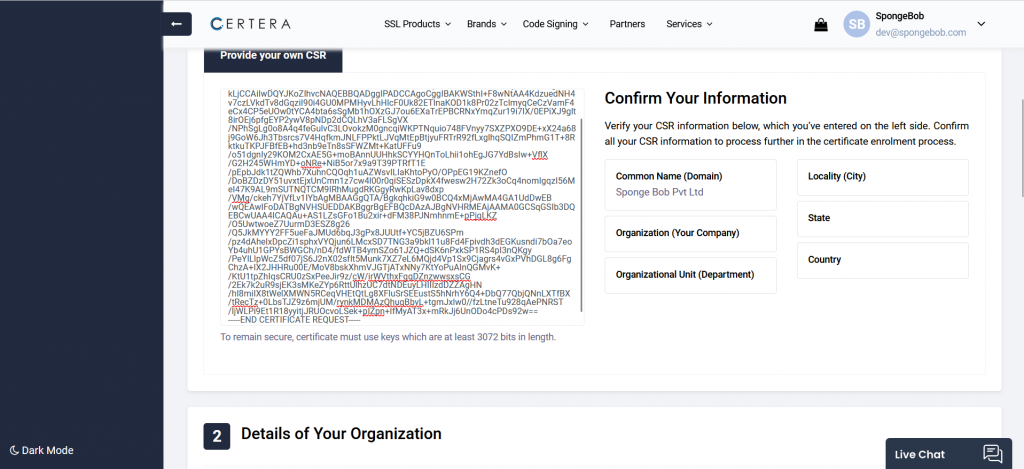
12. Copy your CSR into the specified box, fill in the other necessary fields, and send the order.
13. When the validation process is completed, you will receive an email from CA regarding the Private Key Protection Agreement.
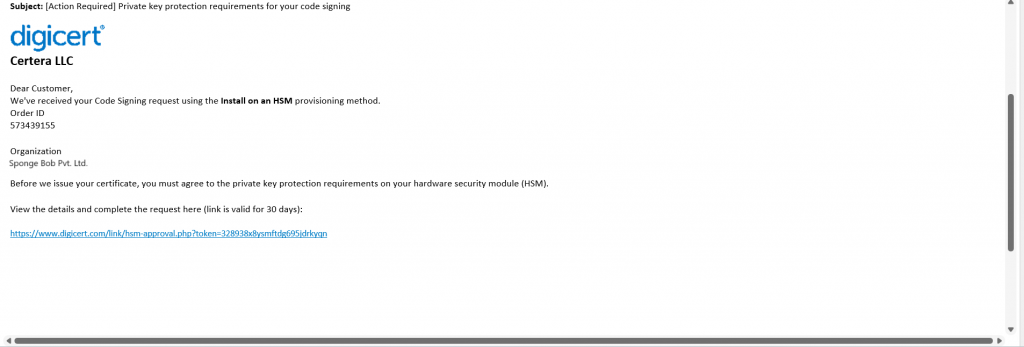
Finally, complete the validation, review the information about your organization, and agree to the private key protection agreement.
