How to Fix ERR_CERT_COMMON_NAME_INVALID in Chrome? [SSL Common Name Mismatch Error]
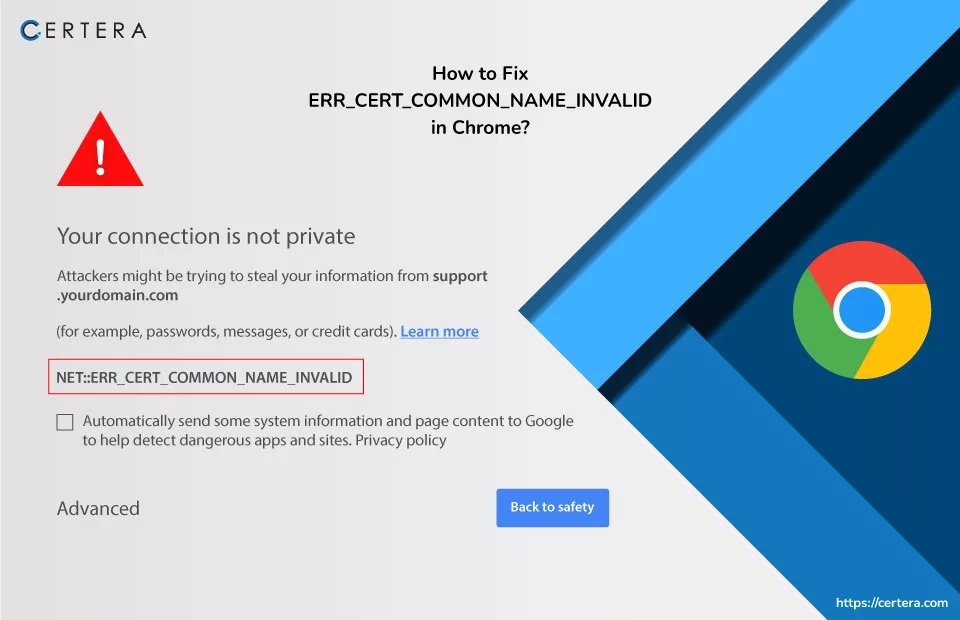
While surfing websites, Encountering an SSL error can be a frustrating hurdle. One such obstacle is the ERR_CERT_COMMON_NAME_INVALID error, commonly known as the SSL Common Name Mismatch Error.
This error arises from a misconfiguration of certificates on a server, and it can disrupt the secure connection between a user and a website. Beyond its technical origins, this error can also be triggered by various factors such as third-party extensions, security programs like antivirus and firewalls, and more.
Often referred to as an SSL connection error, the SSL (Secure Sockets Layer) error materializes when establishing a secure connection with a website’s server. It’s essential to note that this error can stem from inadequately implemented SSL certificates. Consequently, users might be confronted with error messages instead of the expected content when loading a website.
In this guide, we’ll delve deeper into the intricacies of the ERR_CERT_COMMON_NAME_INVALID error, exploring its origins and potential solutions.
Whether it’s due to misconfigured certificates, third-party extensions, or security program interference, understanding the nature of this error is paramount to overcoming it and ensuring a secure and seamless browsing experience.
As shown in the image given below:
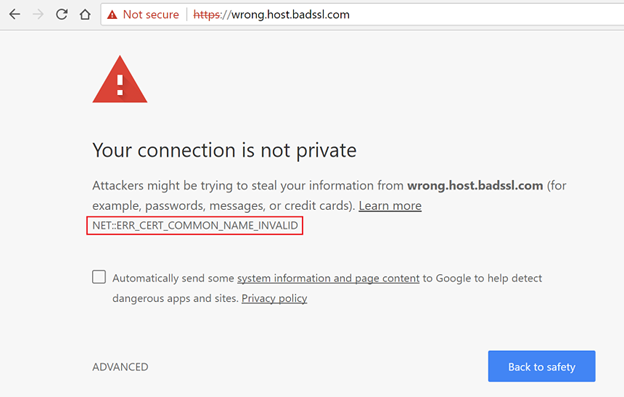
Understanding the Factors Leading to NET::ERR_CERT_COMMON_NAME_INVALID Error
Before delving into the NET::ERR_CERT_COMMON_NAME_INVALID error, let’s know its terminology. The focal point of this error lies in the “common name,” a crucial element in SSL certificates that denotes the domain for which the certificate is issued.
Imagine your website resides at mydomain.com; in this context, the SSL certificate’s common name would be mydomain.com. The crux of the NET::ERR_CERT_COMMON_NAME_INVALID error centers on the fact that the common name indicated by your SSL certificate is somehow deemed invalid.
This error transpires when the name on your certificate doesn’t align with the domain where it’s installed. However, the complexities continue. Various scenarios could trigger this error, including:
Mismatched WWW and Non-WWW Domains:
Your SSL certificate might not cover your domain’s www and non-www versions. Discrepancies between these variations could trigger the error.
Improper HTTPS Transition:
Attempting to switch your website to HTTPS without installing an SSL certificate can lead to this error.
Unrecognized Self-Signed SSL:
The presence of a self-signed SSL certificate, not recognized by your browser as secure, can contribute to the error.
Antivirus Interference:
Antivirus software can inadvertently block your SSL connection, causing this error.
Browser Extension Impact:
Specific browser extensions might interfere with your site’s SSL connection, leading to the error.
Misconfigured Proxy Settings:
Misconfigured proxy settings can also play a role in triggering this error.
Browser Cache and SSL State Issues:
A corrupted browser cache or SSL state can lead to this error, further complicating the troubleshooting process.
Resolving NET::ERR_CERT_COMMON_NAME_INVALID Error Quickly
Encountering the NET::ERR_CERT_COMMON_NAME_INVALID error can be a frustrating experience while browsing the web securely. However, this issue can be successfully resolved by following a few essential steps.
To effectively fix this SSL error, it is crucial to pinpoint the root cause behind it. By identifying the underlying reason for the SSL common name mismatch error, you can implement the techniques provided below to rectify the situation.
Check Date and Time Accuracy:
A surprisingly common reason for encountering the ERR_CERT_COMMON_NAME_INVALID error is an incorrect date and time setting on your computer. A disparity between your system’s clock and time can trigger this error. To rectify this, ensure that your desktop’s date and time are accurately set. By synchronizing your system clock with the official time, you can eliminate this issue and pave the way for secure browsing.
Validate Correct Certificate Installation:
A common cause of SSL common name mismatch is a discrepancy between the domain and the installed certificate. This occurs when the correct certificate is installed but does not encompass the specific web address you are trying to access. This mismatch might arise due to a different certificate being associated with the domain. This situation triggers the “NET: ERR_CERT_COMMON_NAME_INVALID” error. To confirm this, review the “issued to” domain information on the certificate.
Identify Problematic Extensions:
To ascertain whether troublesome browser extensions are causing the error, initiate the Incognito mode in your browser, such as Google Chrome. If the error ceases to appear, it indicates that the extensions might be the culprits. In such cases, it is advised to disable extensions systematically. This can be done by navigating to the extension menu by clicking:
- Three dots
- More Tools
- Extensions
Temporarily disable each extension individually while intermittently checking if the error persists. Once you pinpoint the problematic extension, promptly remove it from your browser to restore error-free browsing.
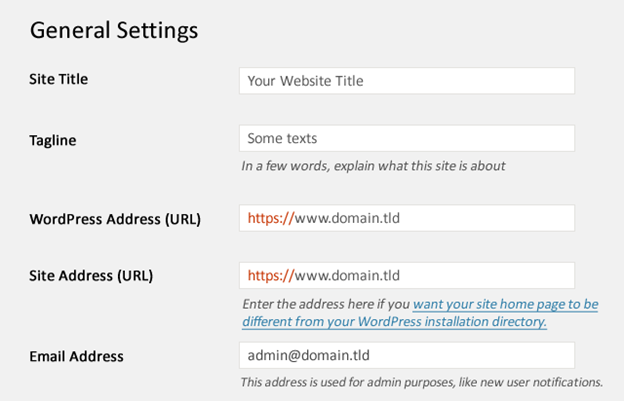
Validate Site Address Protocol:
Occasionally, users might switch their site’s protocol from unsecured HTTP to secure HTTPS out of curiosity. If this change is made without having a valid SSL certificate installed or purchased, it can lead to the “NET: ERR_CERT_COMMON_NAME_INVALID” error. If you’re using a platform like WordPress, ensure you don’t add an “S” to HTTP unless a proper SSL certificate is in place.
In WordPress, navigate to the general settings of your account and confirm the URL protocol. If you’ve unintentionally changed to HTTPS without a valid SSL certificate, reverting to HTTP or acquiring an appropriate certificate can rectify the error.
Clear SSL Cache:
When facing an SSL common name mismatch error, a possible solution is to clear the SSL cache. In Windows, open Internet Properties and navigate to the Content tab. From there, clear the SSL cache to eliminate the error potentially.
If you’re using Chrome, the process involves going to Settings, then Advanced Settings, and clicking “Change Proxy Settings.” Clear the SSL state here, which might rectify the SSL common name mismatch error.