14. Contact our tech support team to get the.PEM file after the order is complete.
15. Return to your Azure certificate operation and select Merge Signed Request.
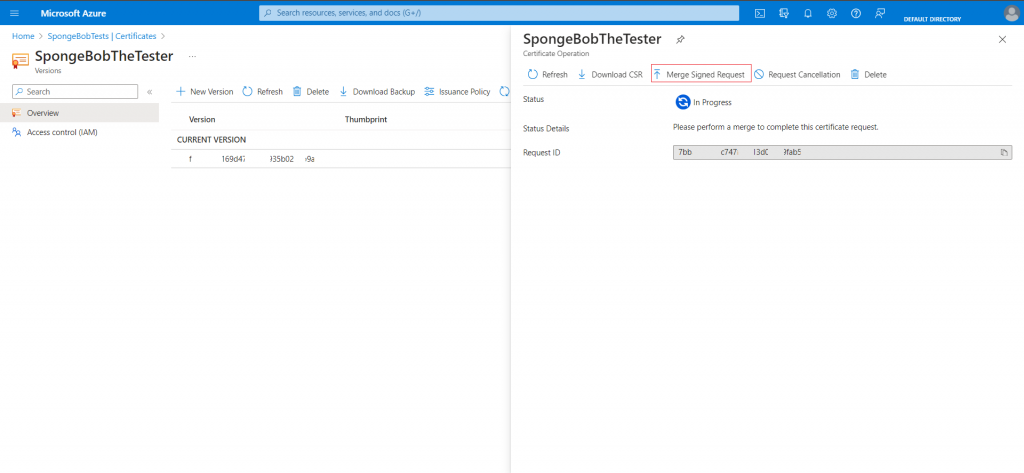
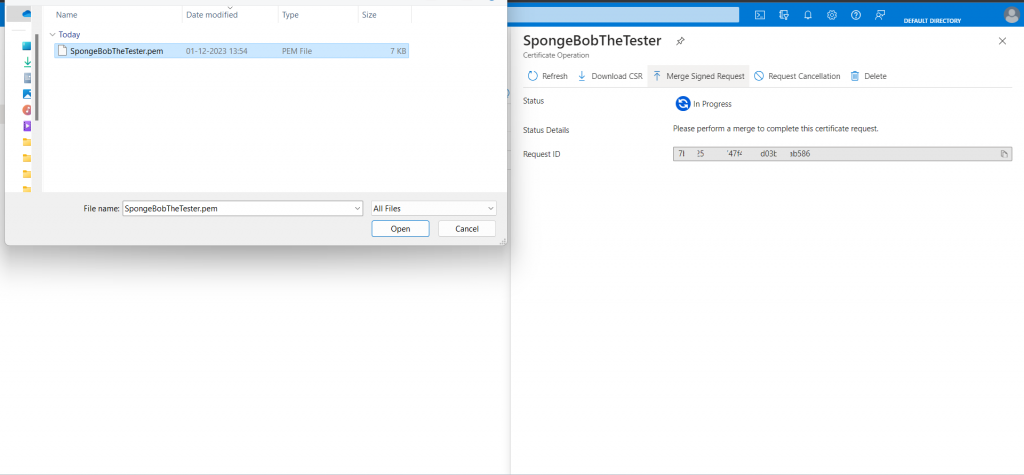
16. Insert the.PEM file there. The status appears to be completed.
Your Code Signing certificate will be available in Azure Key Vault and can be used with the Azure Sign Tool or Azure Pipeline.
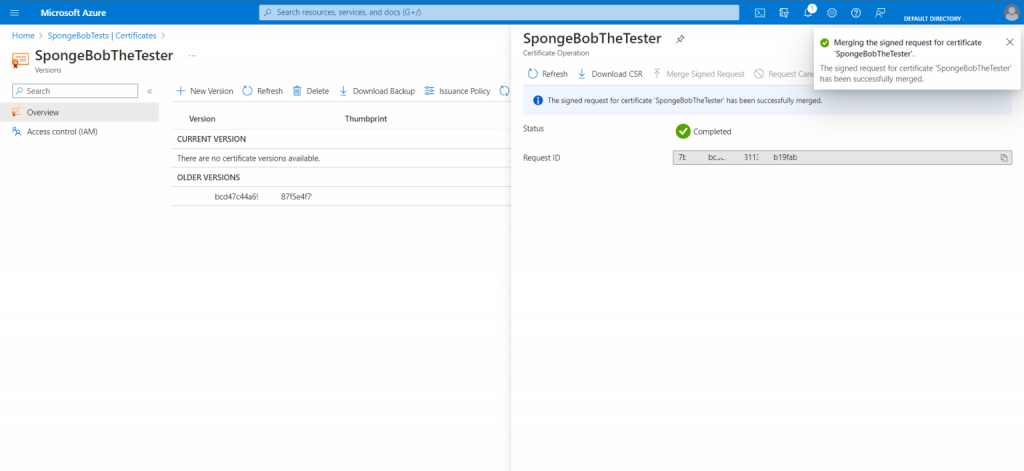
With increased security and confidence, your private key is now securely maintained in the Microsoft Azure KeyVault Cloud HSM.
The above procedures apply to large organizations and small developers. After reading this article, you can use Microsoft Azure KeyVault to manage your keys and certificates.