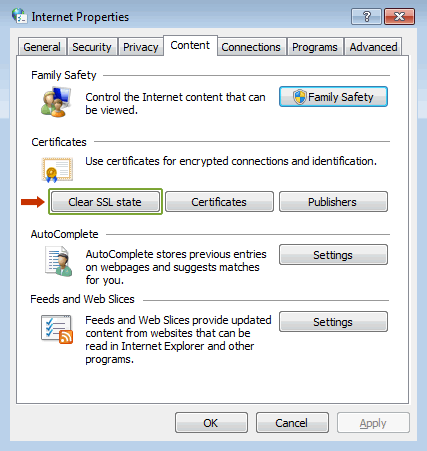
Address Self-Signed Certificates and Domain Mismatches:
Errors can arise when SSL certificates are assigned to the wrong domain or when self-signed certificates are used. Self-signed certificates, typically intended for internal servers, can trigger errors that most browsers don’t consider legitimate.
If you’re experiencing this issue, consult a developer to replace self-signed SSL with a proper SSL certificate aligned with your domain. This step is crucial to resolve the ERR_CERT_COMMON_NAME_INVALID error.
Check Antivirus and Firewall Settings:
Antivirus software or firewalls might block SSL connections, leading to SSL errors. Verify that your antivirus software doesn’t have “https scanning” enabled. If you can’t find this option, consider temporarily disabling the software. This action might help identify whether the antivirus is causing the error.
Review Proxy Settings:
Incorrect proxy settings can lead to browsing issues and trigger SSL errors. Optimize browsing by right-clicking on the Network Access icon. From there, navigate to Internet Properties, which will open the door to a realm of customization. Once inside, focus on the “Connection” tab, which is the key to refining your proxy settings. You’ll find “LAN Settings,” a pivotal checkpoint within this tab.
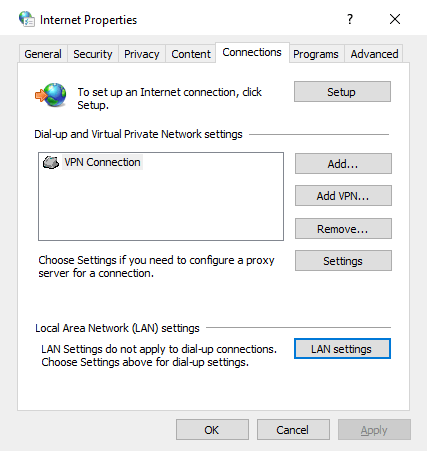
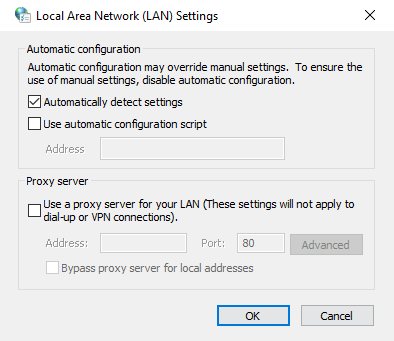
Ensure that your proxy settings are configured to “Automatically detect settings.” Right-click the Network Access icon and access Internet Settings. Navigate to Connections and click on LAN Settings. Check the box for “Automatically detect settings” and confirm with OK. This adjustment could resolve the error and enable seamless website browsing.
Keep OS and Browser Updated:
Outdated browsers and operating systems often contribute to SSL errors. Regularly updating your browser and OS is crucial to avoid such errors. Developers release patches and updates that address security issues, making it essential to keep your software up-to-date. If you’re a website owner, ensure your users are not facing similar errors; if they are, prompt them to update their browsers and operating systems.
Domain and Subdomain Coverage:
Since the error is rooted in a mismatch between the domain and the certificate, it is imperative to ensure that the browsing domain and subdomains are comprehensively covered.
This can be achieved through Subject Alternative Name (SAN) certificates and wildcard certificates. SAN certificates encompass individual domains, while wildcard certificates extend to single-level subdomains.
The error might manifest if you attempt to access a domain or subdomain not covered by your certificate. Hence, verifying the coverage of your certificate is essential for uninterrupted browsing.
Address Redirection and WWW vs. Non-WWW:
Not all SSL certificates inherently cover a website’s non-WWW and WWW versions. Depending on the domain used during the certificate purchase, you might need to manage redirects properly. It’s crucial to ascertain whether your browser is forcefully redirecting users to a different part of the site. If the redirection is in play, configuration adjustments are necessary to remove the redirection.
For instance, consider a scenario where you’ve purchased a wildcard SSL certificate, and the primary domain (e.g., domain.com) redirects to www.subdomain.com. This kind of setup can trigger errors in the browser. In such cases, redirection is required, and obtaining an SSL certificate to cover the redirected traffic is essential to eliminate the error.
Wrapping up
Unveiling the myriad factors contributing to the NET::ERR_CERT_COMMON_NAME_INVALID error highlights its intricate nature. While determining the precise solution might pose a challenge, patience and a systematic approach will undoubtedly guide you toward rectifying this issue.
As you navigate these complexities, you can restore the seamless and secure browsing experience you seek. Following the measures provided in this guide, you can easily overcome the NET::ERR_CERT_COMMON_NAME_INVALID error.
Recommended: What are the Most Common SSL Certificate Errors? How to Fix It?